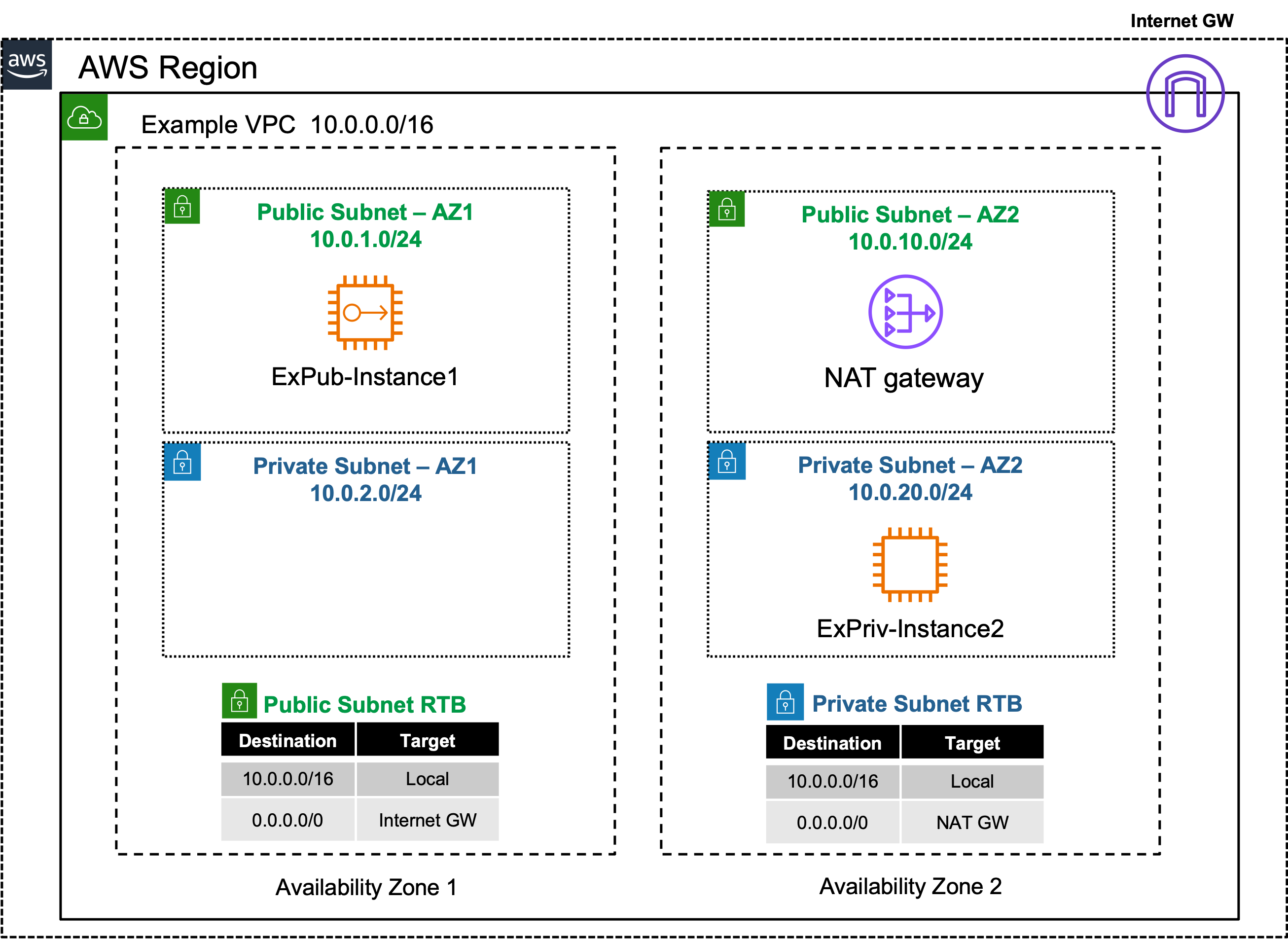
Single VPC & NATGW
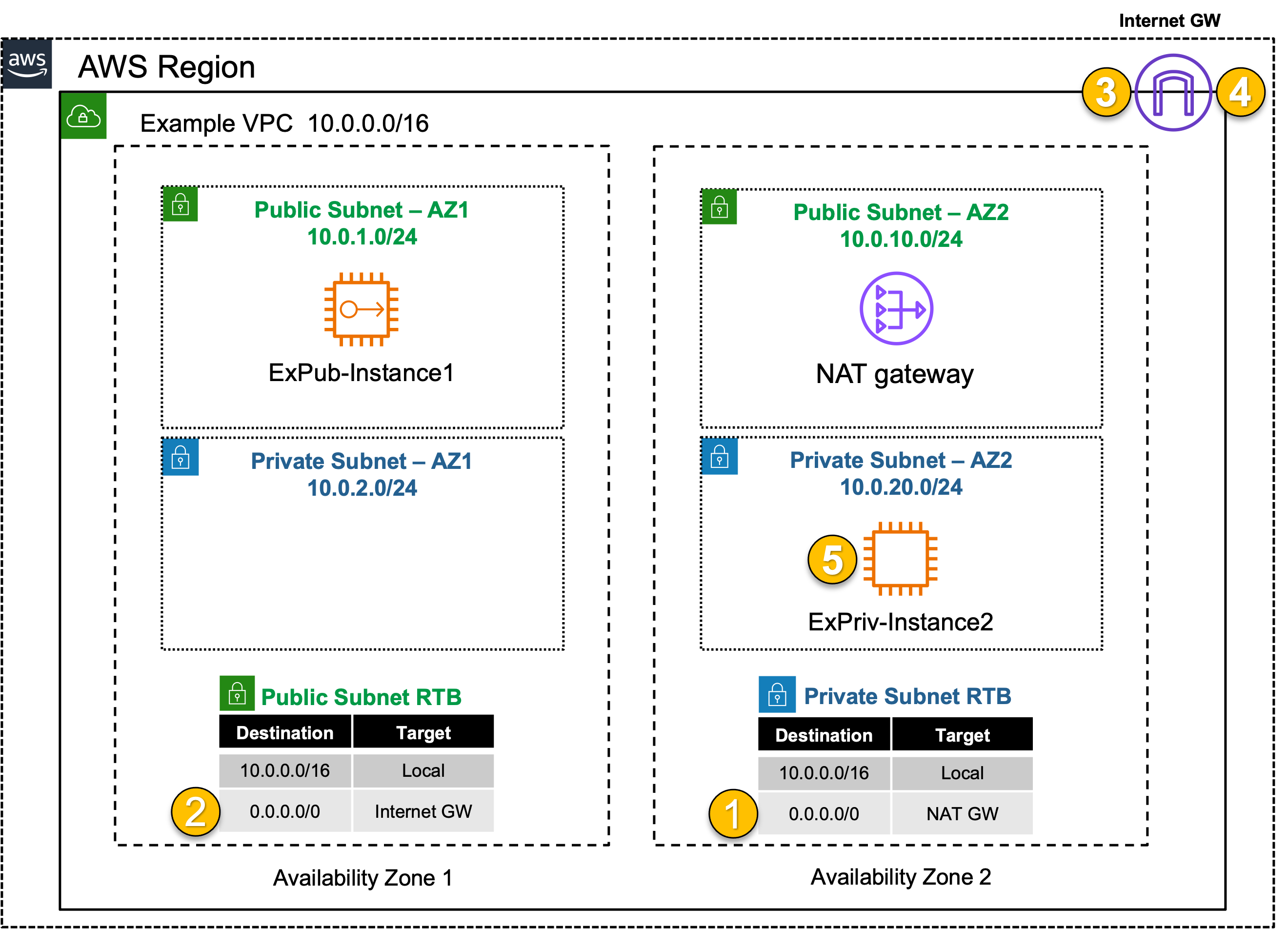
Private Outbound: Single VPC with NATGW
| Goal | Establish outbound only Internet access for EC2 Private instance. |
| Task | Adjust the route table associations so ExPriv-Instance1 can reach the Internet. |
| Verify task completion | Confirm outbound VPC connectivity from EC2 Instance via Ping to Internet from the EC2 instance |
Warning
There are no security controls in this example. However, NATGW is a 1-way service, only allowing connectivity outbound. While ExPriv-Instance2 can freely browse the Internet (outbound), no Internet hosts can connect to it (inbound).
Summarized Steps (click to expand each for details)
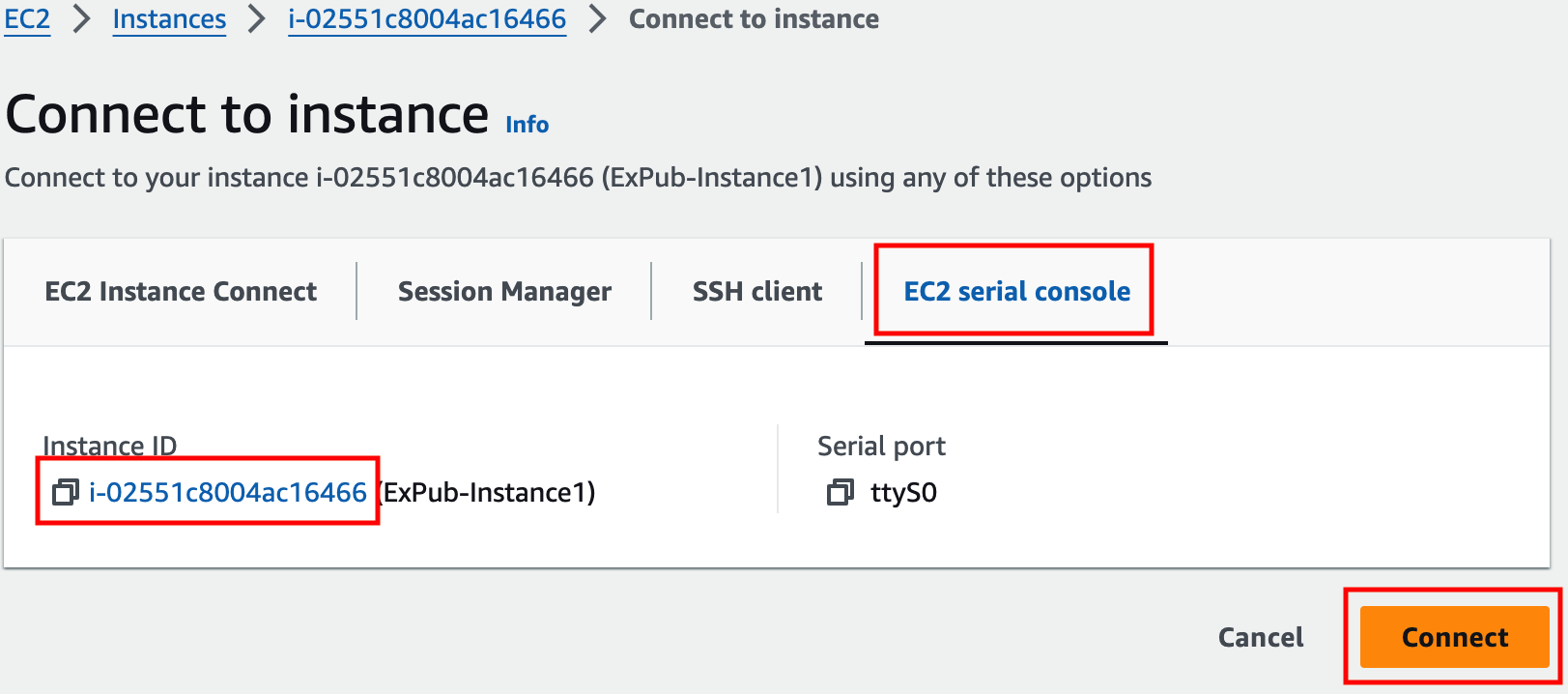
Login to ExPriv-Instance2 and verify it cannot access the Internet.
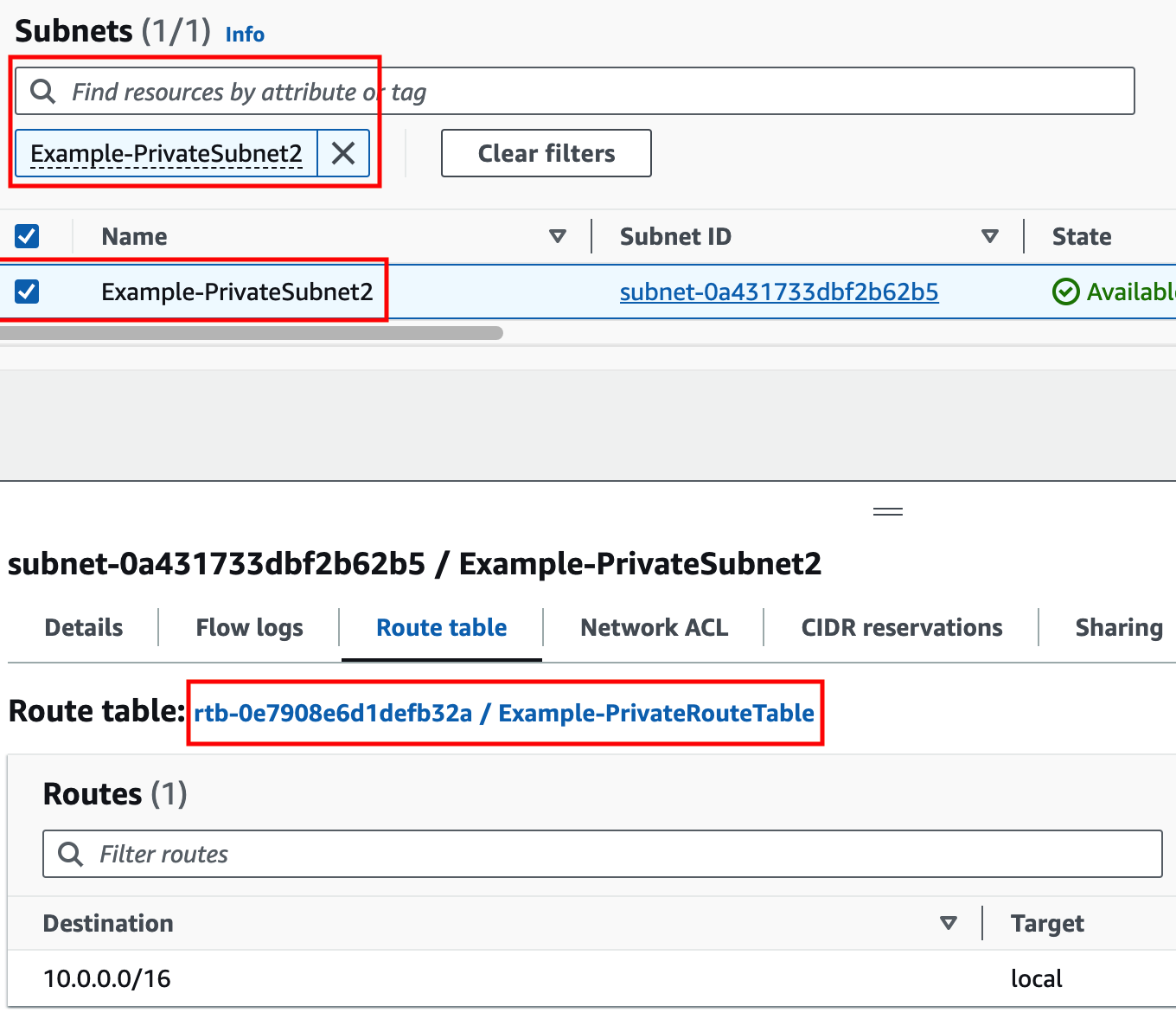
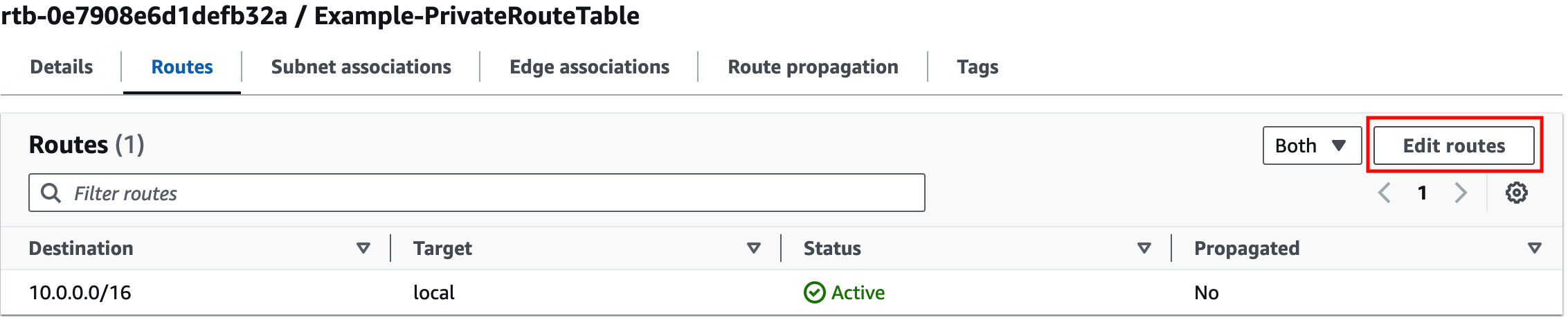
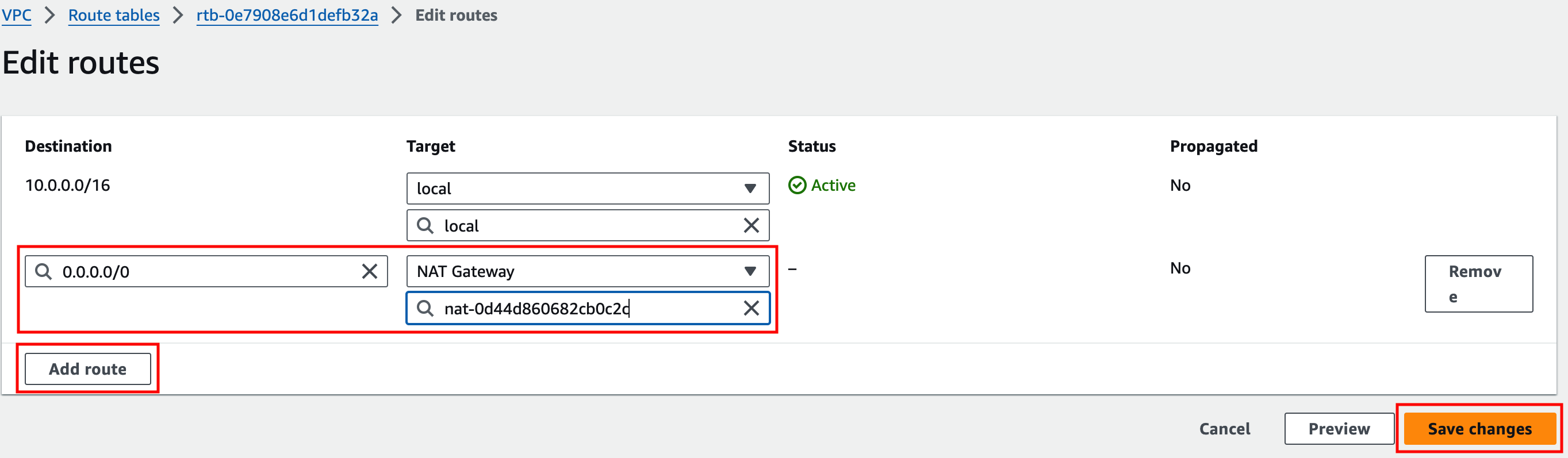
Identify the relevant route table and add the proper route so 0.0.0.0/0 traffic is sent to NATGW.
Test Internet connectivity from ExPriv-Instance2 again.
Let’s dig deeper to understand how all of this works.
Discussion Points
- NAT GW providing many to 1 NAT, for outbound only.
- No internal reachability via NATGW, so no inbound probes seen on any of the private instances.
- General best practice, though thoroughly insufficient for overall security principles.
This concludes this task