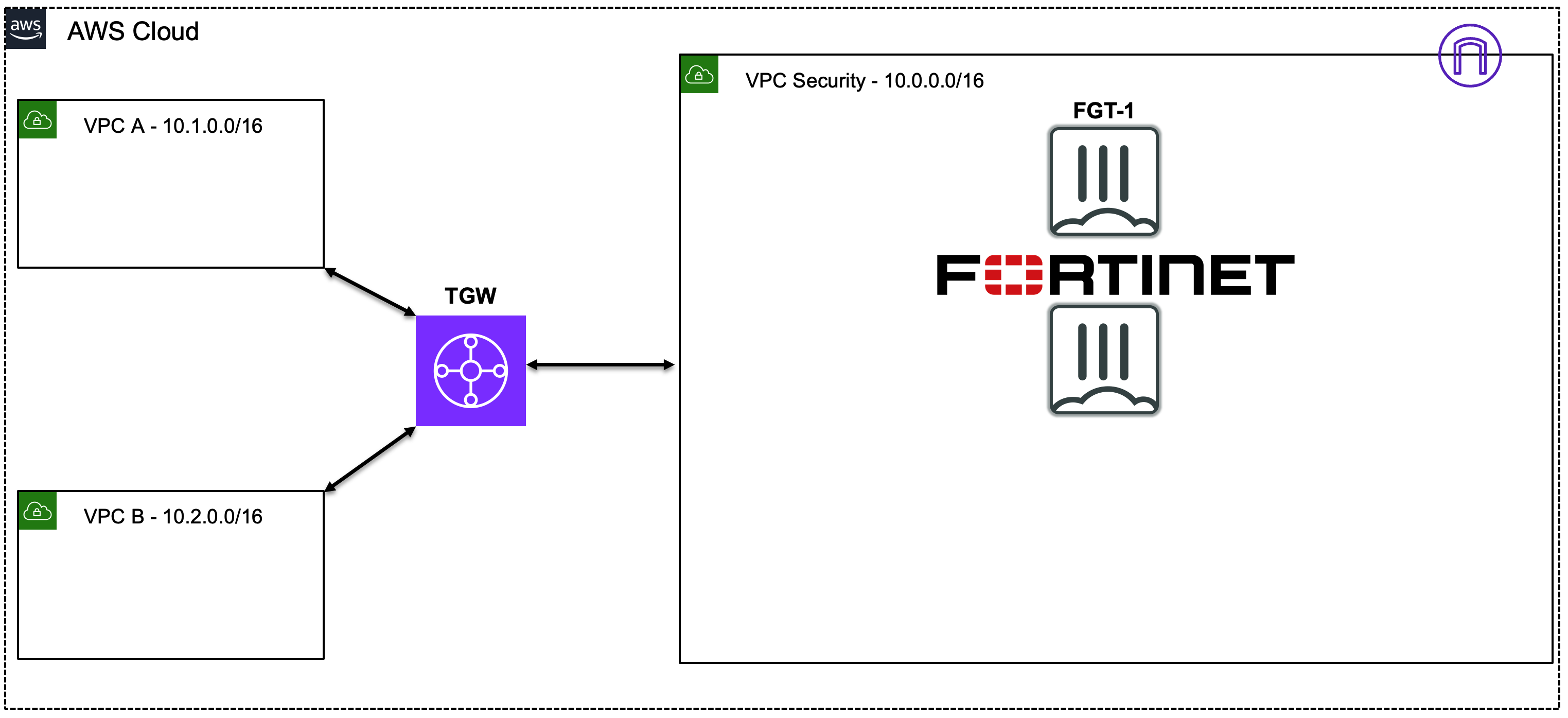
| 1 | Spoke1-Instance1 -> 0.0.0.0/0 TGW | Spoke1-Instance1 sends east/west traffic to the VPC router (its default gw) which routes traffic to TGW as configured in the Spoke1 VPC RTB. | 10.1.2.10:src-port -> 10.2.20.10:80 |
| 2 | Spoke1-TGW-Attachment -> 0.0.0.0/0 Sec-TGW-Attachment | Spoke1-TGW-attachment is associated to the Spoke VPC TGW RTB. This TGW RTB has a default route to Sec-TGW-Attachment, so traffic is forwarded there. | 10.1.2.10:src-port -> 10.2.20.10:80 |
| 3 | Sec-TGW-Attachment -> 0.0.0.0/0 FGT1-Port2 | Sec-TGW-Attachment is attached to the Security VPC TGW Attach Subnets which have a default route to primary FortiGate1 Port2, private interface. | 10.1.2.10:src-port -> 10.2.20.10:80 |
| 4 | FGT1-Port2 -> 0.0.0.0/0 TGW | FGT1 sends inspected & allowed traffic to the VPC router (10.0.0.0/8 static route out port2) via Port2, which routes traffic to the TGW as configured in the Private Subnet VPC RTB. | 10.1.2.10:src-port -> 10.2.20.10:80 |
| 5 | Sec-TGW-Attachment -> 10.2.0.0/16 Spoke2-TGW-Attachment | Sec-TGW-Attachment is associated to the Sec VPC TGW RTB. This TGW RTB has a route for Spoke2 VPC via Spoke2-TGW-Attachment, so traffic is forwarded there. | 10.1.2.10:src-port -> 10.2.20.10:80 |
| 6 | Spoke2-TGW-Attachment -> Spoke2-Instance1 | Spoke2-TGW-Attachment is attached to subnets in Spoke2 VPC which have a local VPC route to reach Spoke2-Instance1. | 10.1.2.10:src-port -> 10.2.20.10:80 |
| 7 | Spoke2-Instance1 -> 0.0.0.0/0 TGW | Spoke2-Instance1 sends reply traffic to the VPC router (its default gw) which routes traffic to TGW as configured in the Spoke1 VPC RTB. | 10.2.20.10:80 -> 10.1.2.10:dst-port |
| 8 | Spoke2-TGW-Attachment -> 0.0.0.0/0 Sec-TGW-Attachment | Spoke2-TGW-attachment is associated to the Spoke VPC TGW RTB. This TGW RTB has a default route to Sec-TGW-Attachment, so traffic is forwarded there. | 10.2.20.10:80 -> 10.1.2.10:dst-port |
| 9 | Sec-TGW-Attachment -> 0.0.0.0/0 FGT1-Port2 | Sec-TGW-Attachment is attached to the Security VPC TGW Attach Subnets which have a default route to primary FortiGate1 Port2, private interface. | 10.2.20.10:80 -> 10.1.2.10:dst-port |
| 10 | FGT1-Port2 -> 0.0.0.0/0 TGW | FGT1 sends inspected & allowed traffic to the VPC router (10.0.0.0/8 static route out port2) via Port2, which routes traffic to the TGW as configured in the Private Subnet VPC RTB. | 10.2.20.10:80 -> 10.1.2.10:dst-port |
| 11 | Sec-TGW-Attachment -> 10.1.0.0/16 Spoke1-TGW-Attachment | Sec-TGW-Attachment is associated to the Sec VPC TGW RTB. This TGW RTB has a route for Spoke1 VPC via Spoke1-TGW-Attachment, so traffic is forwarded there. | 10.2.20.10:80 -> 10.1.2.10:dst-port |
| 12 | Spoke1-TGW-Attachment -> Spoke1-Instance1 | Spoke1-TGW-Attachment is attached to subnets in Spoke1 VPC which have a local VPC route to reach Spoke1-Instance1. | 10.2.20.10:80 -> 10.1.2.10:dst-port |