Task 2: Create Distributed Workload VPC using Terraform in AWS Cloudshell
- Log into your AWS account and navigate to the Console Home.
Info
Note: Make sure you are running this workshop in the intended region. The defaults are configured to run this workshop in us-west-2 (Oregon). Make sure your management console is running in us-west-2 (Oregon), unless you intend to run the workshop in a different FortiGate CNF supported region.
- Click on the AWS CloudShell icon on the console navigation bar
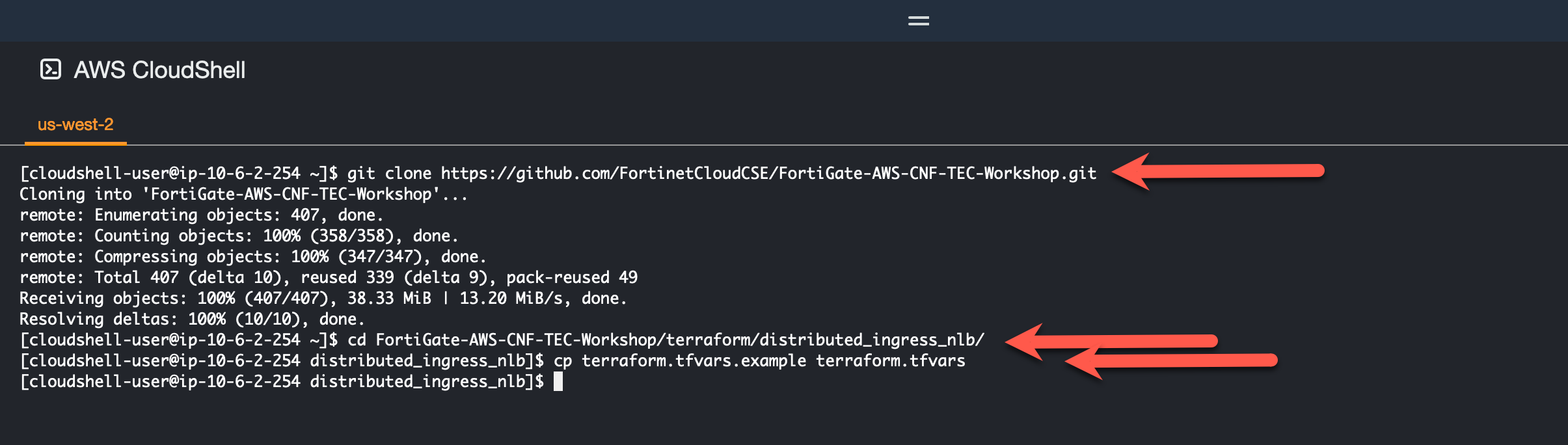
Clone a repository that uses terraform to create a distributed ingress workload vpc
git clone https://github.com/FortinetCloudCSE/FortiGate-AWS-CNF-TEC-Workshop.gitChange directory into the newly created repository for distributed_ingress_nlb
cd FortiGate-AWS-CNF-TEC-Workshop/terraform/distributed_ingress_nlbCopy the terraform.tfvars.example to terraform.tfvars
cp terraform.tfvars.example terraform.tfvars
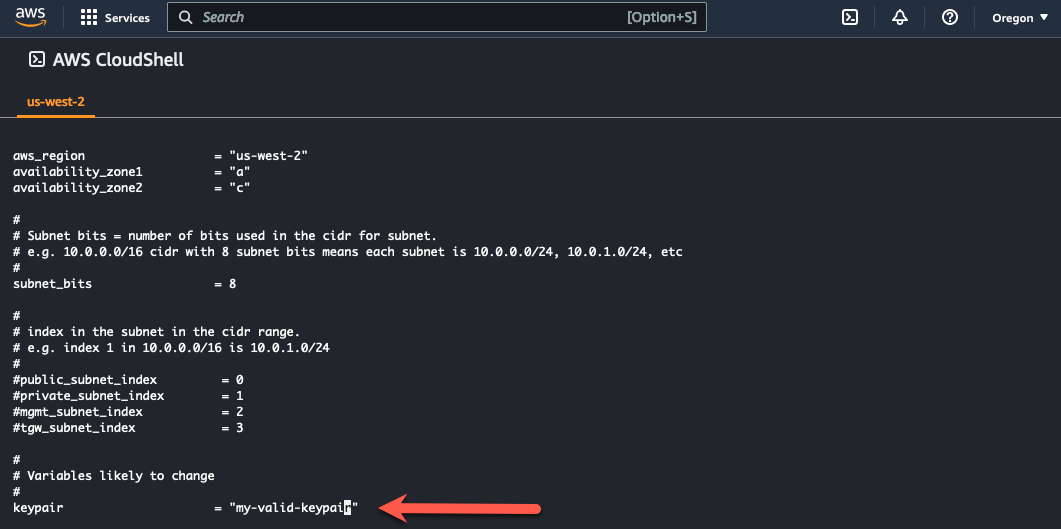
- Edit the terraform.tfvars file and insert the name of a valid keypair in the keypair variable name and save the file
Info
Note: Examples of preinstalled editors in the Cloudshell environment include: vi, vim, nano
Info
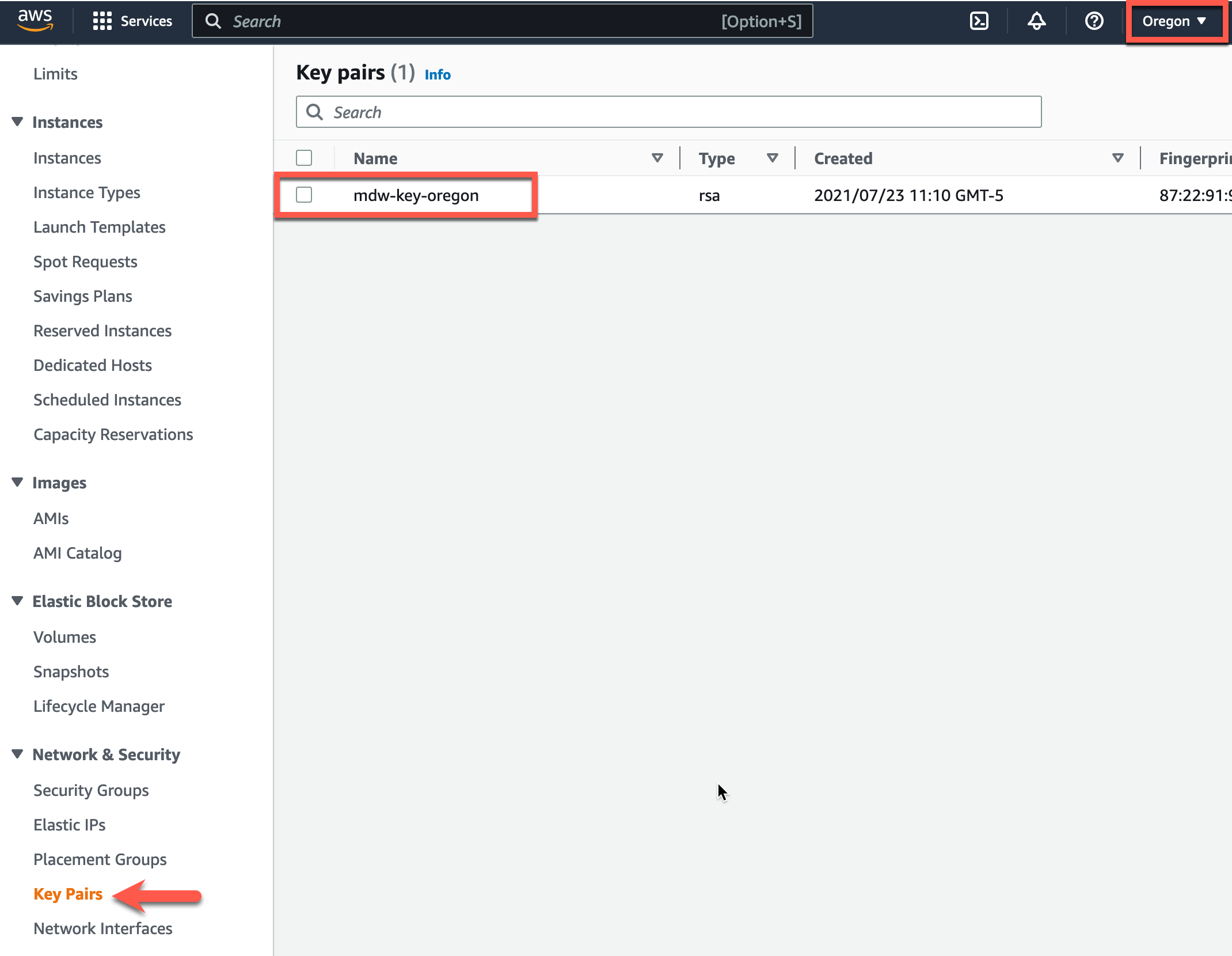
Note: AWS Keypairs are only valid within a specific region. To find the keypairs you have in the region you are executing the lab in, check the list of keypairs here: AWS Console->EC2->Network & Security->keypairs. This workshop is pre-configured in the terraform.tfvars to run in the us-west-2 (Oregon) region.
Info
Note: You may change the default region in the terraform.tfvars file to another FortiGate CNF supported region if you don’t have a valid keypair in that region and you don’t want to create one for this workshop.
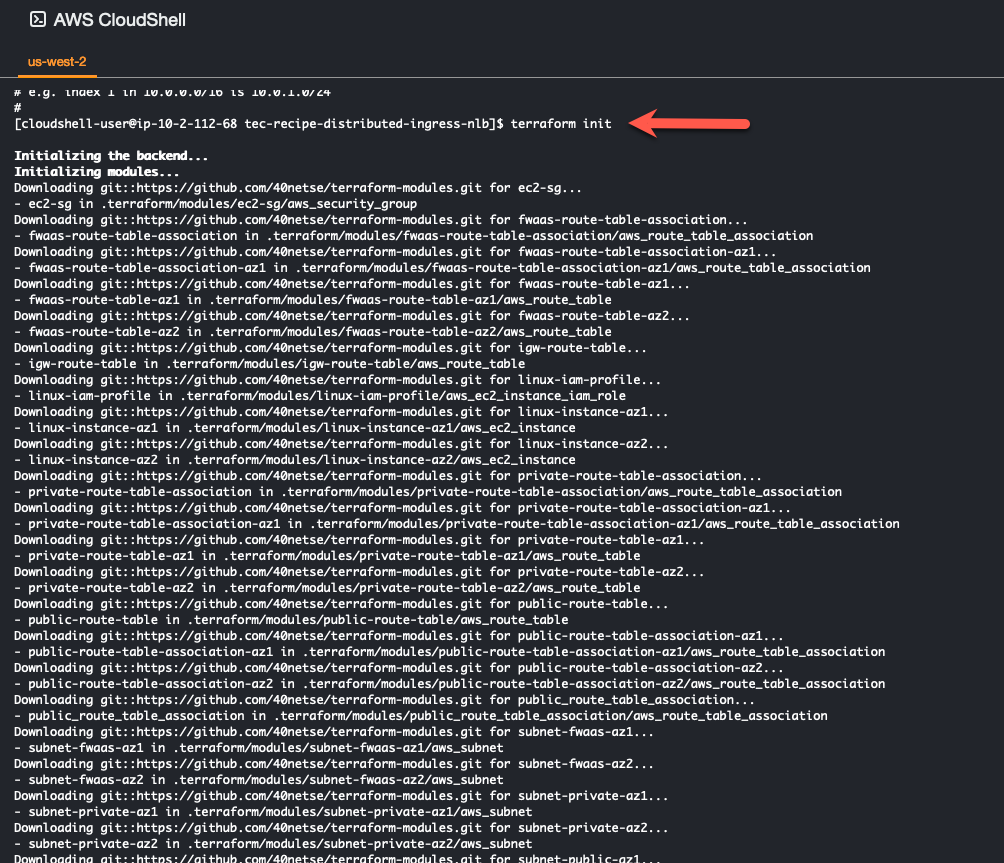
Use the “terraform init” command to initialize the template and download the providers
terraform init
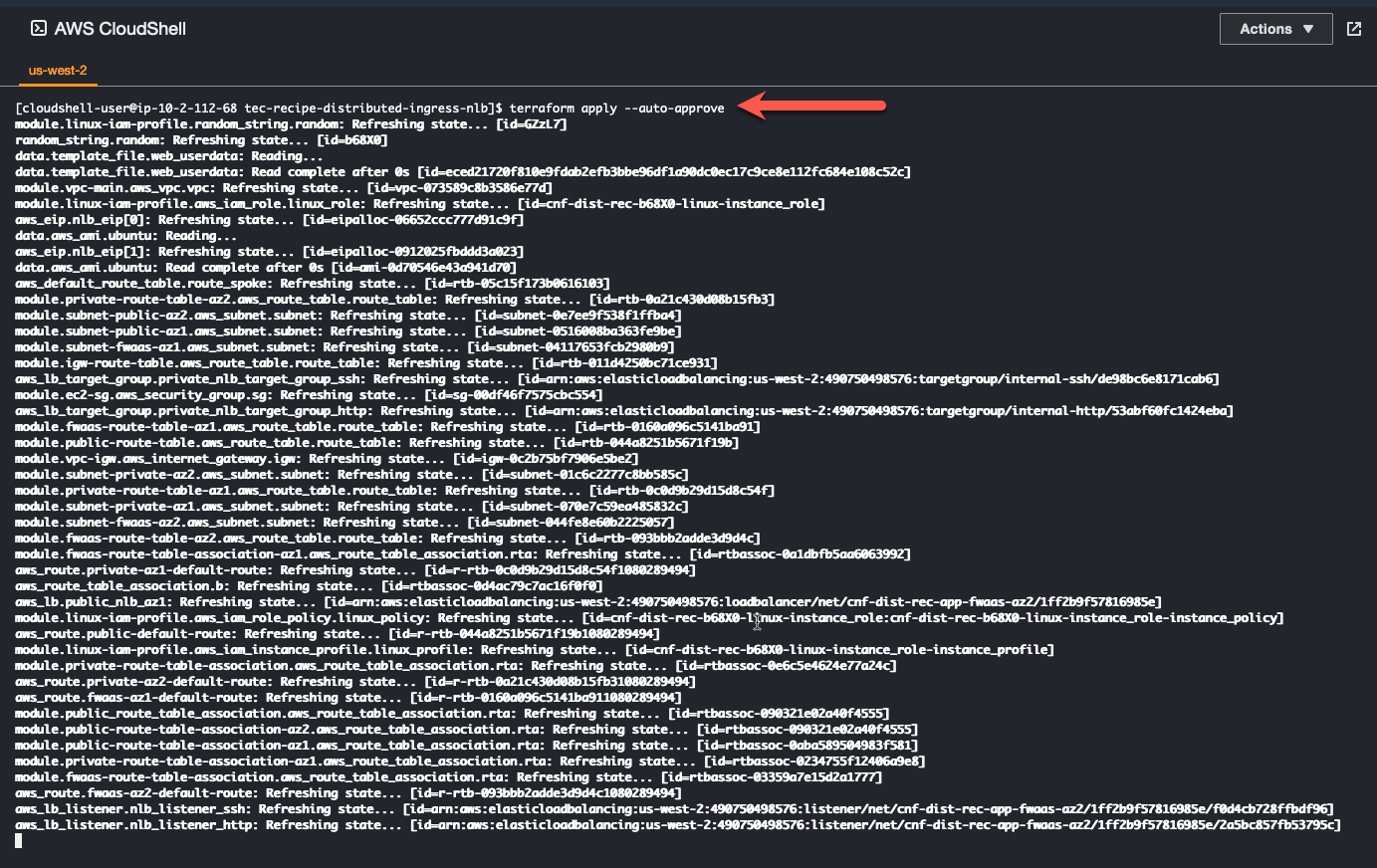
- Use “terraform apply –auto-approve” command to build the vpc. This command takes about 5 minutes to complete.
terraform apply --auto-approve
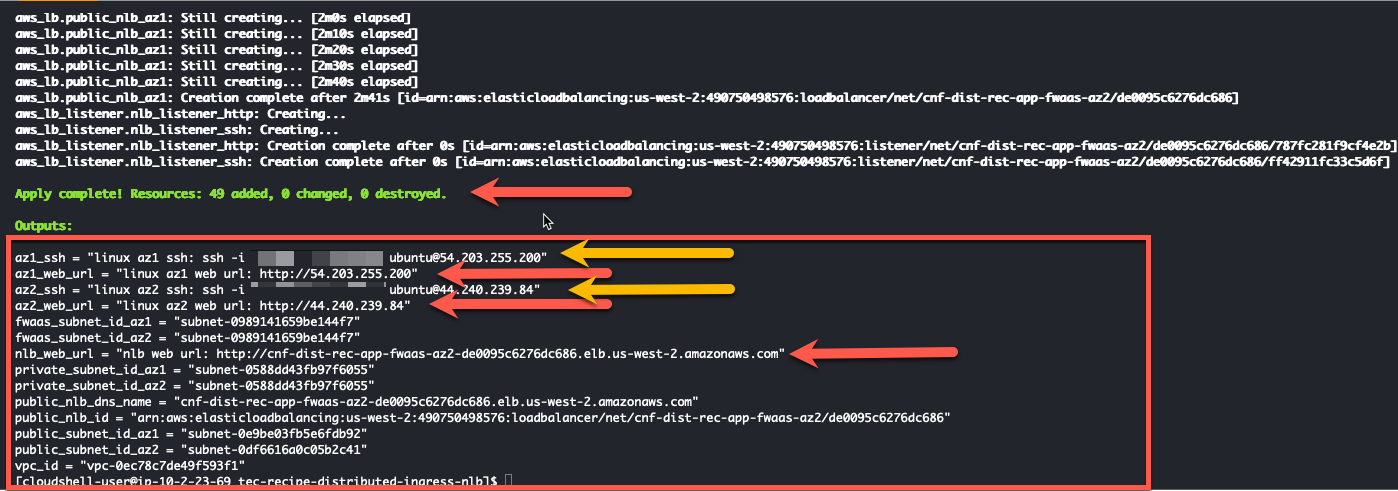
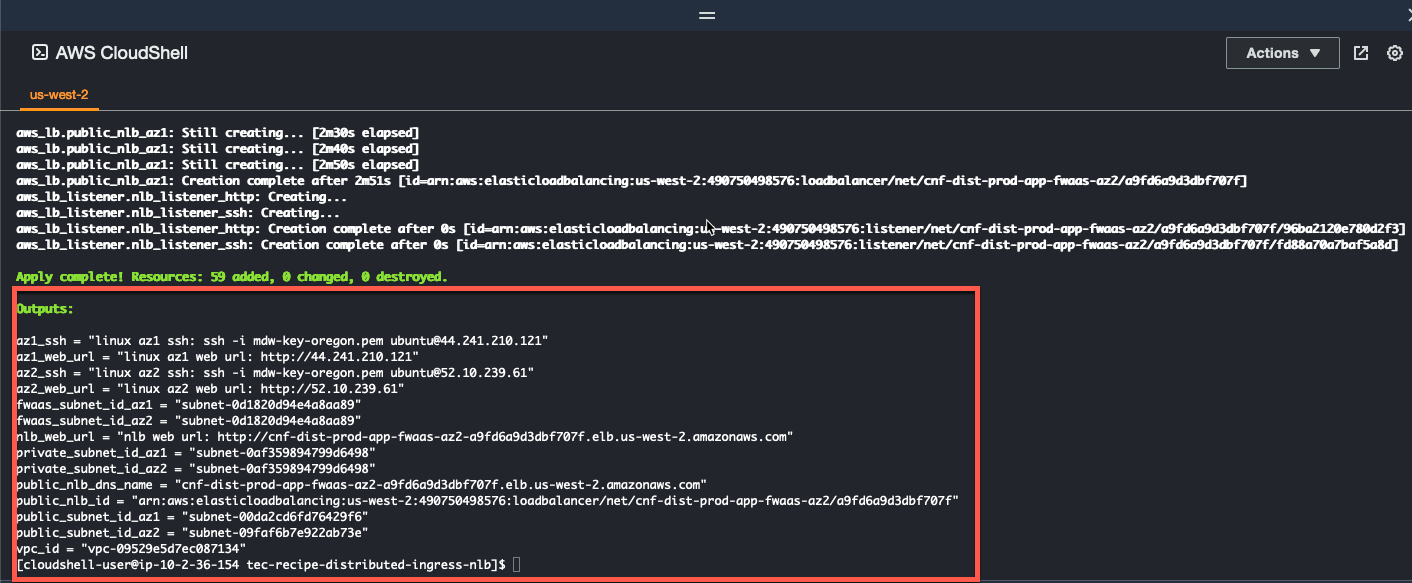
- When the command completes, verify “Apply Complete” and valid output statements.
- Make note of the Web Url (red arrow) for each instance and for the NLB that load balances between the Availability Zones.
- Make note of the ssh command (yellow arrow) you should use to ssh into the linux instances.
- Write down the Public IP address of the linux instance in AZ1. We are going to use that IP for our CNF external syslog server when we deploy Fortigate CNF.
- Bring up a local browser and try to access the Web Url. It will fail because these Web Servers are vulnerable and the security group only allows ssh (tcp port 22). We will fix this in the next task.
- Copy the “Outputs” section to a scratchpad. We will use this info throughout this workshop.
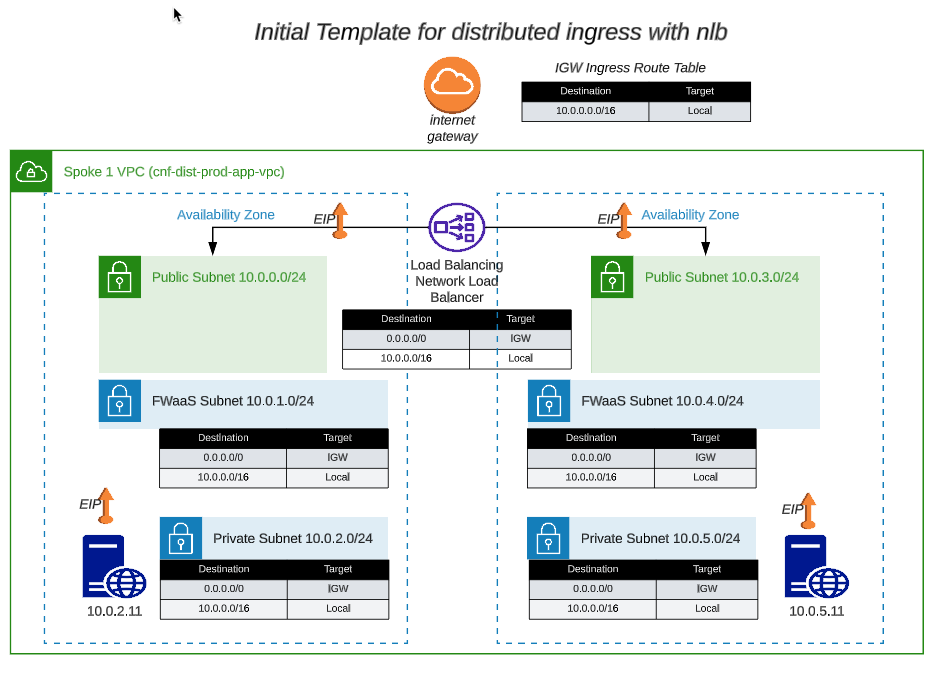
The network diagram for the distributed ingress vpc looks like this:
- This concludes this section.