Transit Gateway w/ VPCs
| Goal | Establish open, secured east/west (Inter-VPC), and outbound flows through the provisioned NGFW VPC and Transit gateway architecture. |
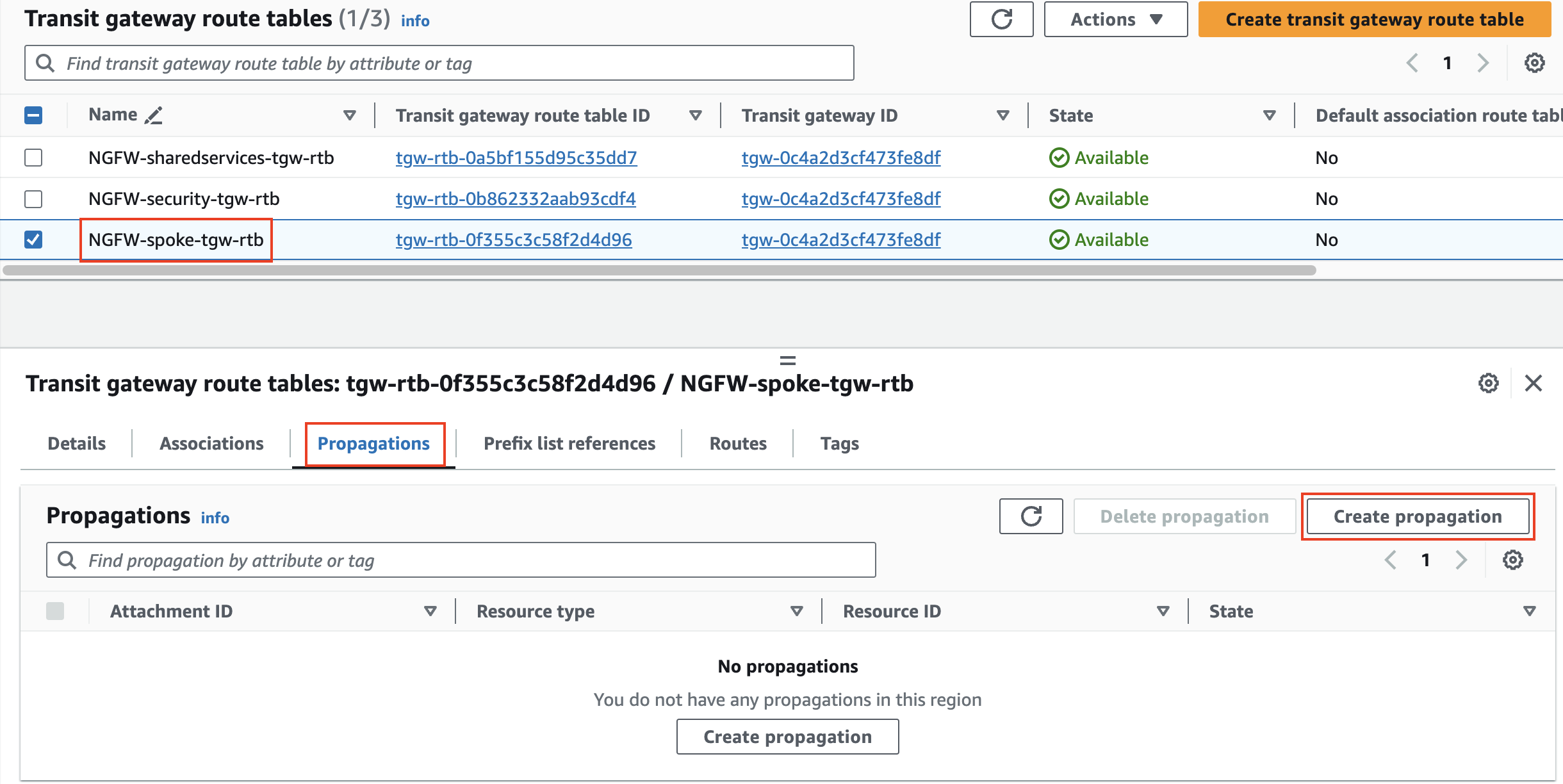
| Task | Create attachment associations + propagations and configure FortiGate routes and firewall policy to allow secured traffic. |
| Validation | Confirm outbound and east/west connectivity from EC2 Instance-A via Ping, HTTP, HTTPS. |
Introduction
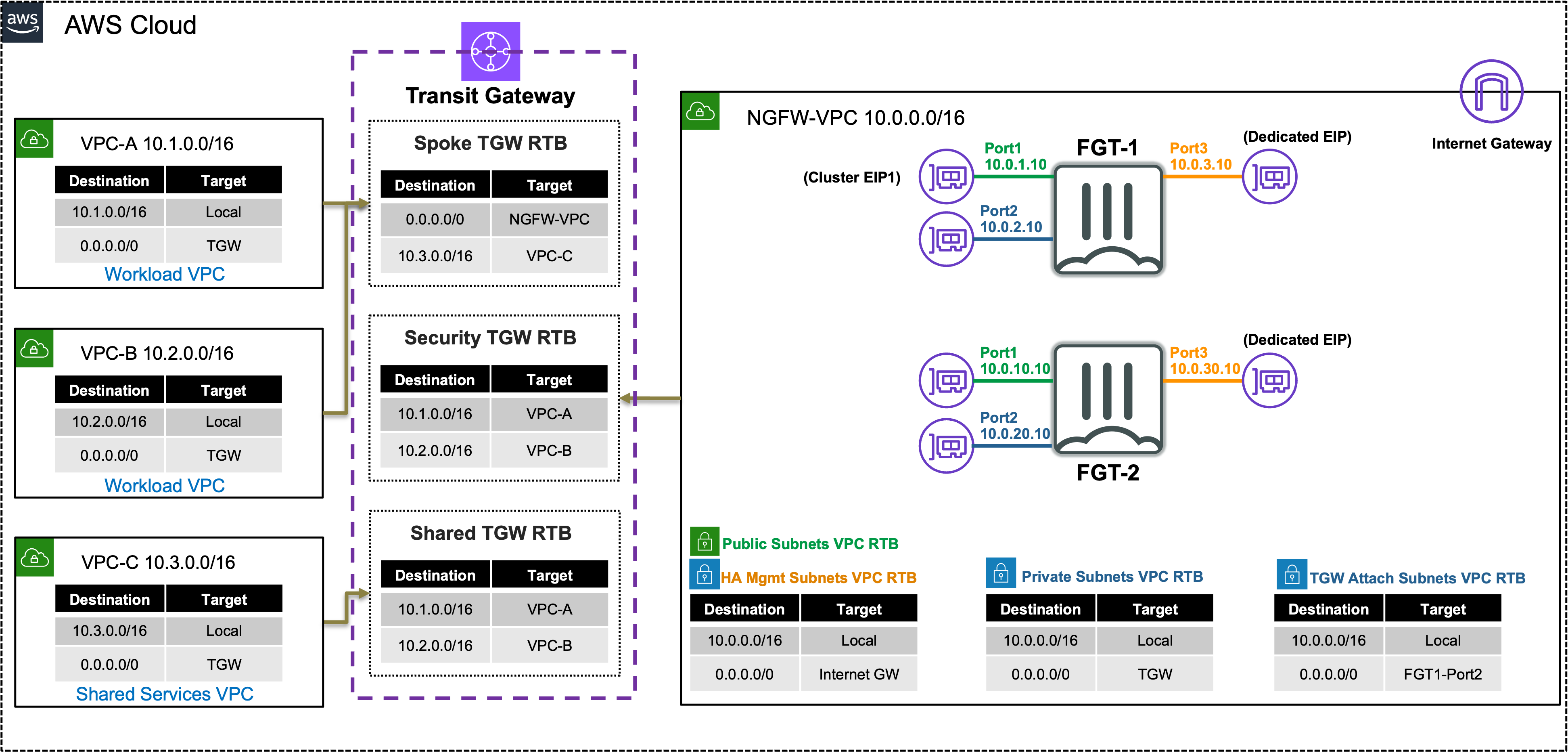
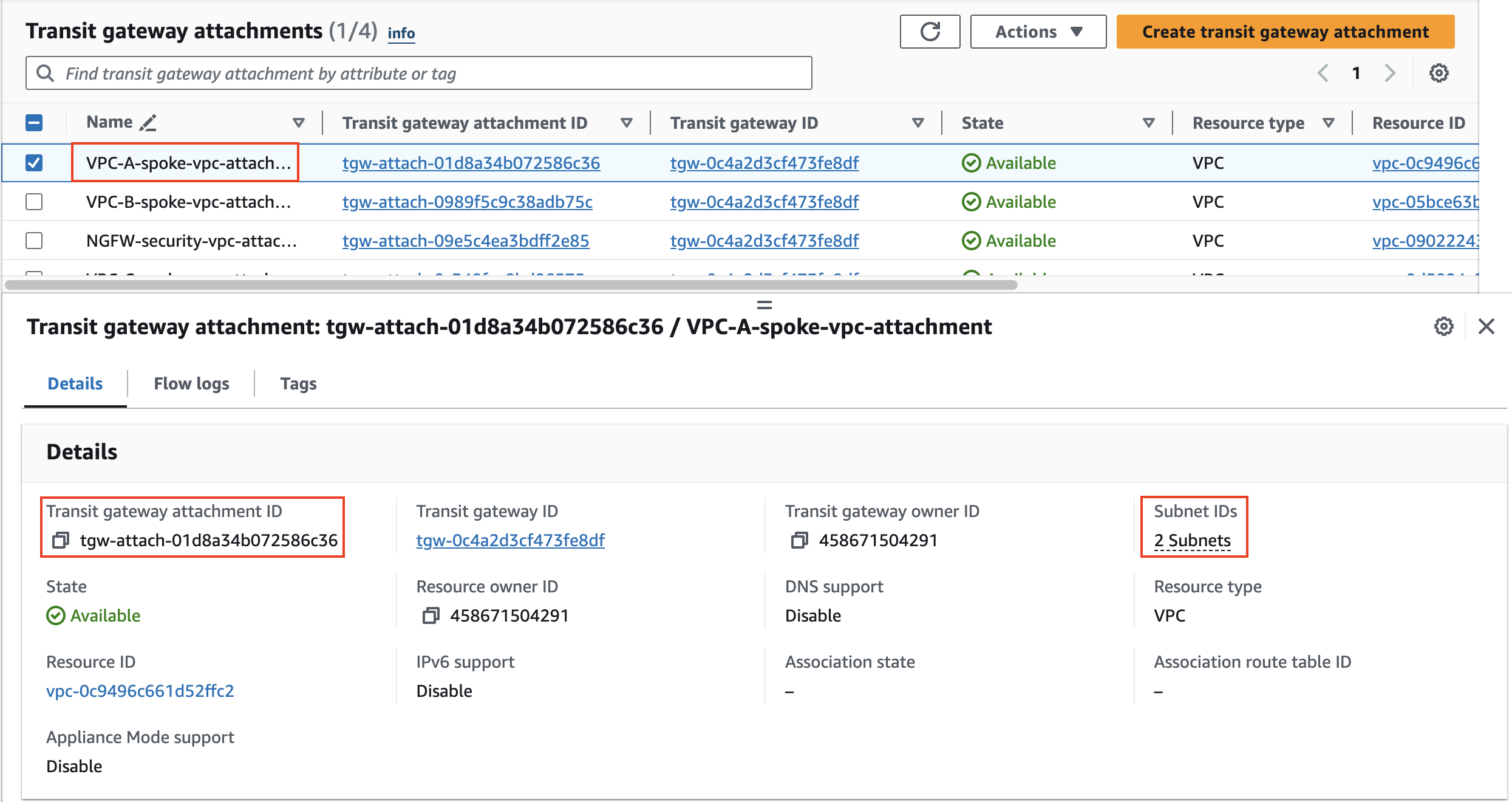
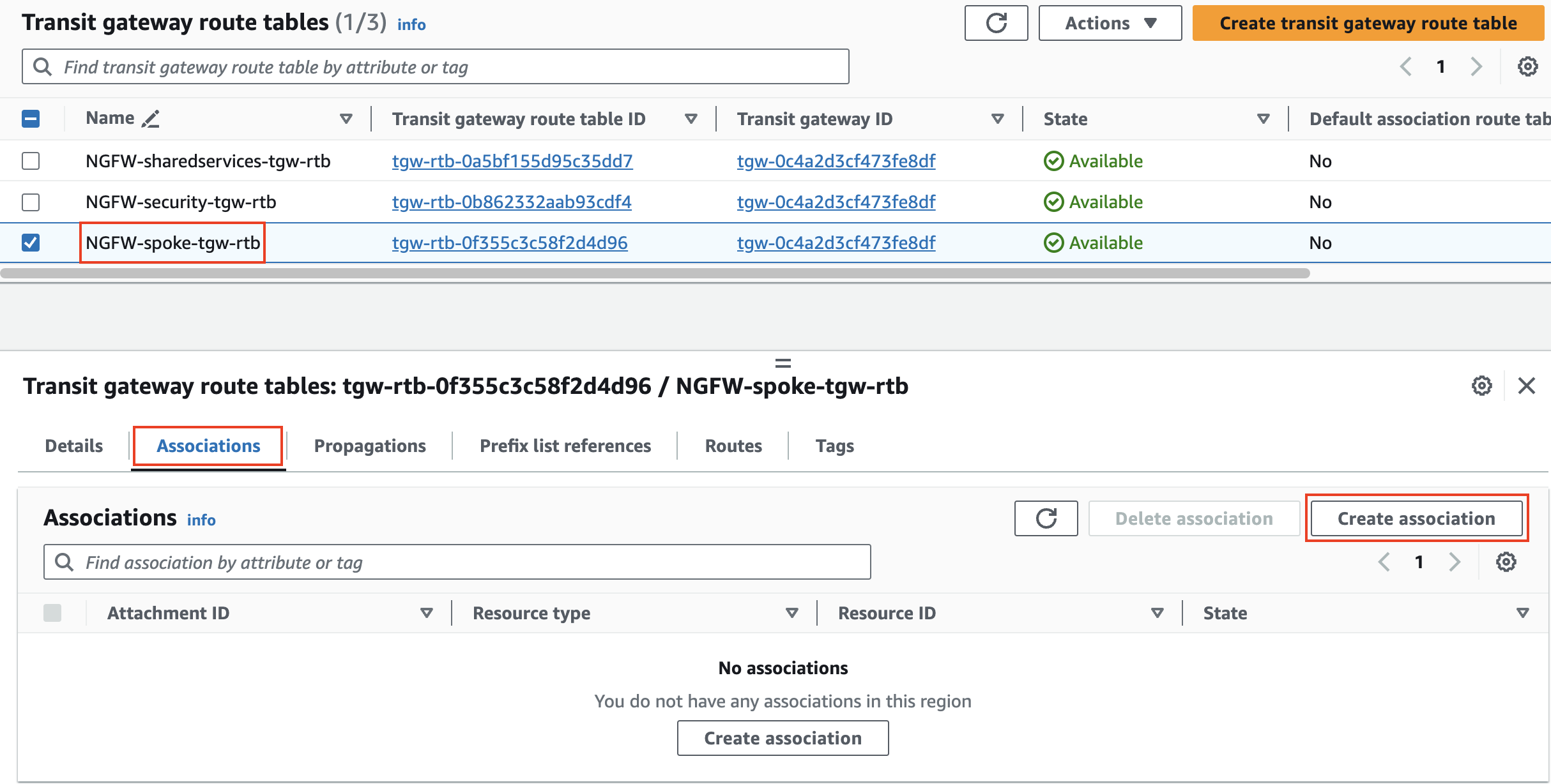
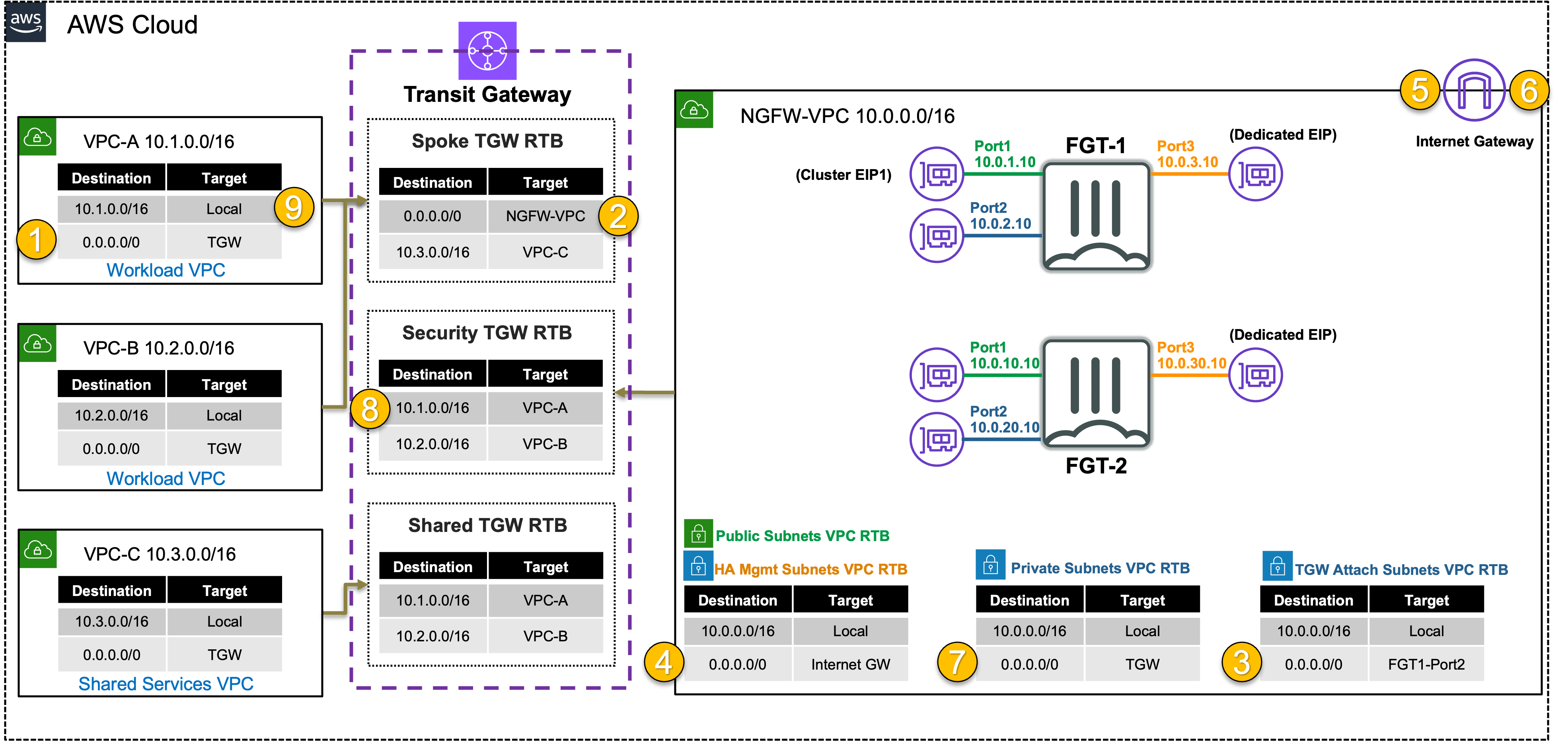
In this task, there are multiple VPCs in the same region that have one instance each. Transit Gateway (TGW) is configured with multiple Transit Gateway Route Tables. You will need to create the appropriate VPC attachment associations and propagations to the correct TGW Route Tables, FW policy and update a static route on the FortiGate Active-Passive cluster.
In this scenario you will allow traffic between the workload and shared services VPC to communicate directly (without going through the FortiGate A-P cluster), while inspecting outbound and east/west connectivity for the workload VPCs.
Summarized Steps (click to expand each for details)
0) Lab environment setup
1) Inspect the Transit Gateway VPC attachments
2) Create associations and propagations for VPC attachments to Transit Gateway Route Tables for east/west to shared services
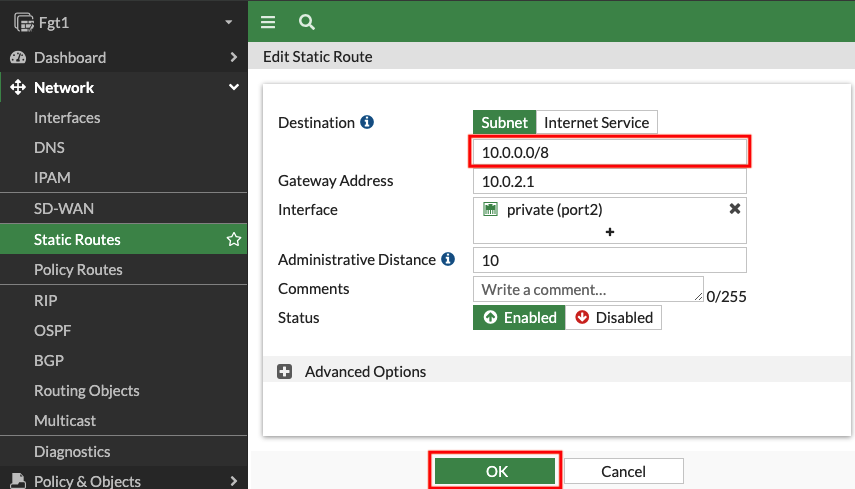
3) Create a default route for centralized east/west and outbound through an inspection VPC
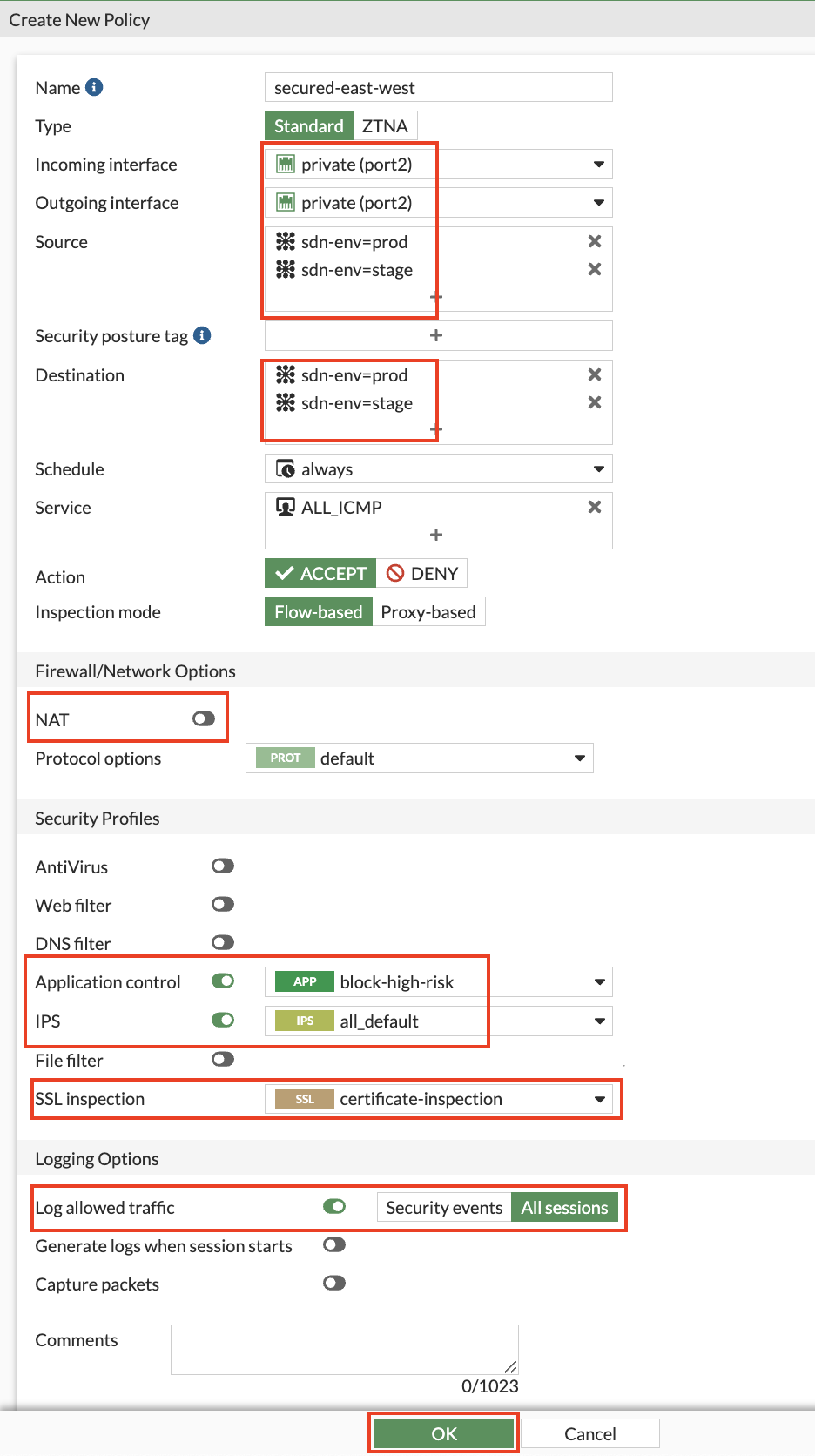
4) Login to the FortiGate GUI, modify a route and add a Firewall Policy allowing east/west
5) Test open east/west connectivity from Instance-A to Instance-C in shared services
6) Test secured east/west and outbound connectivity from Instance-A to Instance-B
7) Let’s dig deeper to understand how all of this works
8) Lab environment teardown
Discussion Points
- TGW is essentially a regional router
- TGW supports transitive routing and has many use cases
- TGW supports the following attachments in the same region:
- VPC (static propagation of VPC CIDR)
- VPN (static or dynamic routing)
- Direct Connect Gateway (static or dynamic routing)
- TGW Connect (GRE over VPC or Direct Connect attachment, supports static or dynamic routing)
- Jumbo frames (8500 bytes) are supported for all attachments except VPN (1500 bytes)
- TGW supports peering directly between TGWs in the same or different regions (supports static routing only)
- FGTs can be attached to the TGWs to provide dynamic routing between them with an overlay tunnel
- TGW supports default route table propagation and association settings which can be used to automate connecting spoke VPCs to a simple centralized design
- Centralized Inspection VPC handles FortiGate NGFW inspection for any traffic flow (Inbound, Outbound, East/West)
- Advanced architectures for all of these scenarios can be found here
This concludes this task