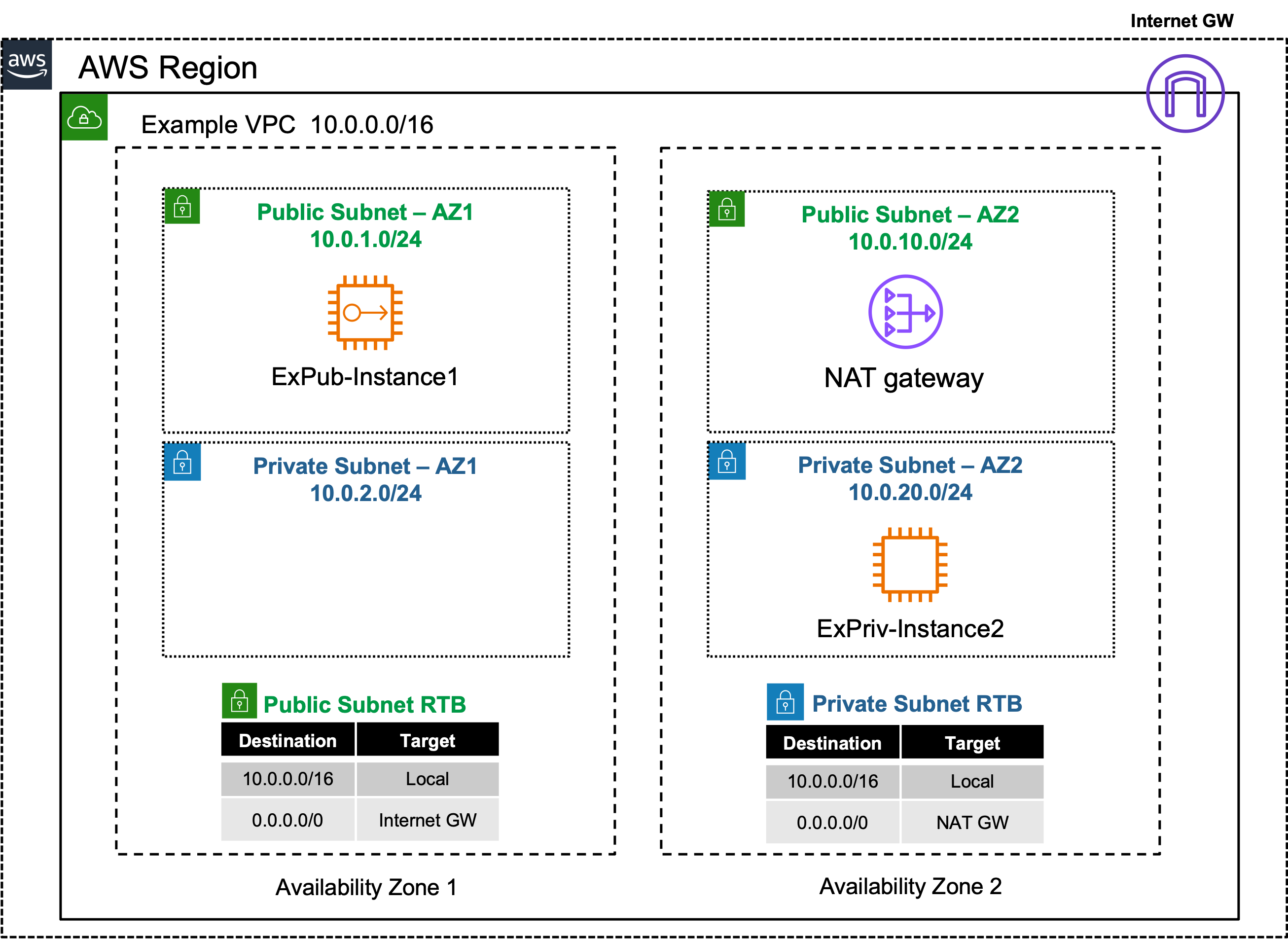
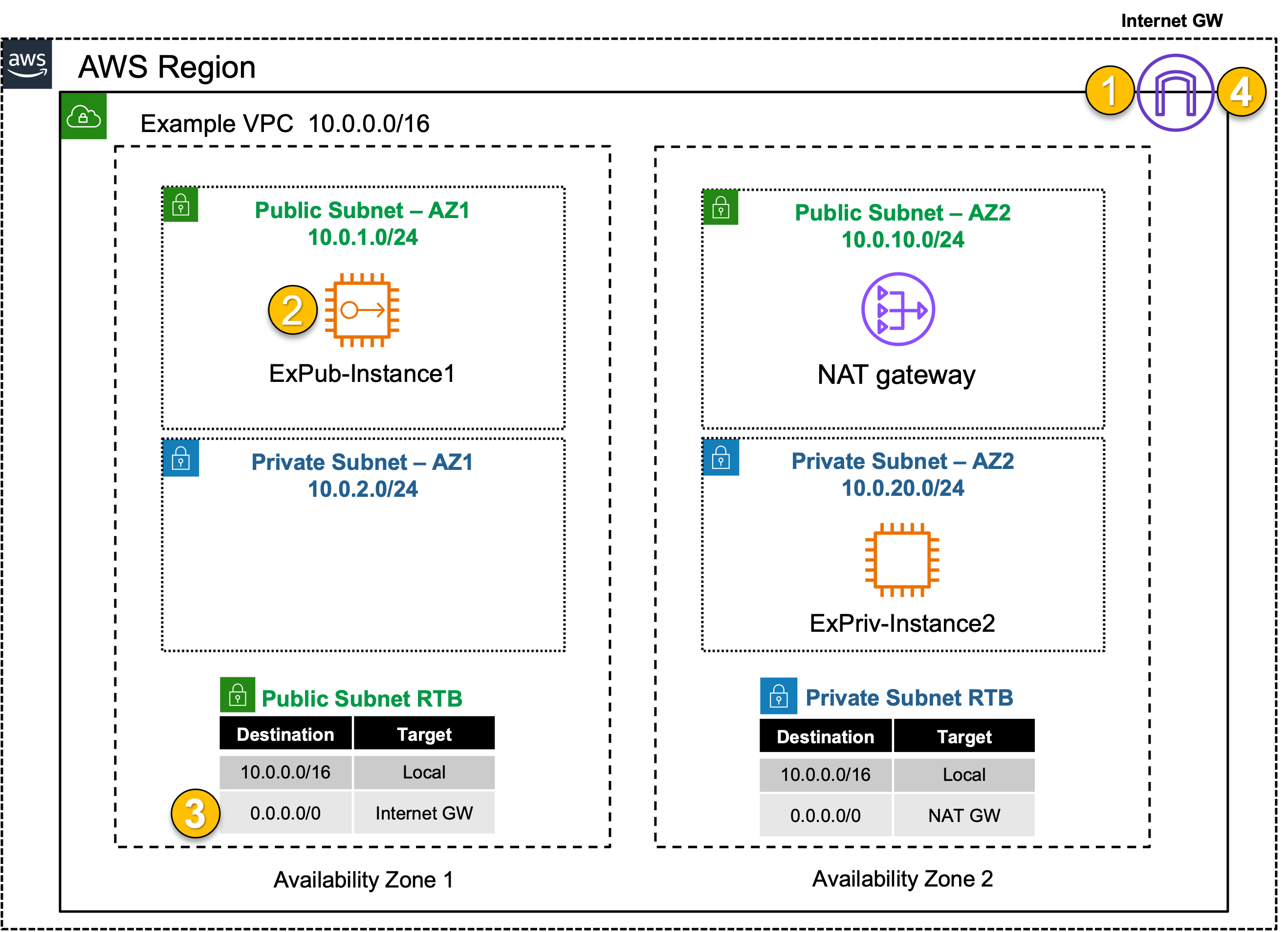
Single VPC & IGW
Public Inbound: Single VPC with IGW
| Goal | Establish Internet access for EC2 Public instance (inbound + outbound). |
| Task | Adjust the route table associations so you can ping ExPub-Instance1. |
| Verify task completion | Confirm inbound VPC connectivity to EC2 Instance via Ping the EC2 Public instance from your laptop/workstation |
Warning
There are no security controls in this example. ExPub-Instance1 can freely communicate with the Internet and anybody on the Internet can reach ExPub-Instance1.
Summarized Steps (click to expand each for details)
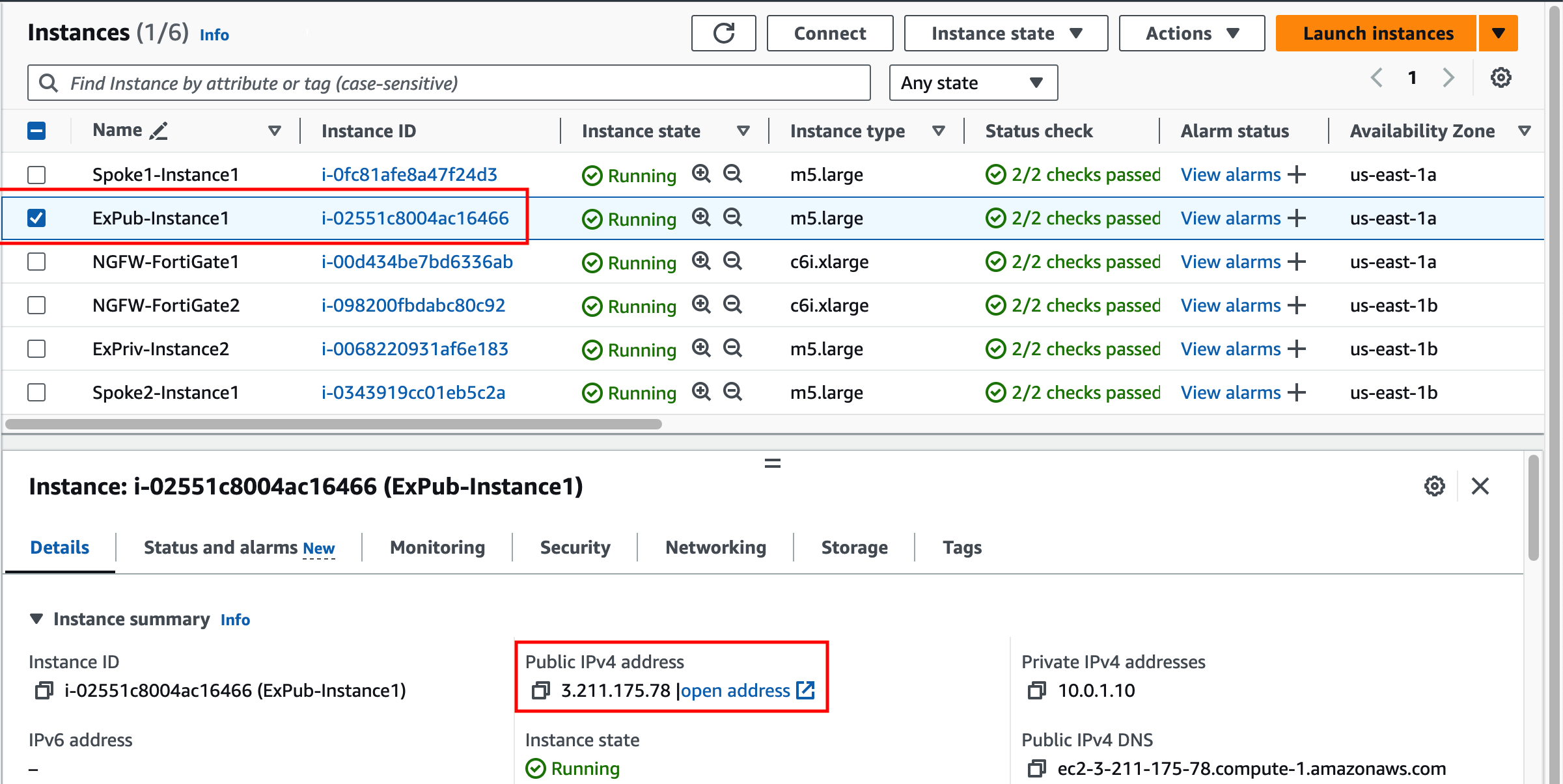
Find the EC2 Instance Public IP and verify it’s currently inaccessible.
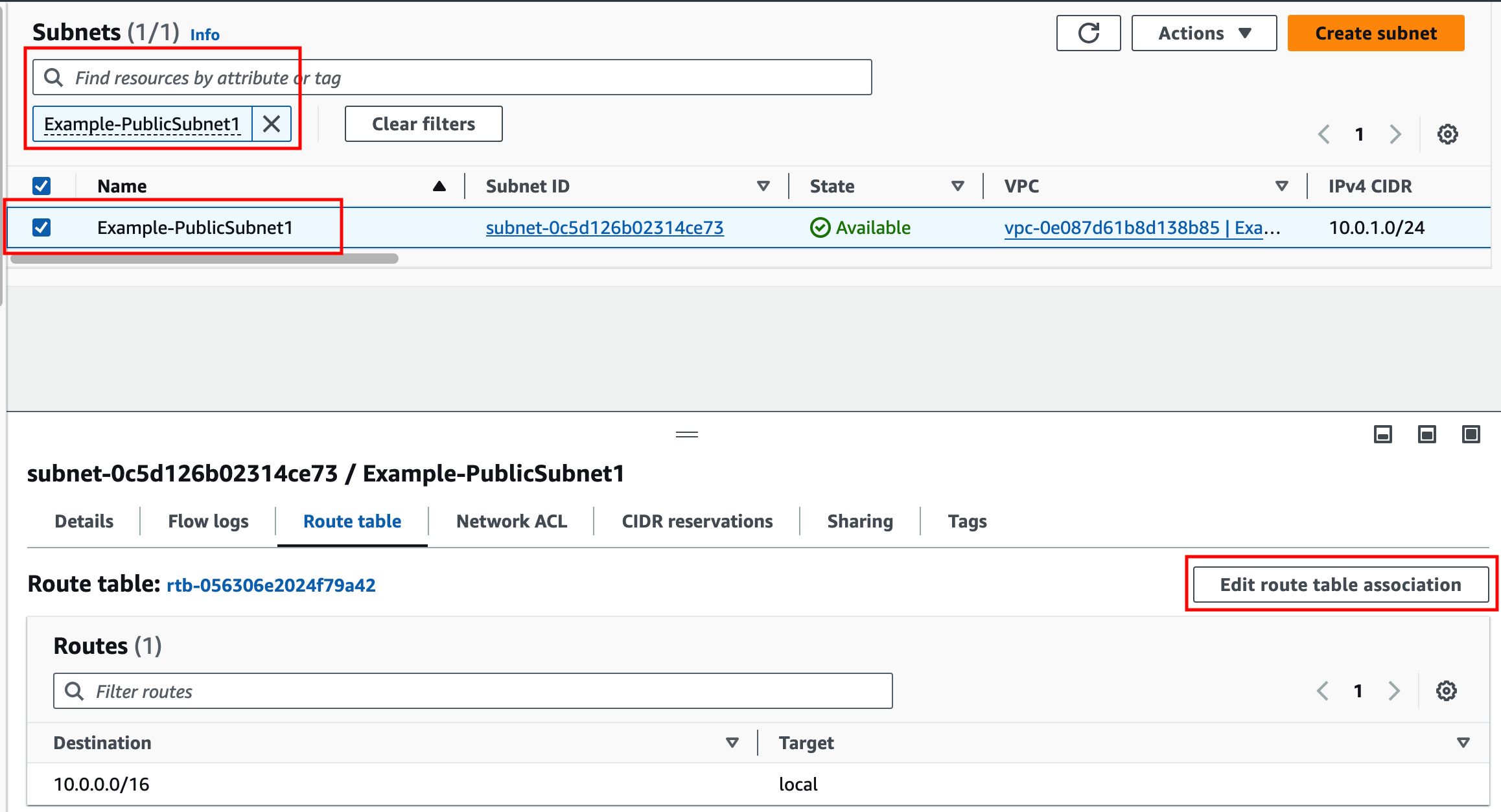
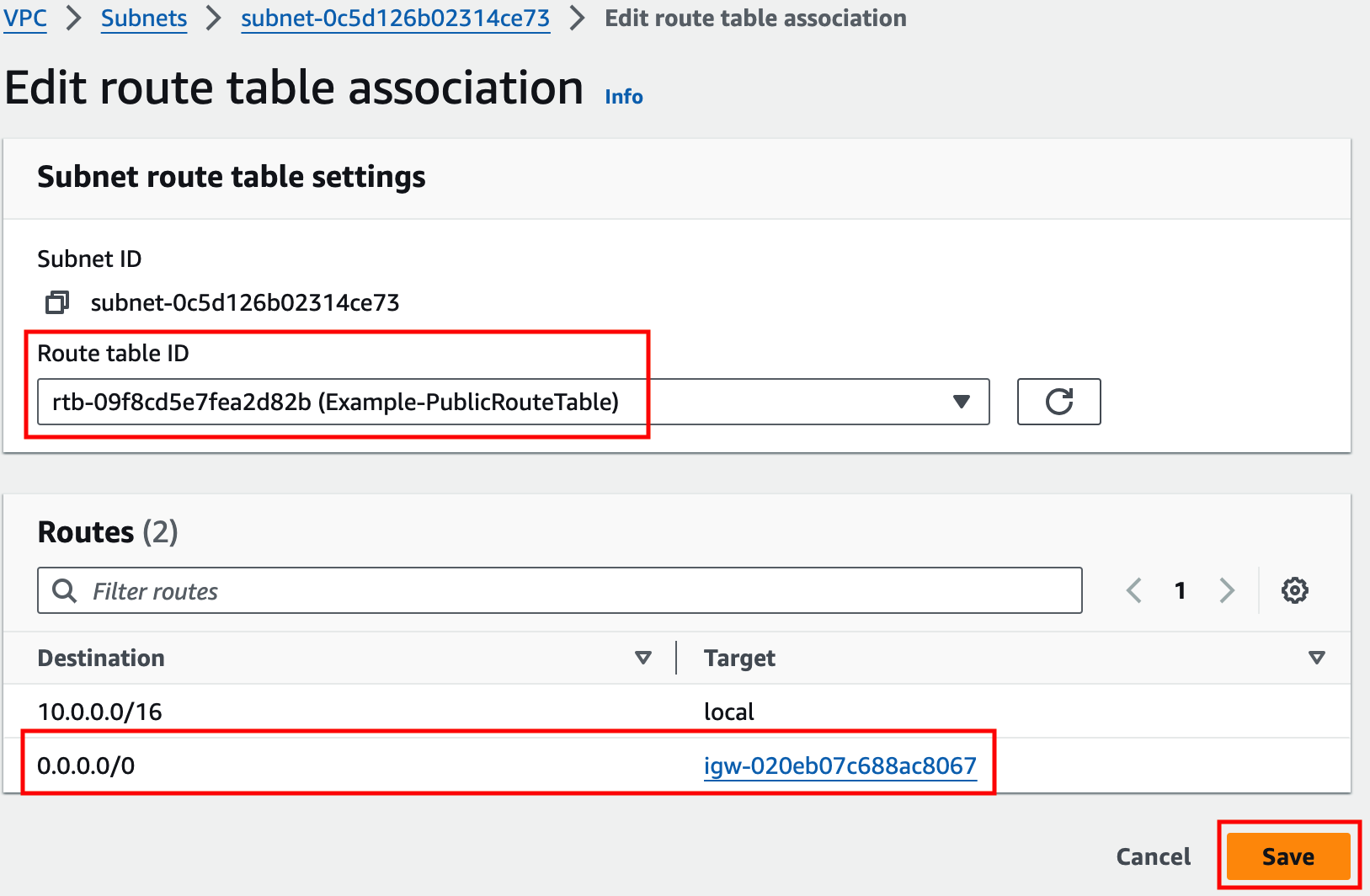
Identify the route table and examine routes, then associate the route table to the proper subnet.
Verify communication to the EC2 Instance Public IP.
Let’s dig deeper to understand how all of this works.
- IGW implicit NAT on EC2 EIP’s.
Discussion Points
- EC2 instances can be assigned an EIP for public reachability.
- VPC’s must have an IGW associated to provide Internet access to any subnet in the VPC.
- Subnets have a default RTB associated to them upon creation, allowing default reachability between all subnets in the VPC.
- You can create additional RTBs within a VPC, and then associate each RTB to one or more subnets, altering the routing behavior of ALL TRAFFIC within that subnet.
- This is a very basic setup and is often used as a “hello world” demo for intro to cloud.
- Without any additional actions taken, this EC2 instance is wide open to the Internet, meaning it can communicate freely to anywhere on the Internet and anybody on the Internet can communicate freely to it. As we’ll see later, there are already inbound probing attempts against this instance even though it was just launched in the last 30 minutes.
This concludes this task