VPC Peering
| Goal | Establish point to point access from VPC A to VPC B |
| Task | Create a peering connection and VPC routes so EC2 Instance-A can ping Instance-B |
| Validation | Confirm point to point VPC connectivity with ping from EC2 Instance-A to B and Instance-B to C |
Introduction
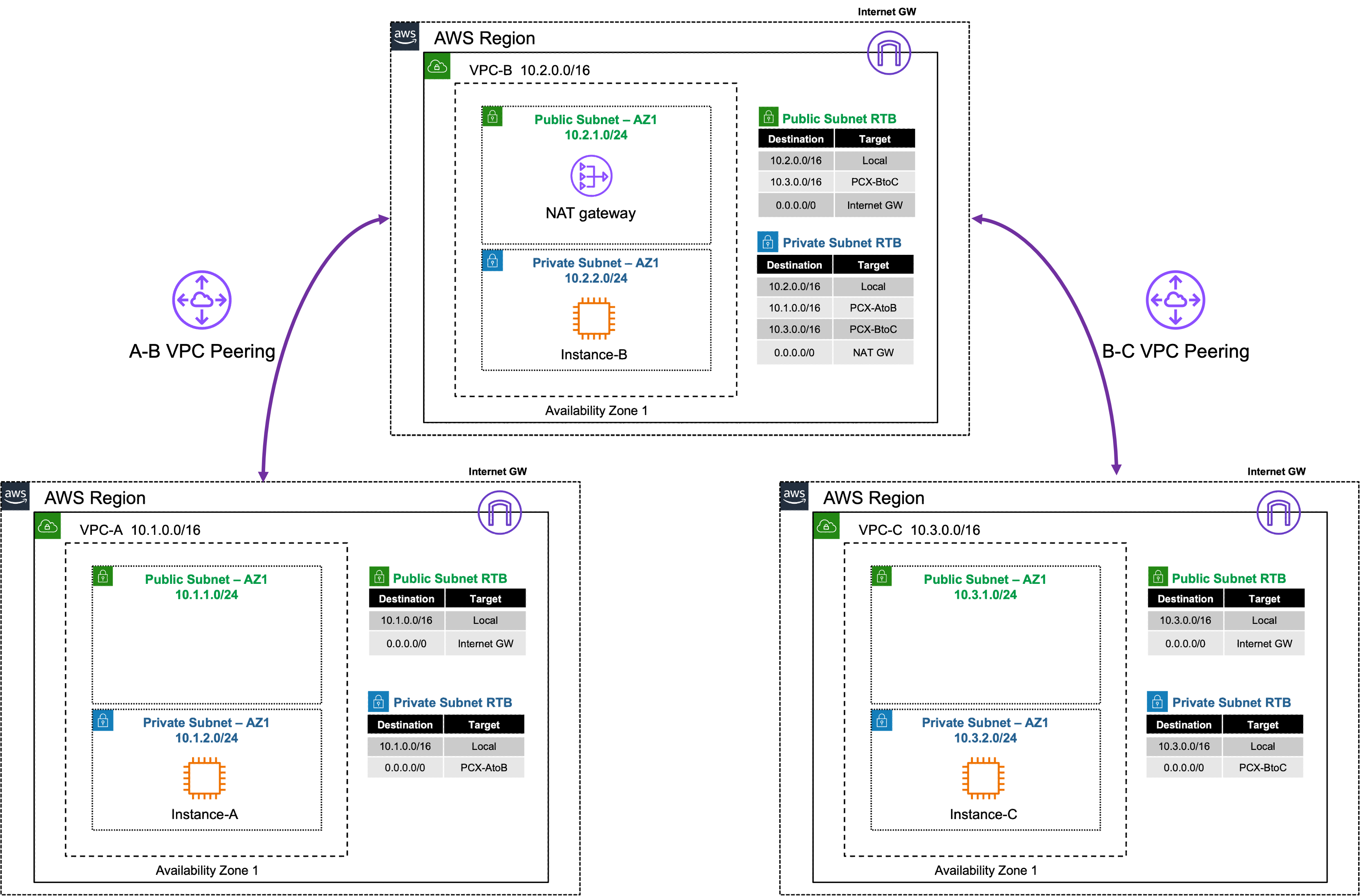
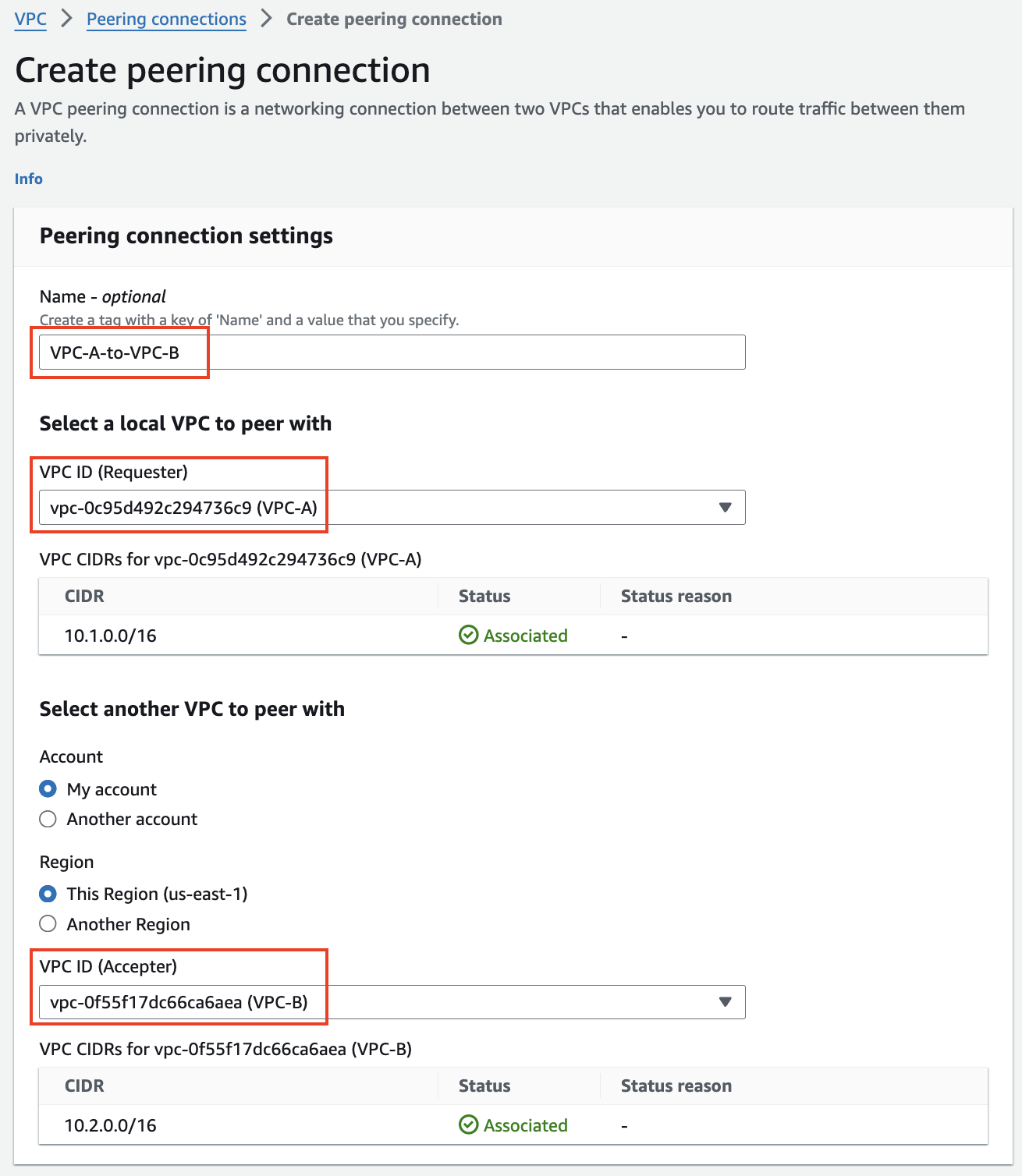
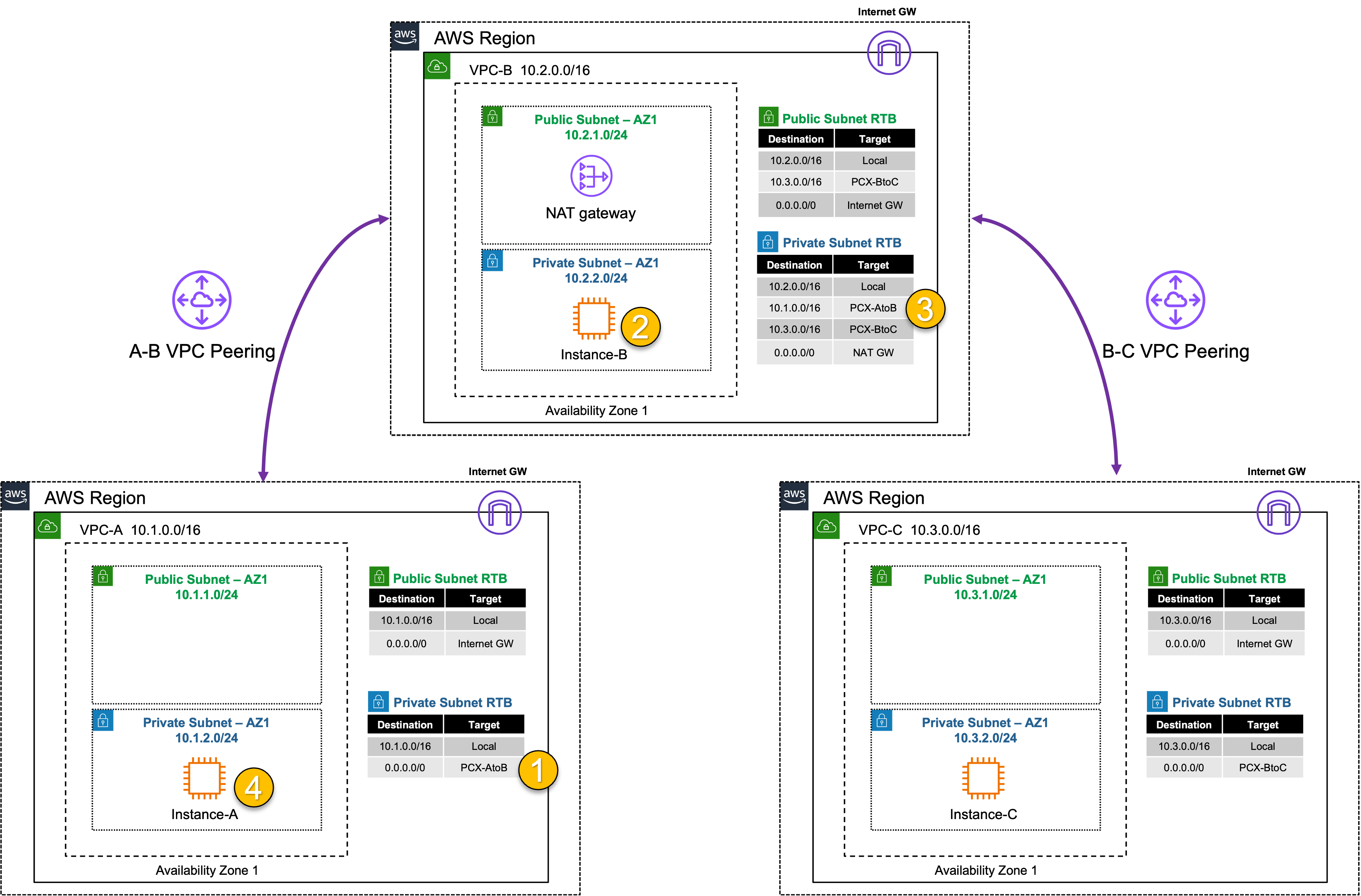
In this task, there are multiple VPCs in the same region that have one instance each. VPC peering and the appropriate VPC routes are already configured for VPC-B to VPC-C. VPC peering and VPC routes will need to be configured between VPC-A and VPC-B. Then traffic will be tested to confirm what traffic routing is and is not supported with VPC peering.
Warning
There are no security controls in this example. Instance-B can freely communicate with the Internet.
Summarized Steps (click to expand each for details)
0) Lab environment setup
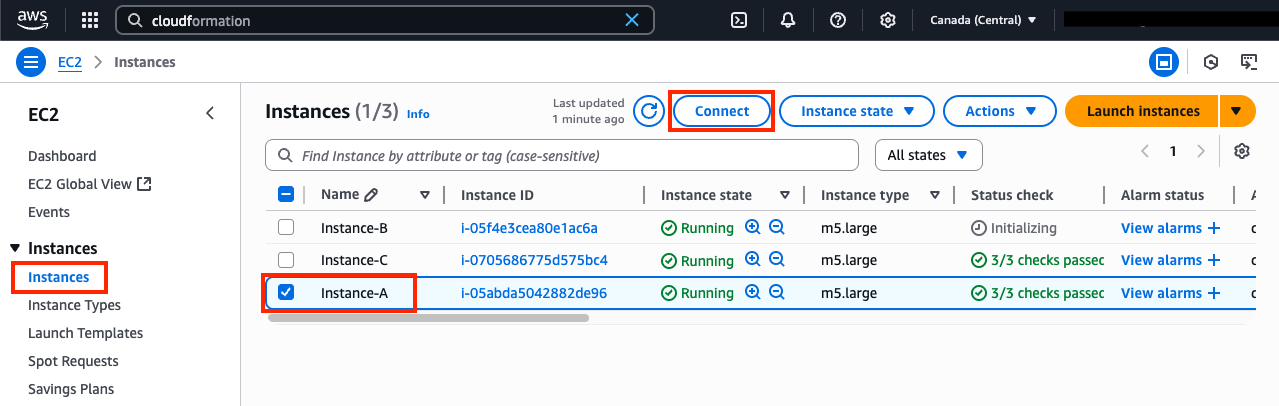
1) Find EC2 Instance-A and verify it can’t access Instance-B or C
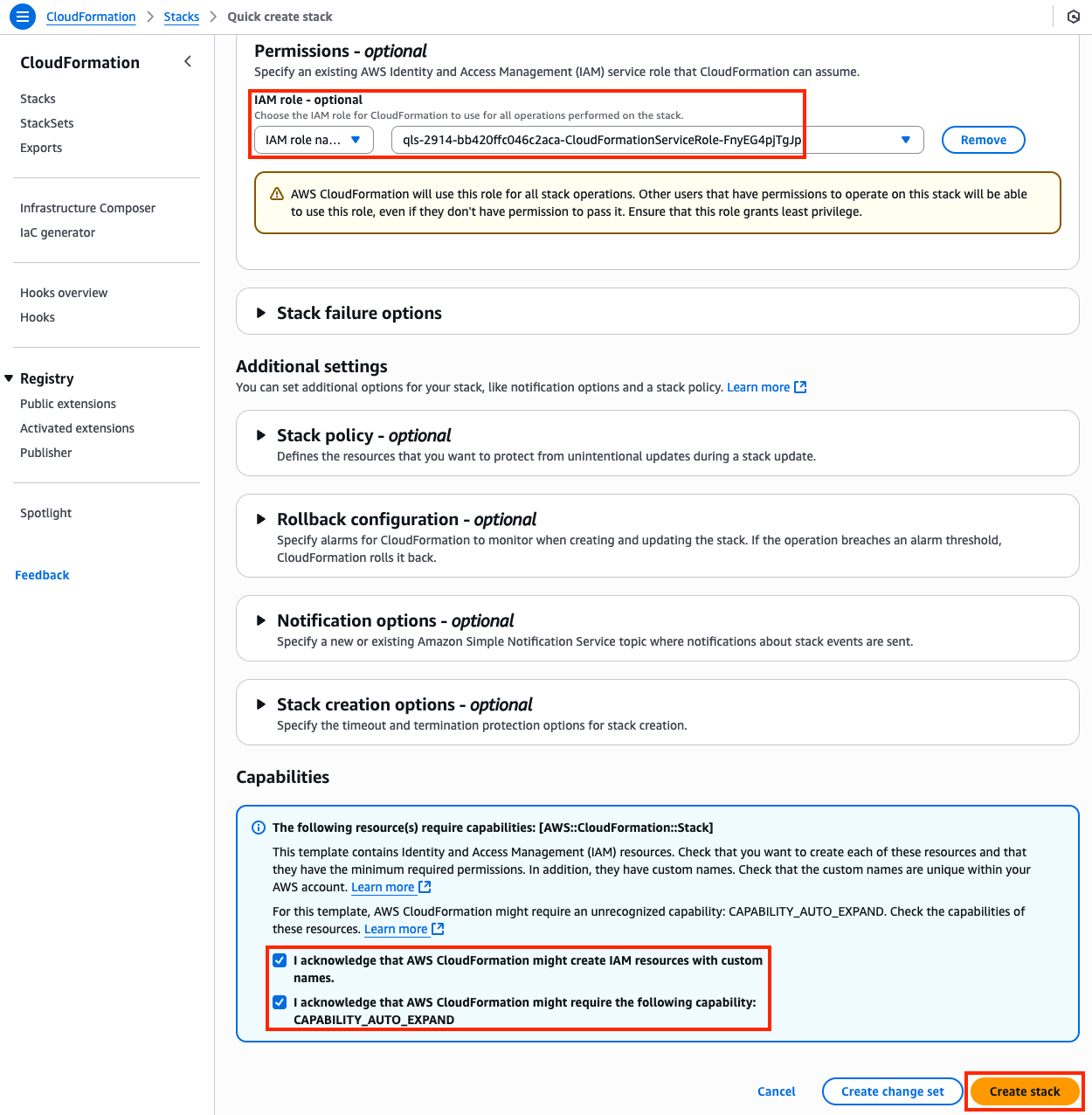
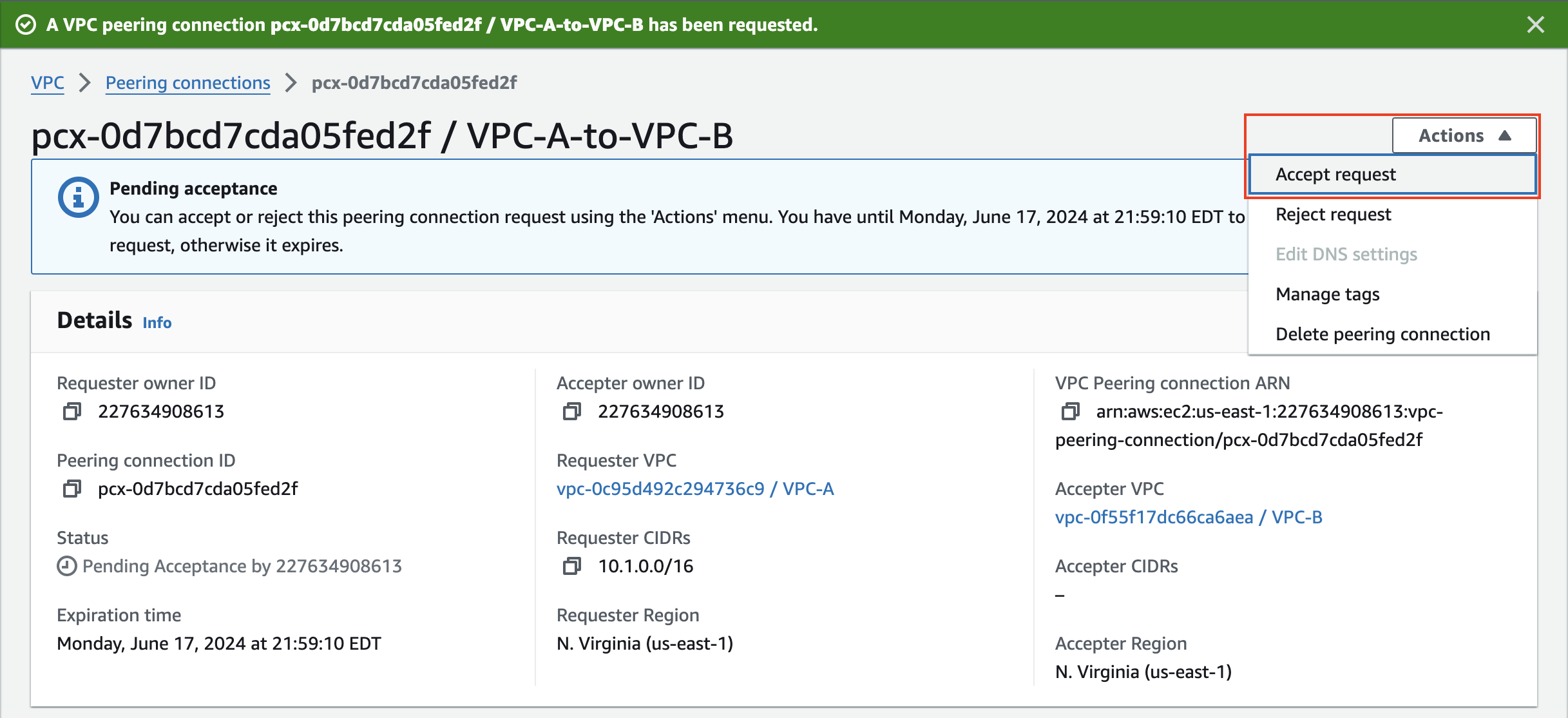
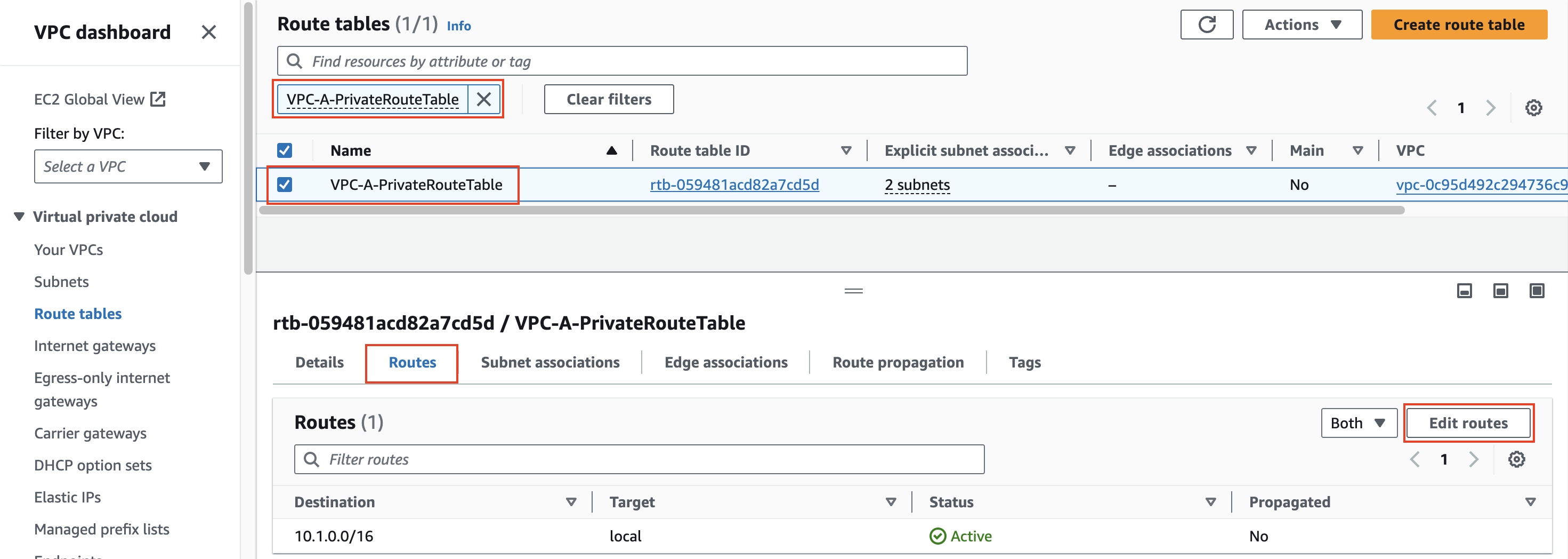
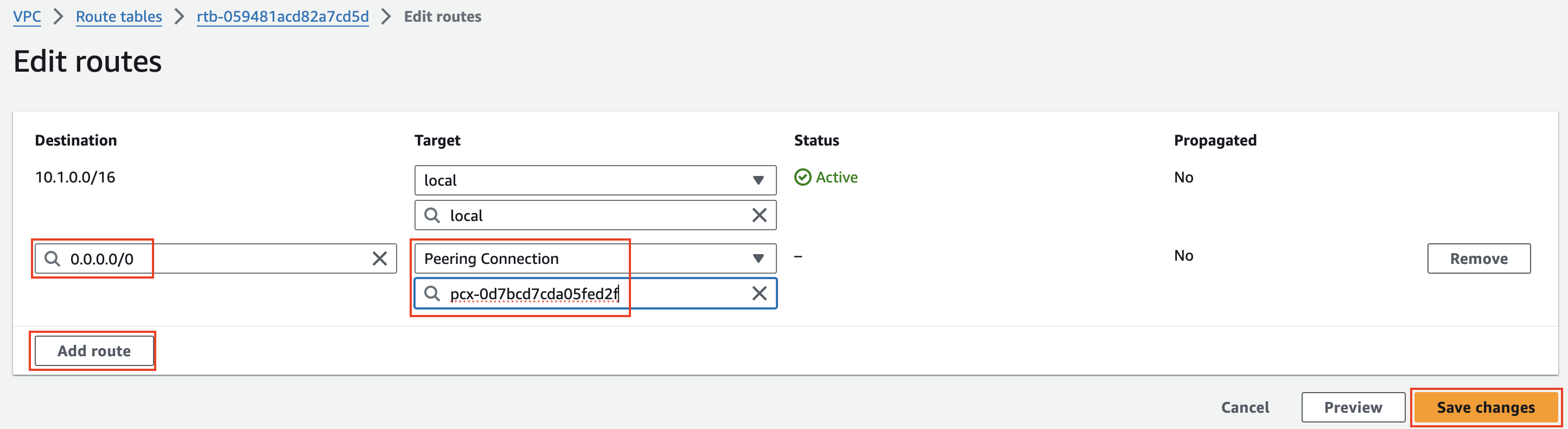
2) Create a VPC peering connection and VPC routes to allow Instance-A in VPC-A to reach Instance-B in VPC-B
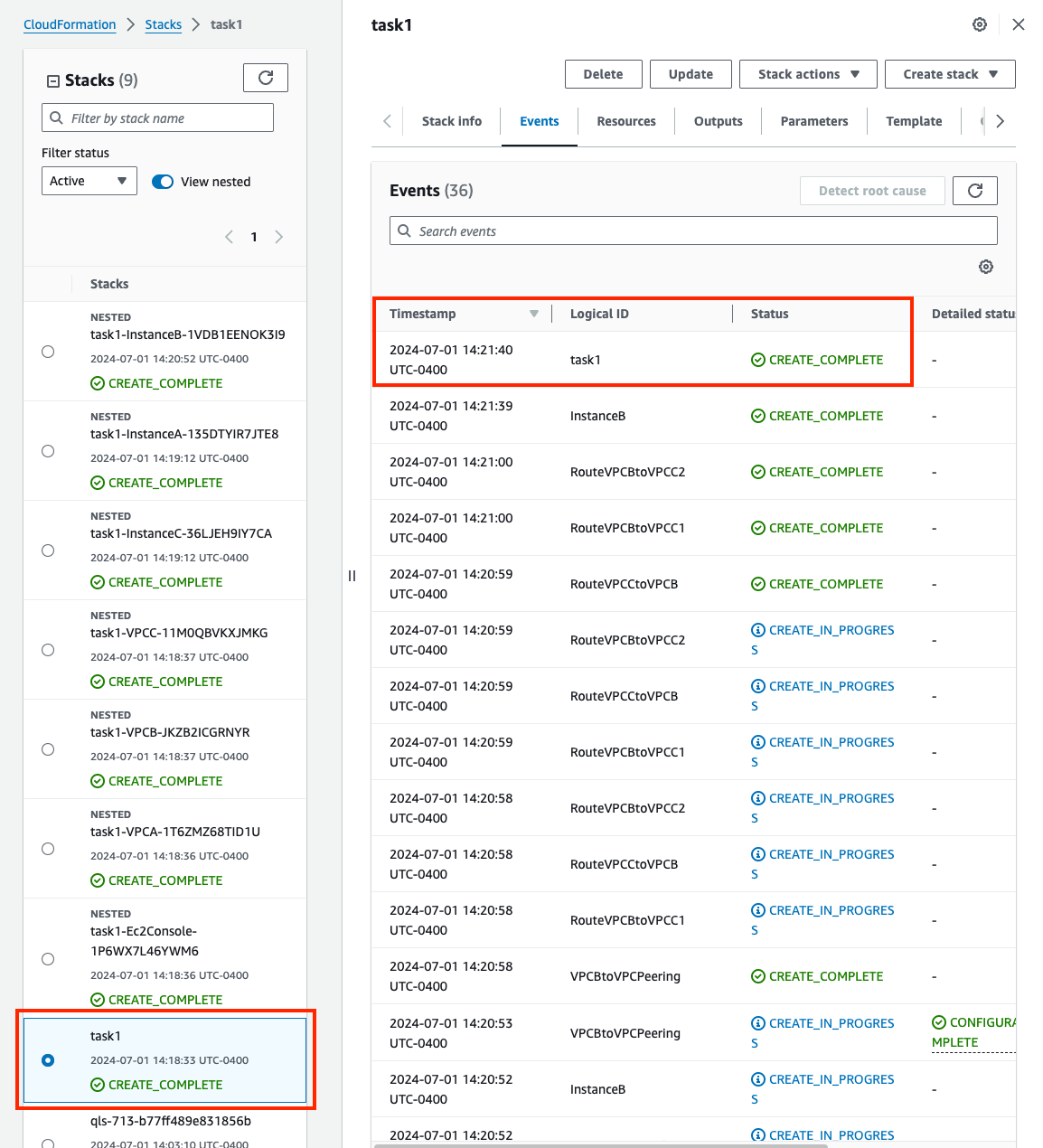
3) Verify communication over the VPC Peering connection
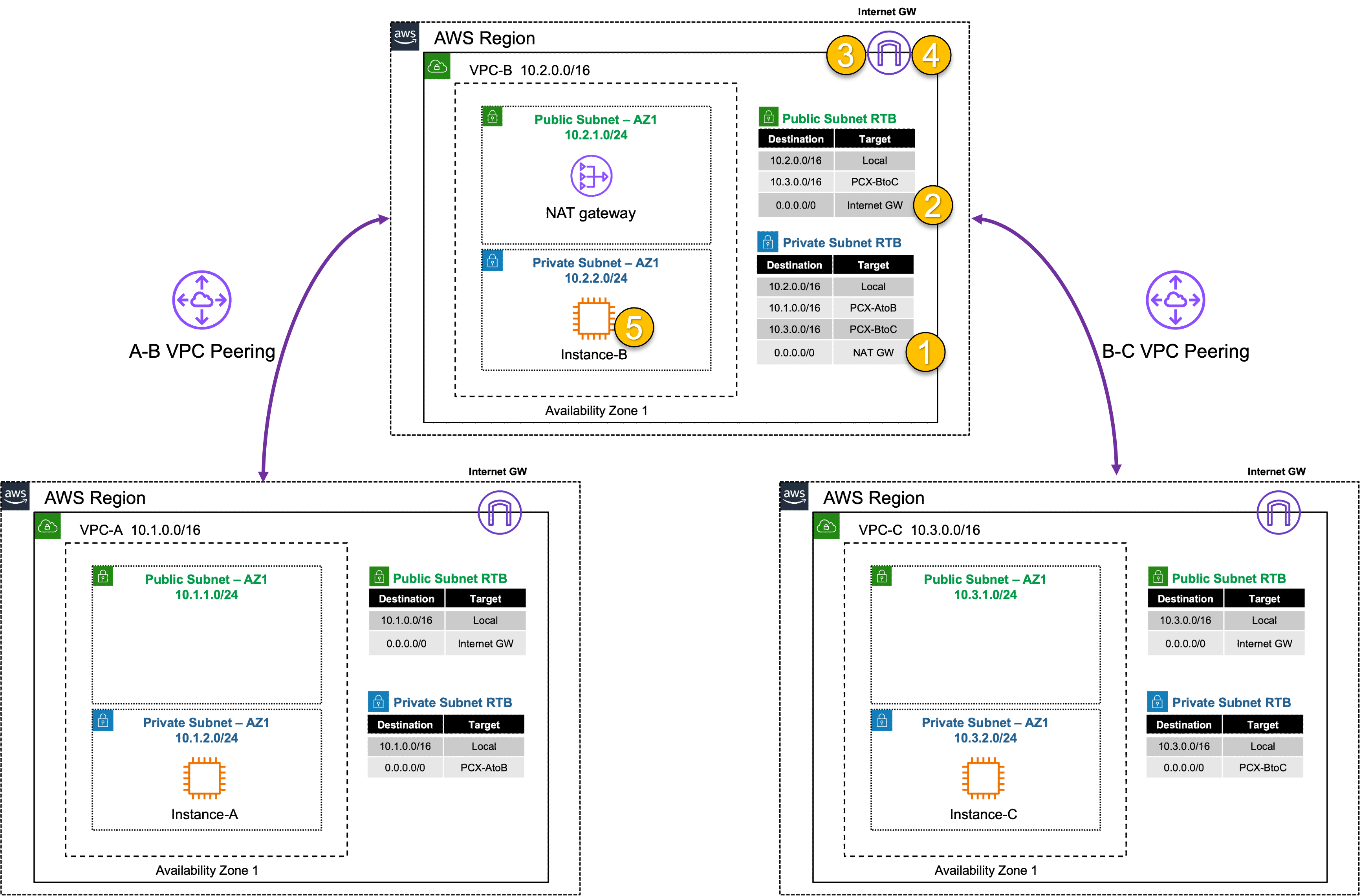
4) Let’s dig deeper to understand how VPC Peering works
5) Lab environment teardown
Discussion Points
- VPC peering is a point-to-point connection only (no transitive routing)
- It is best used when a few trusted VPCs are transferring large amounts of data between each other (ie DB replication)
- Full mesh is required to connect all VPCs together
- For example connecting 16 VPCs in full mesh would require (16*15)/2 = 120 connections
- The max supported VPC peering connections per VPC is 125
- VPC peering supports connections between VPCs:
- In the same or different AWS Accounts
- In the same (intra) or across (inter) regions
- When using inter-region peering, AEAD encryption is used
- No Internet Gateway is required for VPC Peering (even when inter-region)
- Jumbo frames (9001 bytes) are only supported for intra-region connections, inter-region is limited to 1500 bytes
This concludes this task