Cloud WAN
| Goal | Utilize Cloud WAN components and Core Network Policy to provide a secured & orchestrated network. |
| Task | Update Core Networking Policy with logic to automate connecting resources to segments and propagating routes to allow secured traffic flow. |
| Validation | Confirm east/west connectivity from EC2 Instance-A via Ping, HTTP. |
Introduction
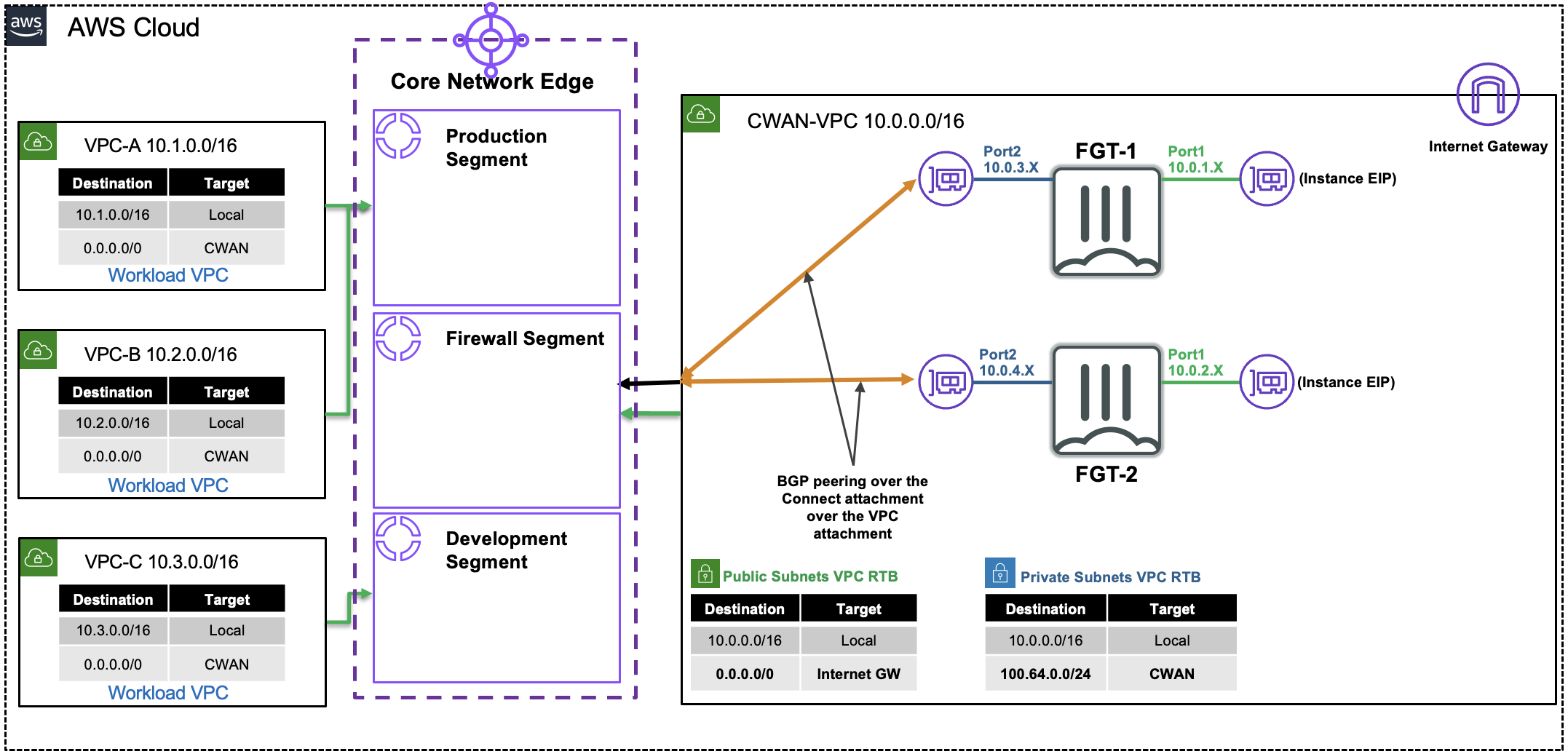
In this design, there are multiple VPCs in the same region that have one instance each. Cloud WAN is configured with multiple segments and attachments (both VPC and Tunnel-less Connect). You will need to create the appropriate Cloud WAN Core Network Policy to automatically enforce segment attachment rules and propagation of routes between segments to direct traffic to the independent FortiGates for traffic inspection.
In this setup these FortiGate are independent (not clustered, nor sharing config) but are working together with FGSP in an Active-Active design to provide more capacity and synchronize session tables. This design specifically uses Tunnel-less Connect attachments to allow dynamic routing between EC2 instances and a Cloud WAN Core Network Edge (CNE) without needing IPsec or GRE based overlay tunnels. This removes the overhead and bottlenecks that come with overlay tunnel protocols while still providing dynamic routing.
Summarized Steps (click to expand each for details)
0) Lab environment setup
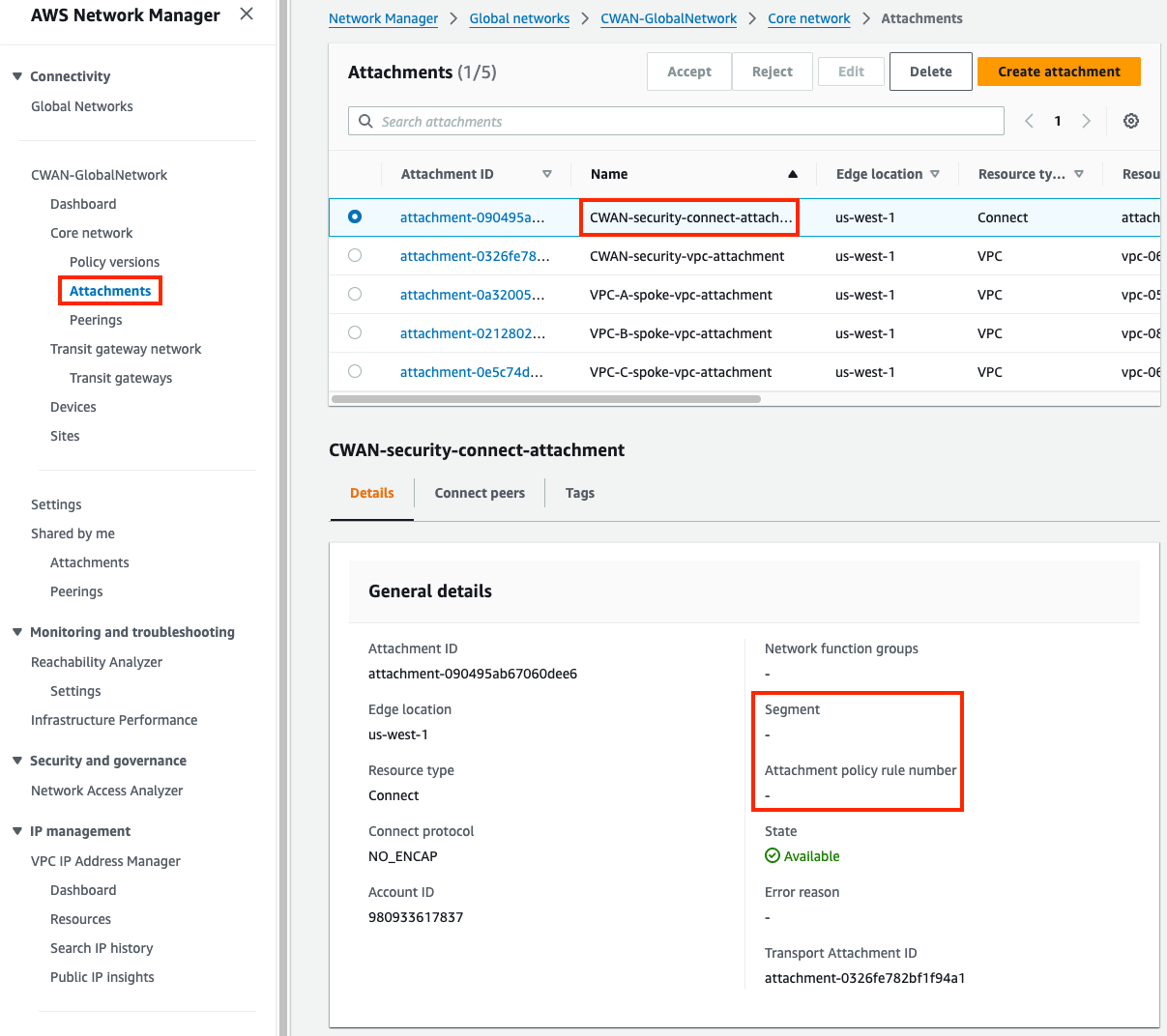
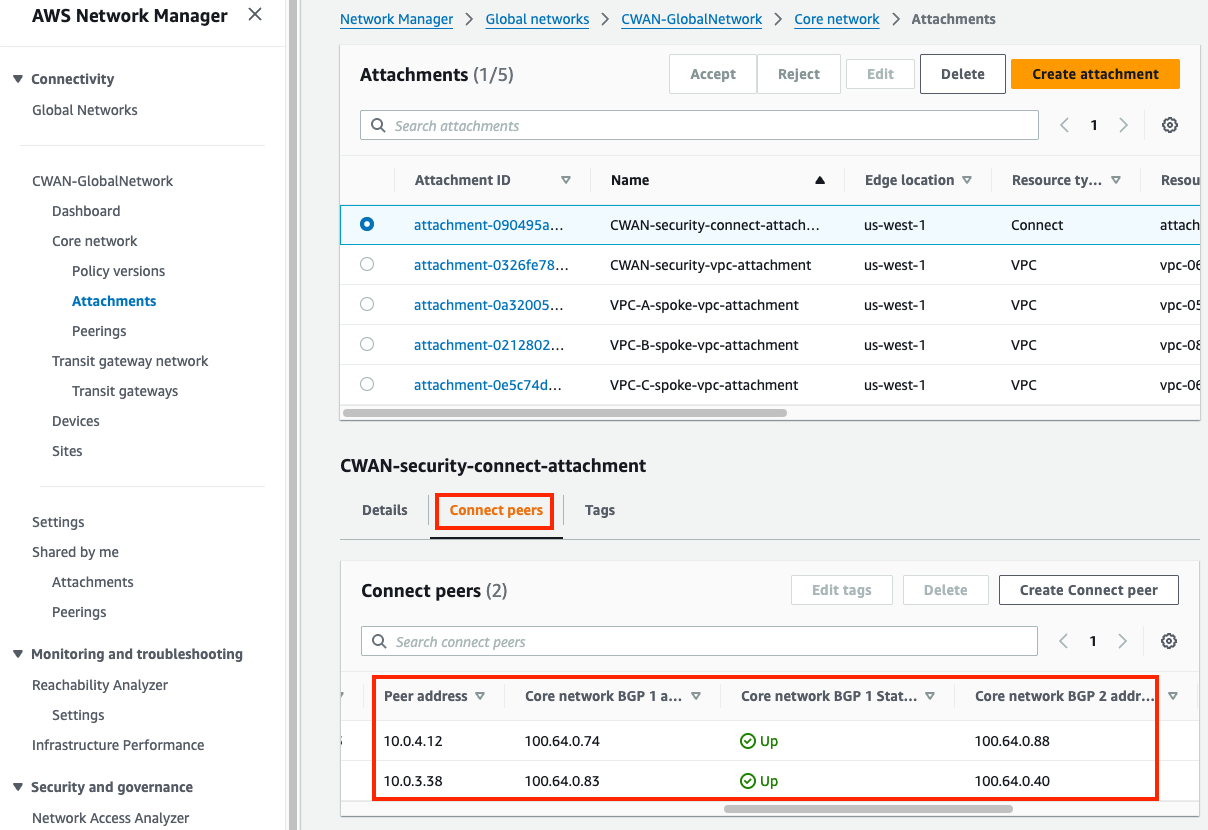
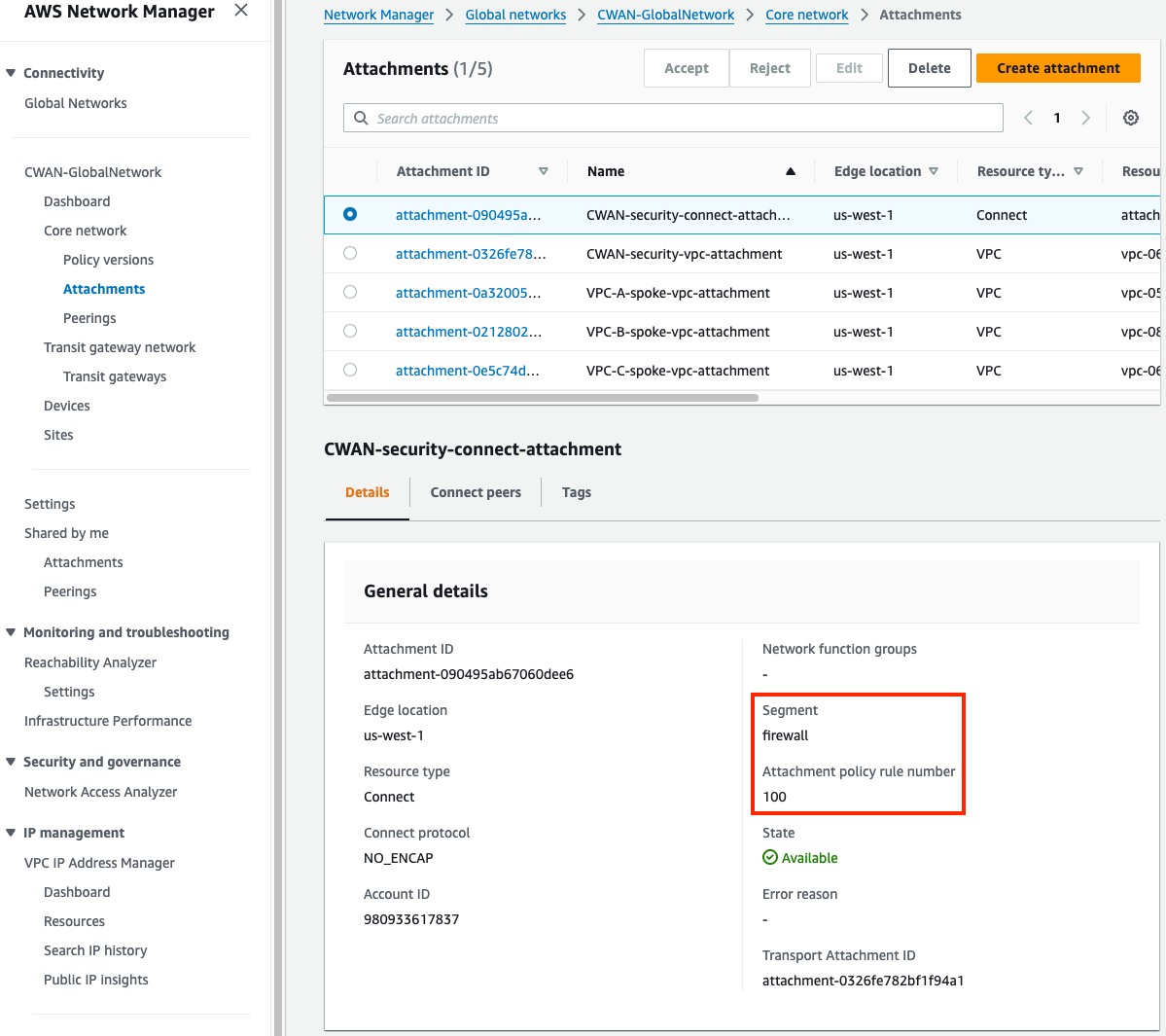
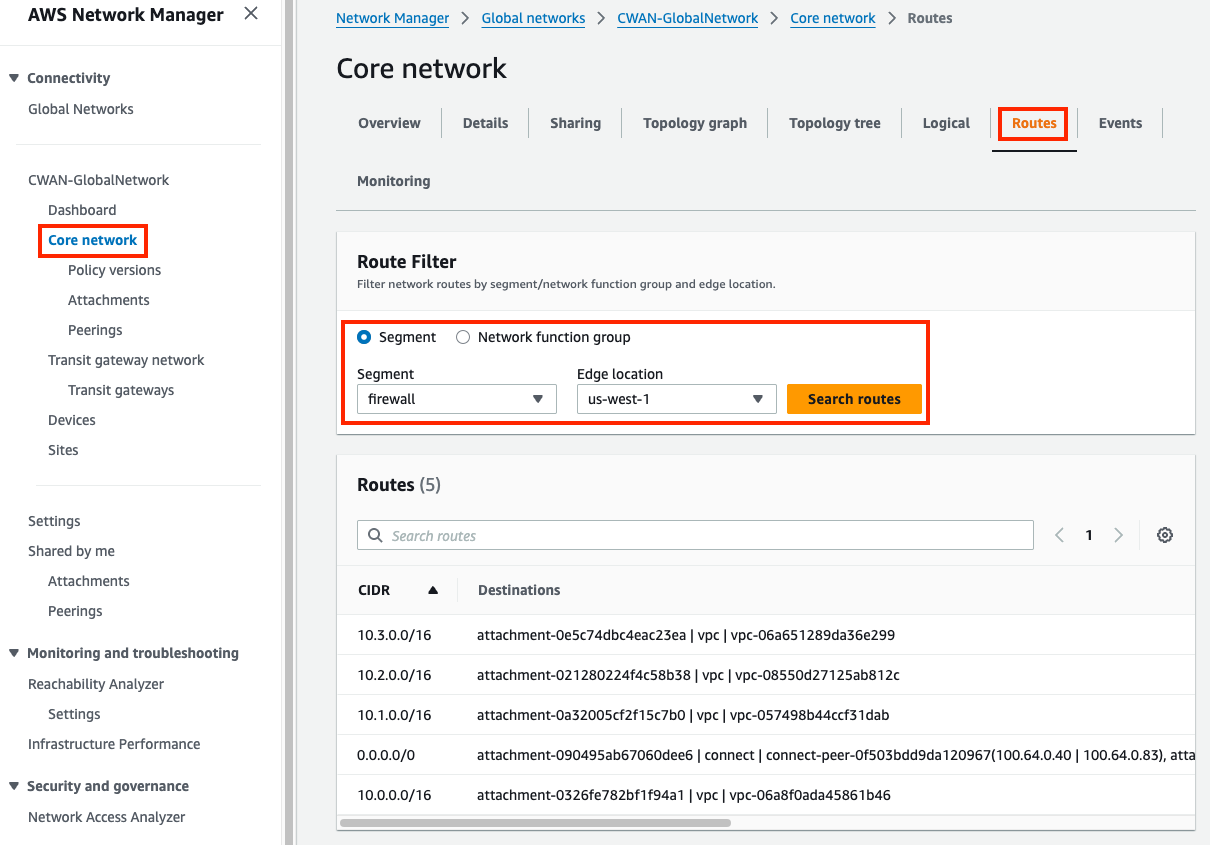
1) Inspect the Cloud WAN attachments and segments
2) Review FortiGate1’s BGP config and current routes advertised/received
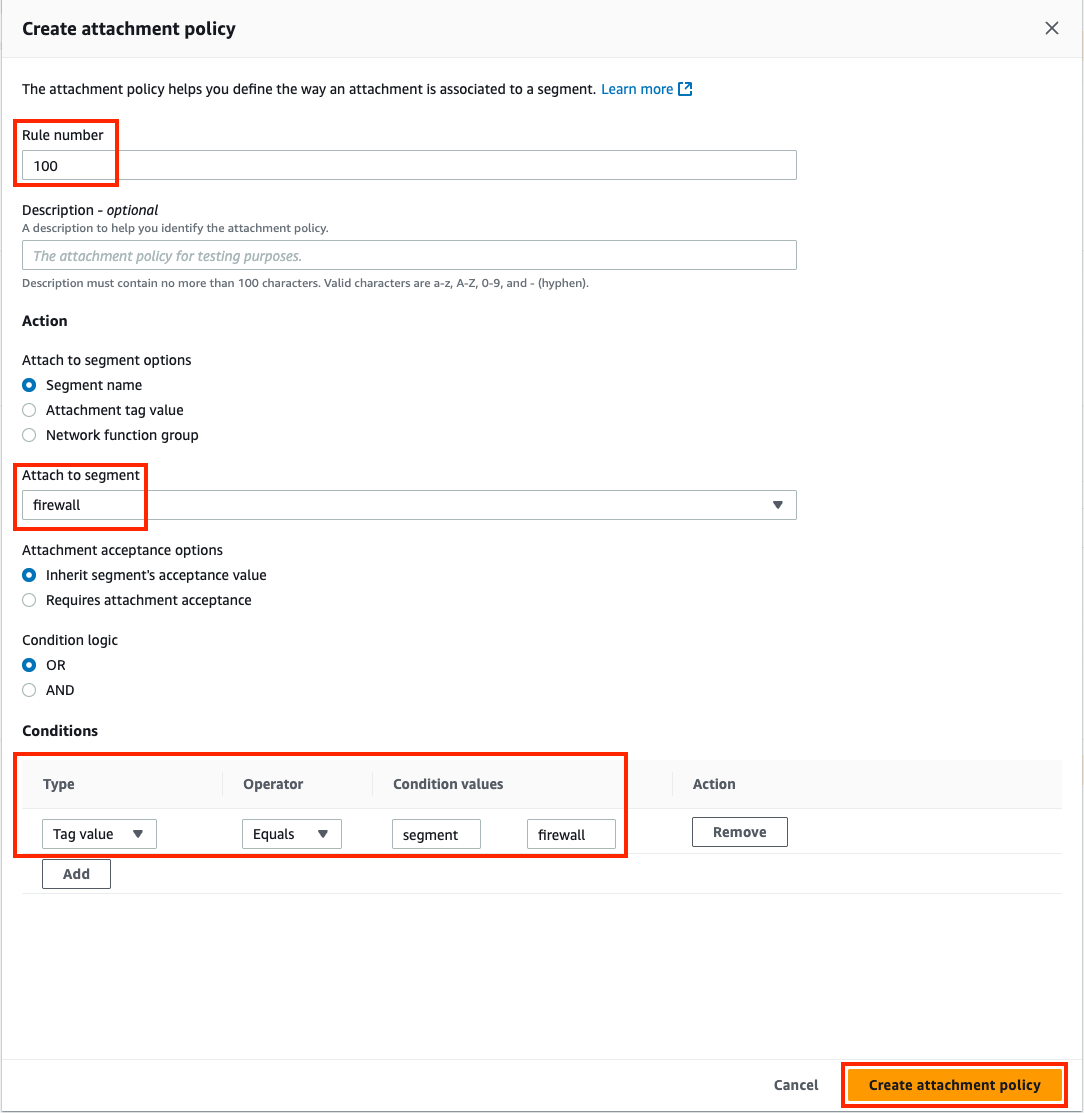
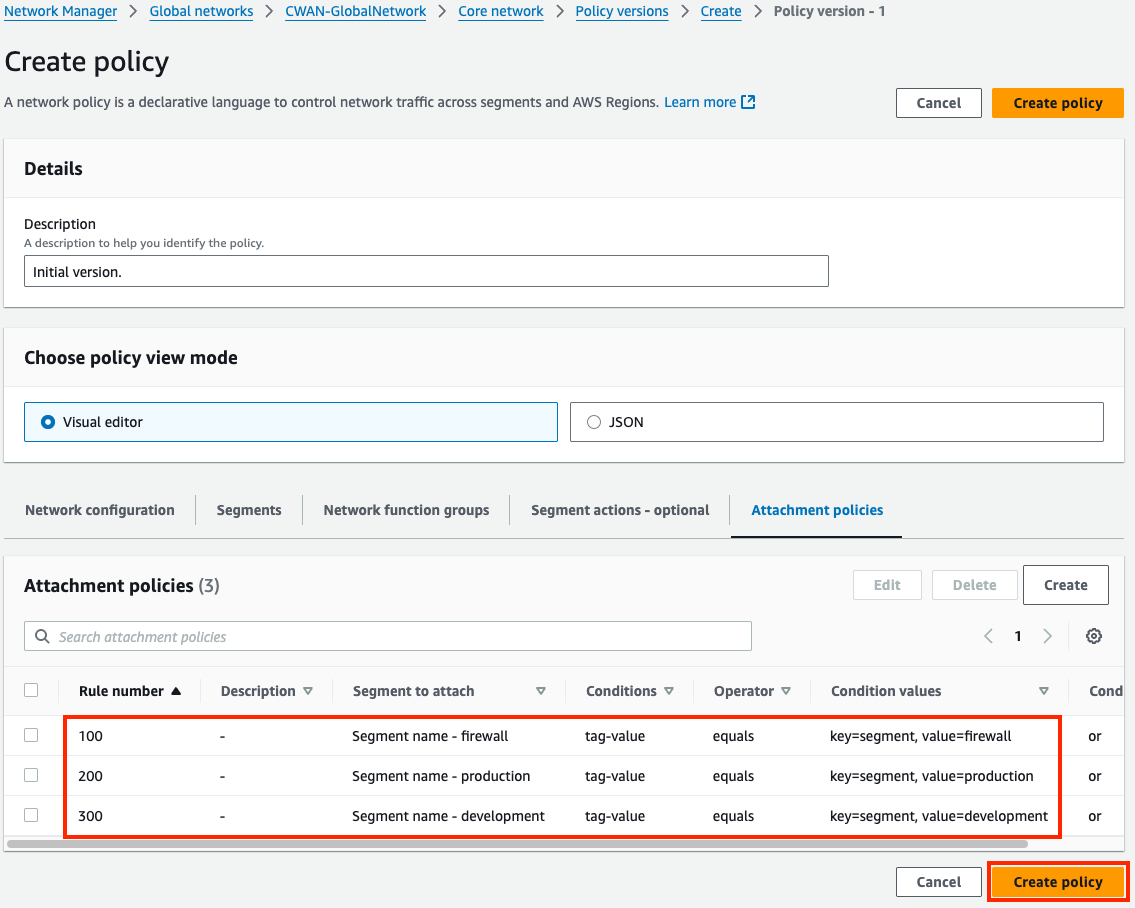
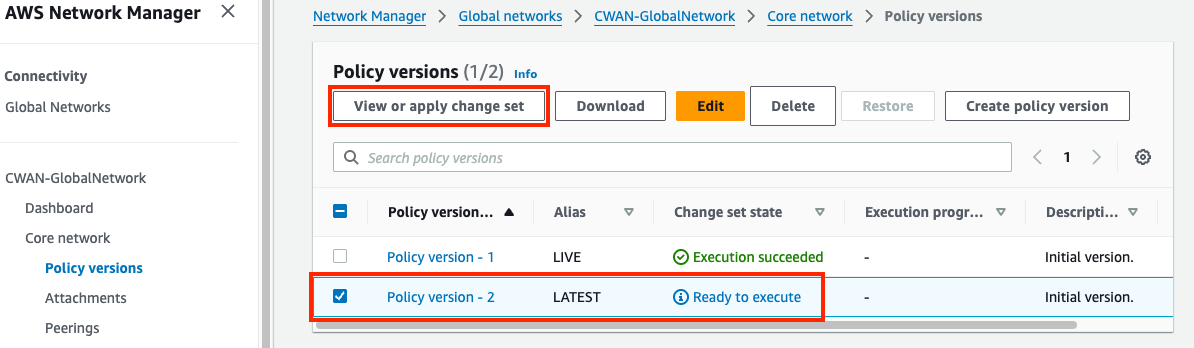
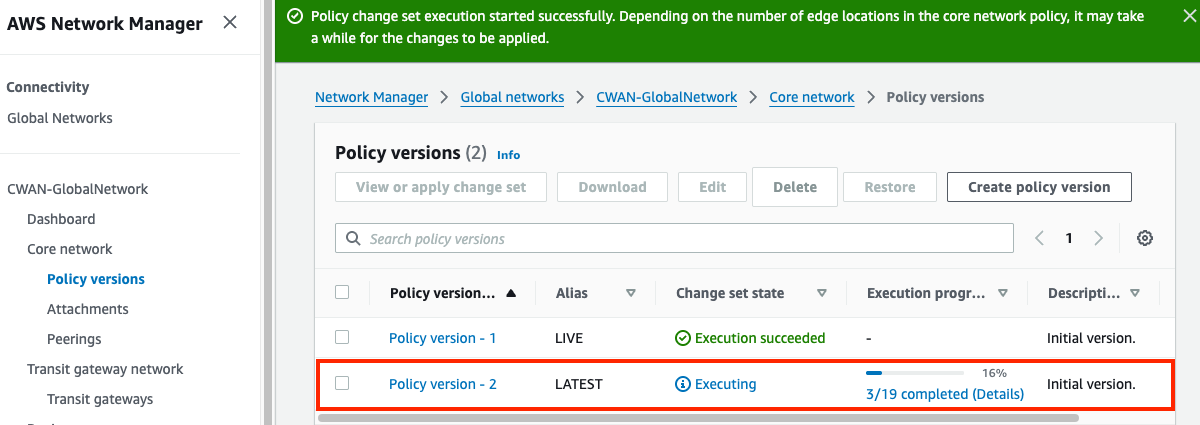
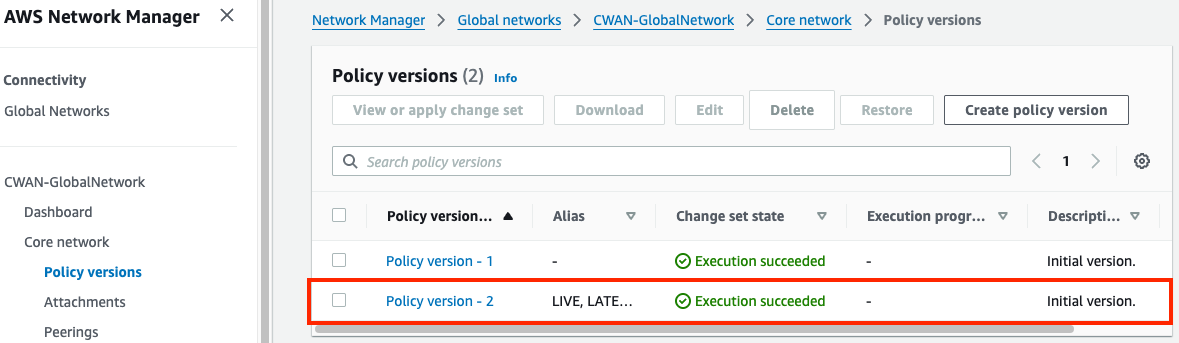
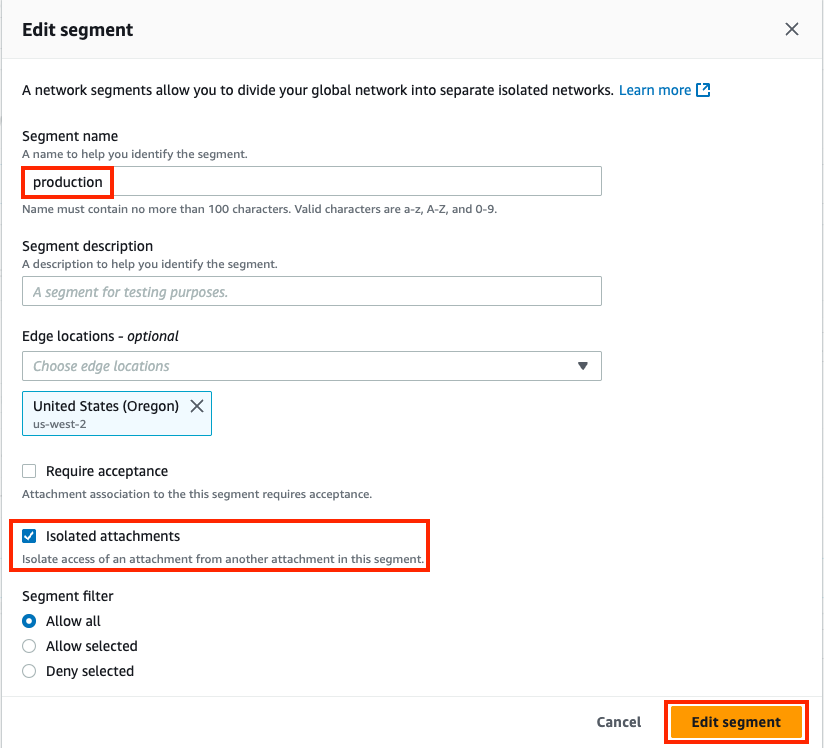
3) Update & Apply Core Network Policy
4) Test traffic and Validate Results
5) Let’s dig deeper to understand how all of this works
6. Lab environment teardown
Discussion Points
- Cloud WAN (CWAN) is a global service
- Network Manager Console, Global Network, and Core Network Policy are Global
- Segments can be regional or global, based on CNE locations and attached resources
- Core Network Edge (CNEs), and attachments (VPC, Connect, VPN, Direct Connect, etc) are regional
- Segments are dedicated routing domains that can be isolated or allow direct communication between attached resources
- Core Network Edges (CNEs) are essentially managed TGWs which are peered together with BGP
- Core Network Policy allows granular automation of attachment association, propagation, and sharing of other routes between segments
- CWAN supports ECMP routing with routes from the same attachment type
- CWAN is a stateless router which will result in asymmetric routing of traffic
- SNAT is required for flow symmetry to the correct FortiGate in Active-Active design
- FGSP can be used instead for Active-Active East/West inspection with caveats
- Appliance Mode is not required but recommended as it limits the amount of asymmetric traffic
- Connect (tunnel-less) attachments use BGP directly to privately connect to an appliance within a VPC only
- Each CWAN Connect (tunnel-less) peer supports up to 100 Gbps, (actual limit is based on instance type BW)
- Jumbo frames (8500 bytes) are supported for all attachments except VPN (1500 bytes)
This concludes this task