Introduction
How to Demo and Sell FortiGate CNF

Welcome!
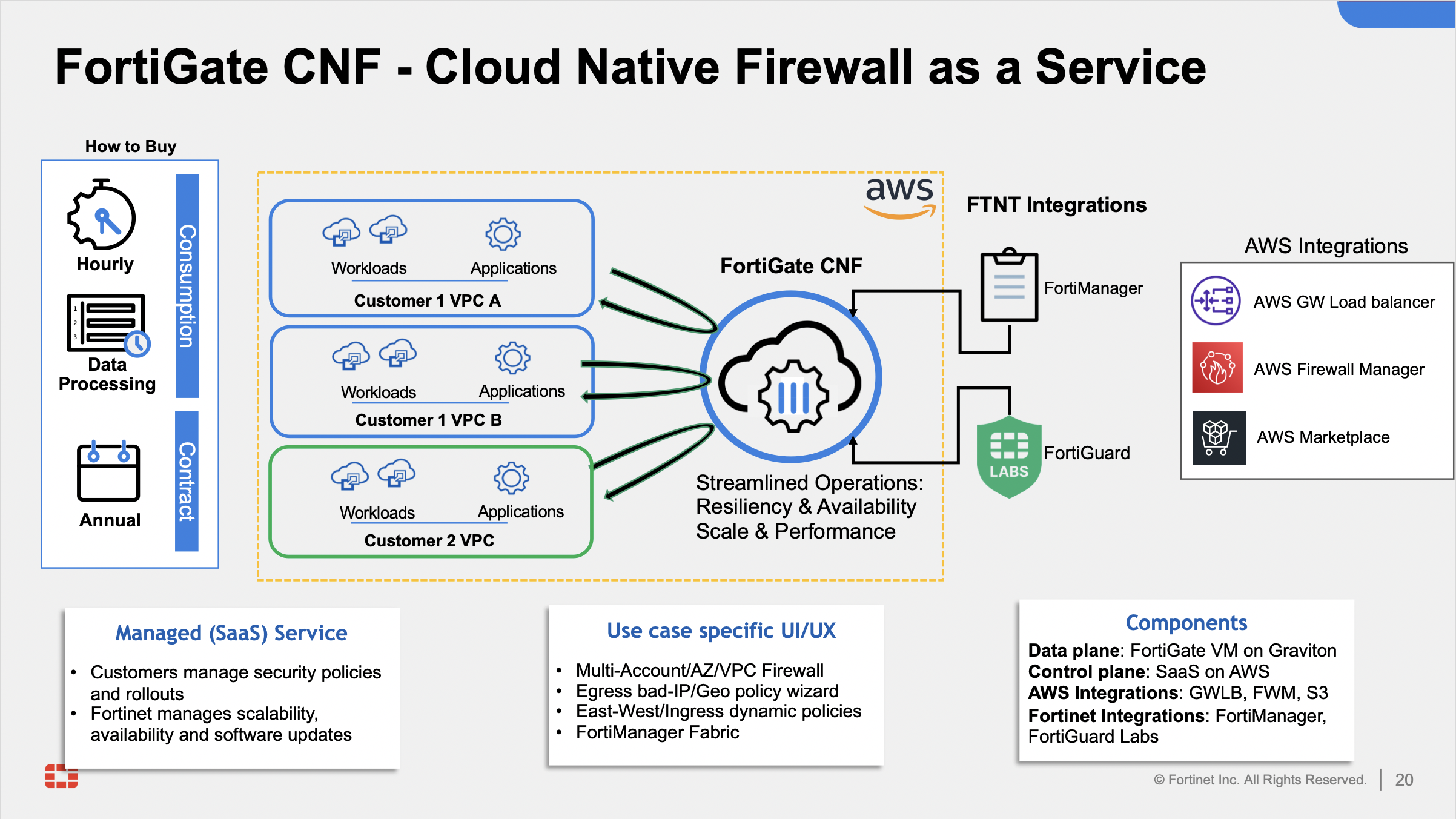
In this TEC Recipe, you will learn how to deploy FortiGate Cloud Native Firewall as a Service (FortiGate CNF). Fortinet customers can use this service to protect AWS workloads deployed in the cloud. Later sections in the TEC Recipe will demonstrate the use of common architecture patterns to protect different types of ingress, egress, and East-West traffic.
This TEC Recipe is intended to help accomplish the following:
- Learn common AWS networking concepts such as routing traffic in and out of VPCs for various traffic flows
- Use AWS Cloudshell and Terraform to deploy a demo environment
- Interact with FortiGate CNF Portal to deploy CNF instances, build security policy sets, and deploy them
- Test traffic flows in an example environment and use FortiGate CNF to control traffic flows
- Configure FortiManager to manage FortiGate CNF instances
- Configure FortiAnalyzer to collect and analyze logs from FortiGate CNF instances
- Learn how to use FortiGate CNF to protect AWS workloads in common architecture patterns
- Configure SDN Connectors to integrate FortiGate CNF with VPC Tagged objects and dynamic policy creation
Learning Objectives
At the end of this TEC Recipe, you will complete the following objectives:
- Understand AWS Networking Concepts (10 minutes)
- Understand AWS Common Architecture Patterns (10 minutes)
- Understand FortiGate CNF terminology (5 minutes)
- Subscribe to FortiGate CNF (5 minutes)
- Onboard an AWS account (5 minutes)
- Use AWS Cloudshell and Terraform to deploy a demo environment (10 minutes)
- Deploy a FortiGate CNF Instance & GWLBe endpoints (20 minutes)
- Create a policy set and apply it to a FortiGate CNF Instance (10 minutes)
- Test traffic flows (distributed in + egress and centralized e-w + egress) (20 minutes)
TEC Recipe Components
These are the AWS and Fortinet components that will be used during this workshop:
- AWS Marketplace
- FortiCloud
- FortiGate CNF Portal
- Hashicorp Terraform Templates (Infrastructure as Code, IaC)
- AWS SDN (AWS intrinsic router and route tables in a VPC)
- AWS Gateway Load Balancer (GWLB)
- AWS Transit Gateway (TGW)
- AWS EC2 Instances (Amazon Linux OS)
AWS Reference Architecture Diagram
This is the architecture and environment that will be used in the workshop.
With AWS networking, there are several ways to organize your AWS architecture to take advantage of FortiGate CNF traffic inspection. The important point to know is that as long as the traffic flow has a symmetrical routing path (for forward and reverse flows), the architecture will work.
This diagram will highlight two main designs that are common architecture patterns for securing traffic flows.
Distributed Ingress + Egress
Centralized Egress + East-West

Subsections of Workshop Prerequisites
Workshop Logistics
Accessing an AWS environment
For the FortiGate CNF Tec Recipe, you will need the following:
- AWS sign in link
- IAM User w/ console access
- Password for the IAM User
Accessing the FortiGate CNF Console
FortiGate CNF and other SaaS solutions are tied to your FortiCloud. If you do not already have one, please navigate here and complete the registration process.
Once logged in, you will see your FortiCloud dashboard.
You will log into the FortiGate CNF console later during the hands on section.
Info
Please log out before proceeding to the next part of the TEC Recipe.


Navigating the AWS Console
When you first login you will see the Console Home page.
Use the Search Box at the top to search for services such as EC2, VPC, Cloud Shell, etc.
When the results pop up, right click the name of the service and open the desired console in a new tab. This makes navigation easier.




AWS Networking Concepts
Before diving into the reference architecture for this workshop, let’s review core AWS networking concepts.
AWS Virtual Private Cloud (VPC) is a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways.
Availability zones (AZ) are multiple, isolated locations within each Region that have independent power, cooling, physical security, etc. A VPC spans all of the AZs in the Region.
Region, is a collection of multiple regional AZs in a geographic location. The collection of AZs in the same region are all interconnected via redundant, ultra-low-latency networks.
All subnets within a VPC are able to reach each other with the default or intrinsic router within the VPC. All resources in a subnet use the intrinsic router (1st host IP in each subnet) as the default gateway. Each subnet must be associated with a VPC route table, which specifies the allowed routes for outbound traffic leaving the subnet.
An Internet Gateway (IGW) is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the internet. It therefore imposes no availability risks or bandwidth constraints on your network traffic.
AWS NAT Gateway (NAT GW) is a Network Address Translation (NAT) service. You can use a NAT gateway so that instances in a private subnet can connect to services outside your VPC but external services cannot initiate a connection with those instances.


AWS Transit Gateway (TGW) is a highly scalable cloud router that connects your VPCs in the same region to each other, to on-premise networks, and even to the internet through one hub. With the use of multiple route tables for a single TGW, you can design hub and spoke routing for traffic inspection and enforcement of security policy across multiple VPCs.


AWS (Gateway Load Balancer (GWLB) is a transparent network gateway that distributes traffic (in a 3/5 tuple flow aware manner) to a fleet of virtual appliances for inspection. This is a regional load balancer that uses GWLB endpoints (GWLBe) to securely intercept data plane traffic within consumer VPCs in the same region.


In this workshop we will use all these components to test FortiGate CNF in an enterprise design.
AWS Common Architecture Patterns
While there are many ways to organize your infrastructure, there are two main ways to design your networking when using GWLB:
We will discuss this further below.
FortiGate CNF is a SaaS offering that on the backend uses FortiGates, AWS GWLB, and GWLB endpoints to intercept customer traffic and inspect this traffic transparently. As part of the deployment process for FortiGate CNF instances, the customer environment will need to implement VPC and ingress routing at the IGW to intercept the traffic to be inspected.
The FortiGate CNF security stack, which includes the AWS GWLB and other components, will be deployed in Fortinet managed AWS accounts. The details of the diagram are simply an example of the main components used in FortiGate CNF.
The following diagrams and paragraphs will explain what happens when customer traffic is received at the FortiGate CNF GWLB.


Decentralized designs do not require any routing between the protected VPC and another VPC through TGW. These designs allow simple service insertion with minimal routing changes to the VPC route table. The yellow numbers show the initial packet flow for a session and how it is routed (using ingress and VPC routes) to the GWLBe endpoint which then sends traffic to the FortiGate CNF stack. The blue numbers show the returned traffic after inspection by the FortiGate CNF stack.
Note: Any subnet where the GWLBe for the FortiGate CNF instance is to be deployed will need to have a specific tag name and value to be seen in the FortiGate CNF portal. Currently this is the tag name ‘fortigatecnf_subnet_type’ and tag value ‘endpoint’.








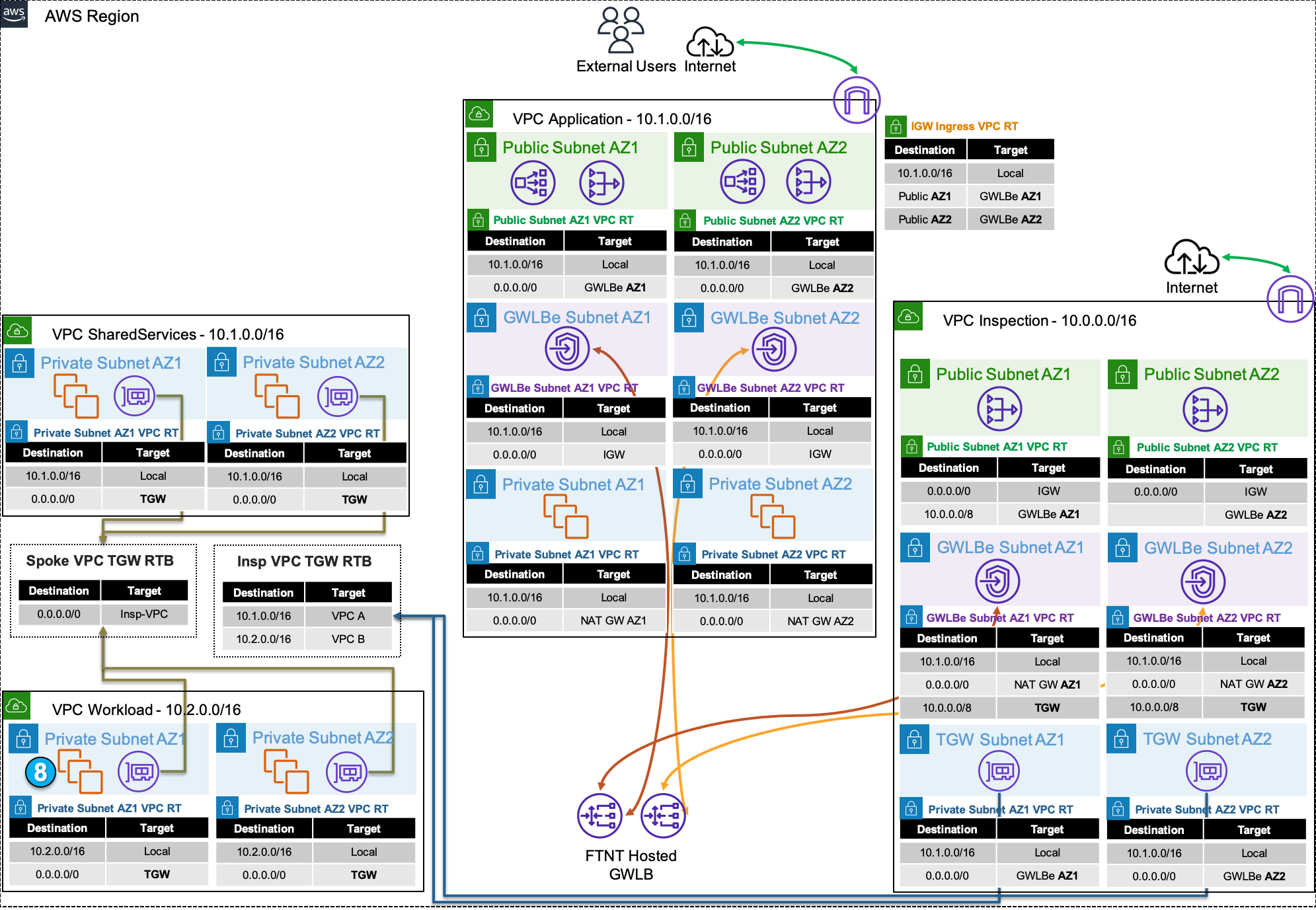
Centralized designs require the use of TGW to provide a simple hub and spoke architecture to inspect traffic. These can simplify east-west and egress traffic inspection needs while removing the need for IGWs and NAT Gateways to be deployed in each protected VPC for egress inspection. You can still mix a decentralized architecture to inspect ingress and even egress traffic while leveraging the centralized design for all east-west inspection.
The yellow numbers show the initial packet flow for a session and how it is routed (using ingress, VPC routes, and TGW routes) to the GWLBe which then sends traffic to the FortiGate CNF stack. The blue numbers (east-west) and purple numbers (egress) show the returned traffic after inspection by the FortiGate CNF stack.






For more examples of distributed and centralized models, please reference the examples on the FortiGate CNF Admin Guide.
FortiGate CNF Terminology
| Term | Description |
|---|
| CNF Console | The console in which you deploy CNF instances and manage policy sets |
| CNF Instance | A deployment of CNF resources in an auto scale group in the region of your choice |
| Policy Set | The group of FW rules, objects, and security profile groups that are assigned to one or many CNF Instance(s) |
| Security Profile Group | A group of Layer 7 inspection profiles such as DNS filter, and known bad IP blocking |




Subsections of Terraform Install and Deployment
- Log into your AWS account and navigate to the Console Home.
- Click on the AWS CloudShell icon on the console navigation bar


We are going to use the Terraform Version Manager to help install Terraform
Clone the Terraform Version Manager repository
git clone https://github.com/tfutils/tfenv.git ~/.tfenv


Make a new directory called ~/bin
mkdir ~/bin
Make a symlink for tfenv/bin/* scripts into the path ~/bin
ln -s ~/.tfenv/bin/* ~/bin
With the Terraform Version Manager installed, we can now install Terraform.
tfenv install


This will install the latest version of Terraform for you. Take note of the installed version of terrform. In this case, the default version is 1.5.3.
To make this version the default version, use the following commmand
tfenv use 1.5.3
Verify you are using the proper version of terraform
terraform -v


This concludes this section.
Info
Note: Make sure you are running this workshop in the intended region. The defaults are configured to run this workshop in us-west-2 (Oregon). Make sure your management console is running in us-west-2 (Oregon), unless you intend to run the workshop in a different FortiGate CNF supported region.


- Click on the AWS CloudShell icon on the console navigation bar


Clone a repository that uses terraform to create a distributed ingress workload vpc
git clone https://github.com/FortinetCloudCSE/FortiGate-AWS-CNF-TEC-Workshop.git
Change directory into the newly created repository for distributed_ingress_nlb
cd FortiGate-AWS-CNF-TEC-Workshop/terraform/distributed_ingress_nlb
Copy the terraform.tfvars.example to terraform.tfvars
cp terraform.tfvars.example terraform.tfvars


- Edit the terraform.tfvars file and insert the name of a valid keypair in the keypair variable name and save the file
Info
Note: Examples of preinstalled editors in the Cloudshell environment include: vi, vim, nano
Info
Note: AWS Keypairs are only valid within a specific region. To find the keypairs you have in the region you are executing the lab in, check the list of keypairs here: AWS Console->EC2->Network & Security->keypairs.
This workshop is pre-configured in the terraform.tfvars to run in the us-west-2 (Oregon) region.




Info
Note: You may change the default region in the terraform.tfvars file to another FortiGate CNF supported region if you don’t have a valid keypair in that region and you don’t want to create one for this workshop.




- Use “terraform apply –auto-approve” command to build the vpc. This command takes about 5 minutes to complete.
terraform apply --auto-approve


- When the command completes, verify “Apply Complete” and valid output statements.
- Make note of the Web Url (red arrow) for each instance and for the NLB that load balances between the Availability Zones.
- Make note of the ssh command (yellow arrow) you should use to ssh into the linux instances.
- Write down the Public IP address of the linux instance in AZ1. We are going to use that IP for our CNF external syslog server when we deploy Fortigate CNF.
- Bring up a local browser and try to access the Web Url. It will fail because these Web Servers are vulnerable and the security group only allows ssh (tcp port 22). We will fix this in the next task.
- Copy the “Outputs” section to a scratchpad. We will use this info throughout this workshop.




The network diagram for the distributed ingress vpc looks like this:


- This concludes this section.
IaC Discussion Points
Discussion Points During a Demo - Chapter 3
Fortinet provides a large library of infrastructure as code (IaC) templates to deploy baseline and iterate POC and production environments in public cloud. IaC support includes Terraform, Ansible, and cloud-specific services such as Azure ARM, AWS Cloudformation, and Google Deployment templates. Terraform Providers are available for several Fortinet products to insert and iterate running configuration.
For more information, review the following:
Advantages of Using AWS CloudShell for Deployment
AWS CloudShell is a browser-based shell that makes it easy to securely manage, explore, and interact with your AWS resources. CloudShell is pre-authenticated with your console credentials and common development and operations tools are pre-installed. CloudShell is available in all commercial AWS regions at no additional cost and provides an environment with preconfigured CLI tools and access to AWS services. CloudShell provides a temporary 1 GB storage volume that is deleted after 120 minutes of inactivity. CloudShell is a convenient method to deploy IaC templates for demonstrations and quick deployments.
AWS Cloudshell is a nice environment for deploying demo environments. However, for production environments, it is recommended to use a local workstation or a CI/CD pipeline. If your customer is asking about how to deploy Terraform in production, you can point them to the following resources:
Be sure to point out that the Fortinet Terraform templates are free to use and modify. These templates are designed to illustrate reference architectures in a demo environment only and may require modification to meet production requirements.
Key questions during your demo
When giving this TEC Workshop as a demo, the following questions will provide a basis for next steps and future meetings:
- Has your organization standardized on an IaC tool-set for infrastructure provisioning and iteration?
- How are the responsibilities for infrastructure assigned? Does cloud network fall under a DevOps, Cloud Networking, or Application Delivery team, as examples?
- What is organizations view on how IaC can improve workflows?
- Is workflow automation in cloud and cross-organizational collaboration important within your cloud business?
Deploy FortiGate CNF
This section will demonstrate how easy it is to deploy a FortiGate CNF instance into an existing VPC and redirect traffic to the CNF instance. The FortiGate CNF instance will be deployed into an account managed and owned by Fortinet. Traffic will be redirected into Gateway Load Balancer Endpoints (GWLBe) on ingress and egress. This will give the CNF Instance access to traffic flows and provide L4-L7 inspection and security features. The customer account will not be responsible for managing the FortiGate CNF instance. The FortiGate CNF instance will be managed by Fortinet and will be updated with the latest security features and bug fixes. The customer account will be responsible for managing VPC Route Tables to redirect traffic to the GWLBe endpoints.
IAM Permissions
The customer account will deploy a CloudFormation Template that creates an IAM Role that can be “assumed” by the FortiGate account. This “assumed” role provides IAM Permissions that allow the GWLBe’s to be installed into the customer VPC.
VPC Route Table Modifications
Once the FortiGate CNF instance and GWLBe’s are deployed, a customer would then modify VPC Route Tables to redirect traffic to the endpoints for inspection. Making these modifications to the route tables is a critical step in the deployment process. If the route tables are not modified correctly, traffic may NOT be redirected to the FortiGate CNF instance for inspection, or you could create asymmetric traffic flows, or you could create an expensive situation where traffic is crossing availability zone boundary’s unnecessarily.
Let’s get started!
Create FortiGate CNF Policy Set
Policies are rules that govern how traffic is handled by the firewall. Policies use address and service objects to build matching rules and security profiles to define what action is to be taken.
Policy sets are groups of rules. A single policy set is deployed to a firewall instance, but policy sets may be re-used across multiple firewall instances.
Each CNF instance uses a single policy set at a time, but a single policy set can be used by multiple FortiGate CNF instances. Objects can also be used across multiple policy sets.
Fortigate CNF can create dynamic address objects based on cloud native tags, fully qualified domain-names, or even geography based IP’s or malicious IPs provided by the Fortiguard service IP Database. This allows for dynamic security policies that can keep up with the dynamic nature of cloud infrastructure.
Deploy Centralized Egress VPC
This section provides instructions for deploying the centralized egress vpc using a provided Terraform template.
The template will create an Inspection VPC in dual availability zones with three (3) subnets in each availability zone. A jump box and a FortiManager will be deployed in the public subnet in the first availability zone.
In addition to the resources in the inspection vpc, two spoke VPC’s will be created and attached to the inspection vpc via a transit gateway. Subsequent tasks in this workshop will deploy a FortiGate CNF instance and associated endpoints to allow for traffic inspection of ingress, egress, and east-west traffic between the spoke VPCs.
The following network diagram illustrates the layout of the inspection vpc and spoke vpcs:


Subsections of Deploy Centralized Egress VPC
Info
Note: Make sure you are running this workshop in the intended region. The defaults are configured to run this workshop in us-west-2 (Oregon). Make sure your management console is running in us-west-2 (Oregon), unless you intend to run the workshop in a different FortiGate CNF supported region.


- Click on the AWS CloudShell icon on the console navigation bar


Info
Note: You installed terraform into the AWS Cloudshell environment in Task 1. If you destroyed the Cloudshell environment, you will need to install terraform again. See Task 1 for instructions.
Info
Note: You may have already cloned this repository in a previous task. If so, you can skip this step.
Clone a repository that uses terraform to create a distributed ingress workload vpc
git clone https://github.com/FortinetCloudCSE/FortiGate-AWS-CNF-TEC-Workshop.git
Change directory into the newly created repository for distributed_ingress_nlb
cd ~/FortiGate-AWS-CNF-TEC-Workshop/terraform/centralized_ingress_egress_east_west/
Copy the terraform.tfvars.example to terraform.tfvars
cp terraform.tfvars.example terraform.tfvars


- Edit the terraform.tfvars file and insert the name of a valid keypair in the keypair variable name and save the file
Info
Note: Examples of preinstalled editors in the Cloudshell environment include: vi, vim, nano
Info
Note: AWS Keypairs are only valid within a specific region. To find the keypairs you have in the region you are executing the lab in, check the list of keypairs here: AWS Console->EC2->Network & Security->keypairs.
This workshop is pre-configured in the terraform.tfvars to run in the us-west-2 (Oregon) region.




Info
Note: You may change the default region in the terraform.tfvars file to another FortiGate CNF supported region if you don’t have a valid keypair in that region and you don’t want to create one for this workshop.




- Use “terraform apply –auto-approve” command to build the vpc. This command takes about 5 minutes to complete.
terraform apply --auto-approve


- When the command completes, verify “Apply Complete” and valid output statements.
- Copy the “Outputs” section to a scratchpad. We will use this info throughout this workshop.


The network diagram for the centralized egress vpc looks like this:


- This concludes this section.
Task 11: Initialize FortiAnalyzer
Info
Note: Since this is a workshop, we will use the trial license for FortiManager and FortiAnalyzer. You must have know your credentials for your FortiCloud account to get through this task in the workshop. The trial license is valid for 15 days.
- In the next couple of tasks, we will initialize FortiManager and FortiAnalyzer. Let’s start with the FortiAnalzyer. Find the FortiAnalyzer IP address and instance ID from the output of the Terraform template you saved to your scratchpad. Be sure to accept the self-signed certificate presented by FortiAnalyzer.


- Login to FortiAnalyzer with the credentials you used to create your FortiCloud account.
- Click Free Trial
- Click Login with FortiCloud


- Scroll to the bottom of the “Terms” and click the box that Accepts the terms of the license.
- Click Accept


- This will cause the FortiAnalyzer to reboot and apply the license. This will take a minute.
Info
Note: If the FortiAnalyzer reboots to screen asking the user to attach an entitlement file, the FortiAnalyzer is unable to contact FortiCloud to verify the trial license. If this happens, rebooting the FortiAnalyzer from the AWS EC2 screen should resolve the problem.


- Once the FortiAnalyzer has rebooted, accept the self-signed certificate and login again with with the default credentials of admin and instance-id as password.


- Accept the defaults on the Setup screen and click Begin


- Accept the default hostname, unless you want to change it.


- Now change the default password (instance-id) to something more secure. This will log you out and force you to login again with the new password.




- Setup complete, click Finish


- This concludes this section.
Task 12: Initialize FortiManager
- In this task, we will initialize FortiManager. Find the FortiManager IP address and instance ID from the output of the Terraform template you saved to your scratchpad. Be sure to accept the self-signed certificate presented by FortiManager during initial login.


- Login to FortiManager with the credentials you used to create your FortiCloud account.
- Click Free Trial
- Click Login with FortiCloud


- Scroll to the bottom of the “Terms” and click the box that Accepts the terms of the license.
- Click Accept


- This will cause the FortiManager to reboot and apply the license. This will take a minute.
Info
Note: If the FortiManager reboots to screen asking the user to attach an entitlement file, the FortiManager is unable to contact FortiCloud to verify the trial license. If this happens, rebooting the FortiManager from the AWS EC2 screen should resolve the problem.


- Once the FortiManager has rebooted, accept the self-signed certificate and login again with the default credentials of admin and instance-id as password.


- Accept the defaults on the Setup screen and click Begin


- Accept the default hostname, unless you want to change it.
- Click Next


- Now change the default password (instance-id) to something more secure. This will log you out and force you to login again with the new password.


- This concludes this section.
Task 13: Deploy FortiGate CNF and Gateway Load Balancer Endpoints
The network diagram for the centralized egress vpc (included here for convenience) looks like this:


Prerequisite: You must have completed “Task 4: Subscribe to FortiGate CNF in AWS Marketplace” before continuing. This task will only need to be completed once per AWS account.
Prerequisite: You must have completed ““Task 5: Onboard an AWS account to FortiGate CNF” before continuing. This task will only need to be completed once per AWS account.
In the FortiGate CNF console, navigate to CNF instances and click New.


Provide a name for the CNF instance. This workshop example uses corp-us-west-2-cnf.
Select us-west-2 for the region.
Click FortiManager mode
Under Logging Options, make sure Internal S3 Logging is unchecked
select FortiAnalyzer for the external logging and insert the FortiAnalyzer IP from your scratchpad.
Under Endpoints, click New to create a GWLB Endpoint for AZ1


Provide a Name for the endpoint this workshop uses corp-us-west-2-endp-az1
Use the dropdown to select the account you onboarded in Task 5
Choose the tec-cnf-lab-inspection-vpc from the dropdown for VPC ID
Uncheck Select from all subnets and choose cnf-dist-rec-app-fwaas-az1 from the dropdown
Click OK to continue


Under Endpoints, click New to create a GWLB Endpoint for AZ1
Provide a Name for the second endpoint. This workshop uses corp-us-west-2-endp-az2
Use the dropdown to select the account you onboarded in Task 5
Choose the tec-cnf-lab-inspection-vpc from the dropdown for VPC ID
Uncheck Select from all subnets and choose cnf-dist-rec-app-fwaas-az2 from the dropdown
Click OK to continue


- The “Create CNF” screen should look like this
- Click OK to continue


- The CNF Instance should show up as active after roughly 10 minutes (Now is a great time for a break :) ). Then you can select and edit it to deploy endpoints and assign a policy set.


- Approximately 10 minutes later…


- To validate all GWLBe endpoints have been deployed and are active, select and edit the CNF instance and click Edit.


- To view the GWLBe endpoints on the Configure Endpoints section of the wizard. Verify that both endpoints are active and have a status of Active.


- Click Troubleshooting. Here you can see that FortiManager status is currently disabled. We will connect the FortiManager in a later task. You can also see that allow_all policy is currently active.
- Click Finalize to continue


- This concludes this section.
Task 14: Modify VPC Route Tables to direct egress traffic to Fortigate CNF for inspection
- The initial deployed terraform template deploys an inspection VPC with a FortiManager and FortiAnalyzer and a couple of customer or workload VPC’s connected to a Transit Gateway (TGW). This design allows outbound traffic to egress through the NAT Gateways and the option to add various types of AWS load balancers for ingress traffic. The interesting aspect of this design pattern allows many VPC’s to share a single FortiGate CNF instance. This design pattern is depicted in this picture:


- The default VPC route tables route the egress traffic to the NAT Gateways and the ingress traffic is directed to the TGW for each Spoke VPC. Traffic that is going to the FortiAnalzyer, FortiManager and Jump Box are routed locally to the EIP associated with each device. This design is a working design, but does not give the FortiGate CNF instance the opportunity to inspect the traffic. We need to change the VPC route tables to force egress and ingress traffic through the GWLB Endpoints we created in the previous task. This give the FortiGate CNF instance the opportunity to inspect ingress and egress traffic. The modified design will look like this:


Note: Changes to the route tables are in RED.
- The first change will be to the public route table in the inspection VPC in AZ1.
- Log into your AWS account and navigate to the Console Home.


- First, we need to understand which CNF Endpoint is deployed in each AZ. To do this, click on “Endpoints” in the left pane.


- Then choose one of the CNF Endpoints and click subnets in the lower window.


From this screen, you can see the subnet id where the Endpoint is deployed. You have a few options here.
- You could navigate to the subnet tab on the left navigation pane and check which AZ that subnet is in using the subnet id.
- You might notice that the IP address is 10.0.1.54. If you check the network diagram above, you can see that the 10.0.1.0/24 CIDR is in AZ1.
- In this case, I included the AZ in the name of the name of the subnet “tec-cnf-lab-inspection-fwaas-az1-subnet” in the terraform that deployed the workshop VPC. It’s a useful hint in this case, but that may not be true in other VPC environments.
- Nevertheless, this endpoint (vpce-xxxx0c92) is deployed in AZ1 and (vpce-xxxxdd75) is deployed in AZ2.
- You might want to add this info to your scratchpad.
Now let’s modify the route tables. Click on “Route tables” in the left pane


- Highlight the Inspection VPC Public Route table named “tec-cnf-lab-inspection-public-rt-az1”.
- Click on the “Routes” tab at the bottom.
- Click on “Edit routes”.




- Modify the target for the East-West Supernet CIDR to point to the GWLB Endpoint in AZ1. This will redirect ingress traffic to the GWLB Endpoint for inspection.
- Click Save changes


- Now do the same for the Inspection VPC Public Route table in AZ2. Click Route Tables


- Highlight the Inspection VPC Public Route table named “tec-cnf-lab-inspection-public-rt-az2”.
- Click on the “Routes” tab at the bottom.




- Now let’s redirect egress traffic coming from the TGW to the GWLB Endpoint for inspection. Click Route Tables


- Highlight the Inspection VPC Public Route table named “tec-cnf-lab-inspection-private-rt-az1”.
- Click on the “Routes” tab at the bottom.




- Now let’s do the same for the egress traffic in AZ2. Click Route Tables


- Highlight the Inspection VPC Public Route table named “tec-cnf-lab-inspection-private-rt-az2”.
- Click on the “Routes” tab at the bottom.




IaC Discussion Points
The Centralized Egress VPC is commonly used when there is a strong desire to control egress traffic through a common set of NAT Gateways contained within an common inspection VPC. The benefits of this design is that you control the egress point of all connected Spoke VPC’s through a central VPC with a single set of NAT Gateways. There must be a single NAT Gateway per Availability Zone within the inspection VPC, which have an hourly cost. The spoke VPC’s are connected to the inspection VPC via a Transit Gateway. The Transit Gateway is a regional resource and has a monthly cost.
Discussion Points During a Demo - Chapter 8
The same discussion points apply to this chapter as in Chapter 3. These discussion points are repeated here for convenience.
Fortinet provides a large library of infrastructure as code (IaC) templates to deploy baseline and iterate POC and production environments in public cloud. IaC support includes Terraform, Ansible, and cloud-specific services such as Azure ARM, AWS Cloudformation, and Google Deployment templates. Terraform Providers are available for several Fortinet products to insert and iterate running configuration.
For more information, review the following:
Advantages of Using AWS CloudShell for Deployment
AWS CloudShell is a browser-based shell that makes it easy to securely manage, explore, and interact with your AWS resources. CloudShell is pre-authenticated with your console credentials, and common development and operations tools are pre-installed. CloudShell is available in all commercial AWS regions at no additional cost and provides an environment with preconfigured CLI tools and access to AWS services. CloudShell provides a temporary 1 GB storage volume that is deleted after 120 minutes of inactivity. CloudShell is a convenient method to deploy IaC templates for demonstrations and quick deployments.
AWS Cloudshell is a nice environment for deploying demo environments. However, for production environments, it is recommended to use a local workstation or a CI/CD pipeline. If your customer is asking about how to deploy Terraform in production, you can point them to the following resources:
Be sure to point out that the Fortinet Terraform templates are free to use and modify. These templates are designed to illustrate reference architectures in a demo environment only and may require modification to meet production requirements.
Key questions during your demo
When giving this TEC Workshop as a demo, the following questions will provide a basis for next steps and future meetings:
- Has your organization standardized on an IaC tool-set for infrastructure provisioning and iteration?
- How are the responsibilities for infrastructure assigned? Does cloud network fall under a DevOps, Cloud Networking, or Application Delivery team, as examples?
- What is organizations view on how IaC can improve workflows?
- Is workflow automation in cloud and cross-organizational collaboration important within your cloud business?






















































































































































































































