Task 1 - East-West ZTNA traffic
East-West inspection
Now that Server policy is all setup, for microsegmentation within trusted network using ZTNA we need to edit the ZTNA profile. Also, since FortiWeb has a firewall we will be using a firewall policy to prevent traffic between trusted network.
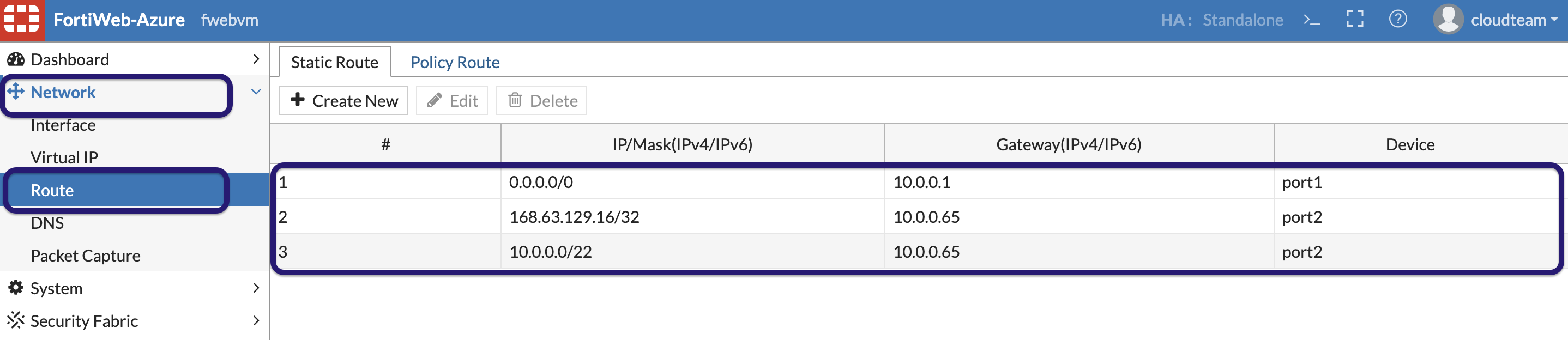
lets create a static route to get to the internal VNET through port2 in Network » Route » Static route.
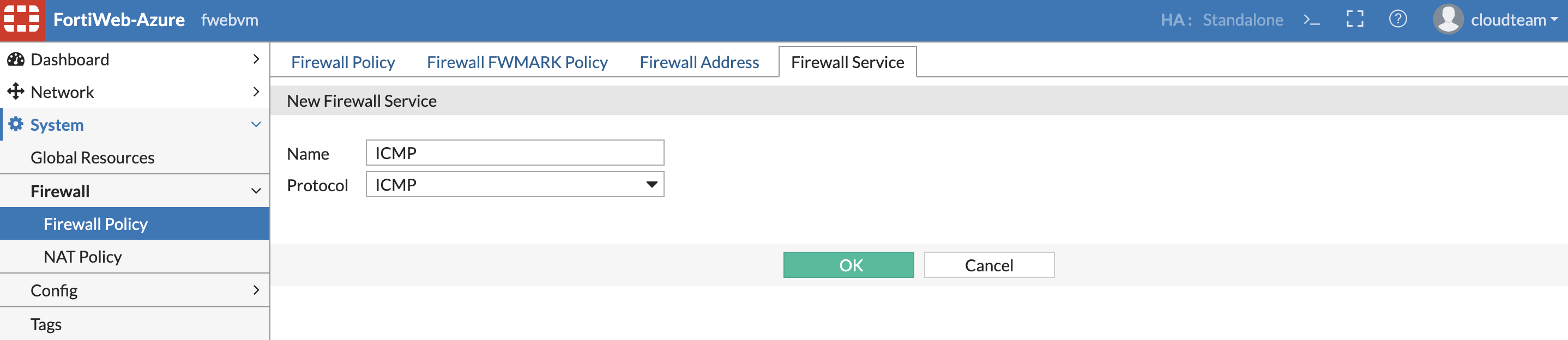
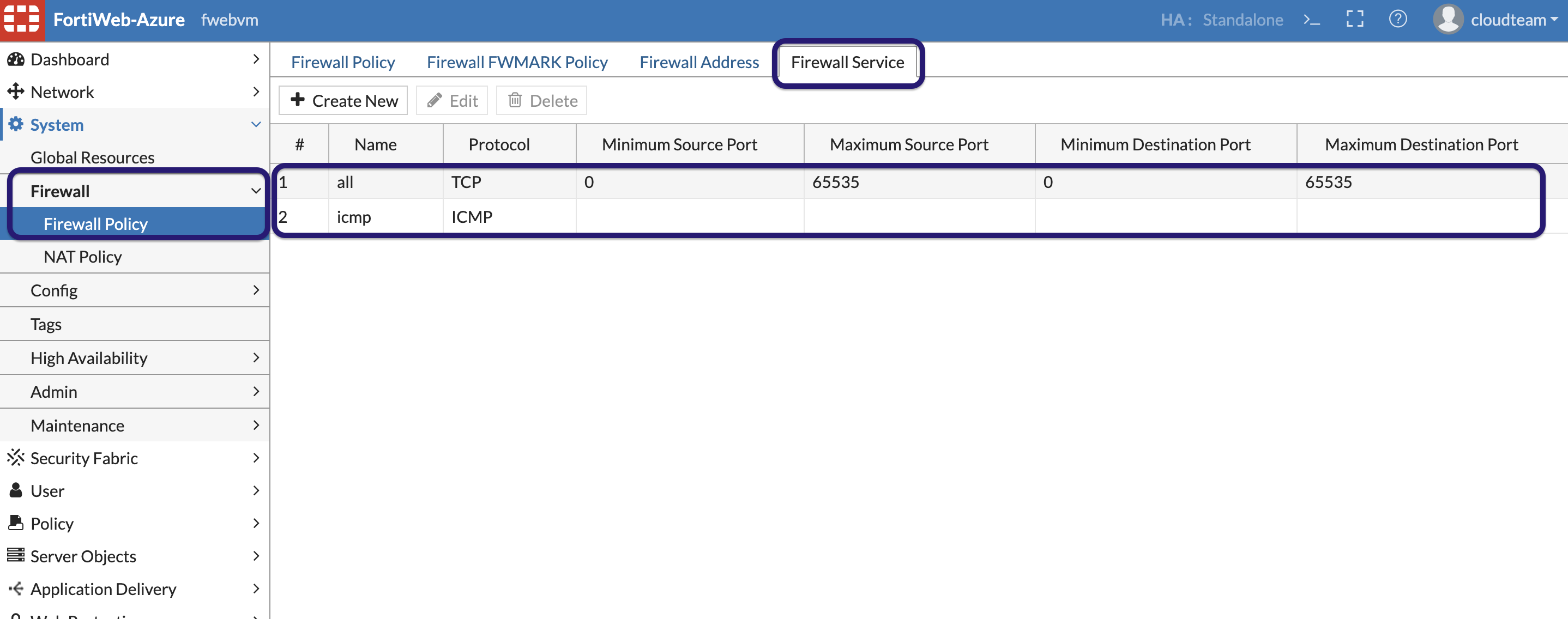
Also Lets create a firewall policy. In System » Firewall » Firewall Policy » Firewall Service.
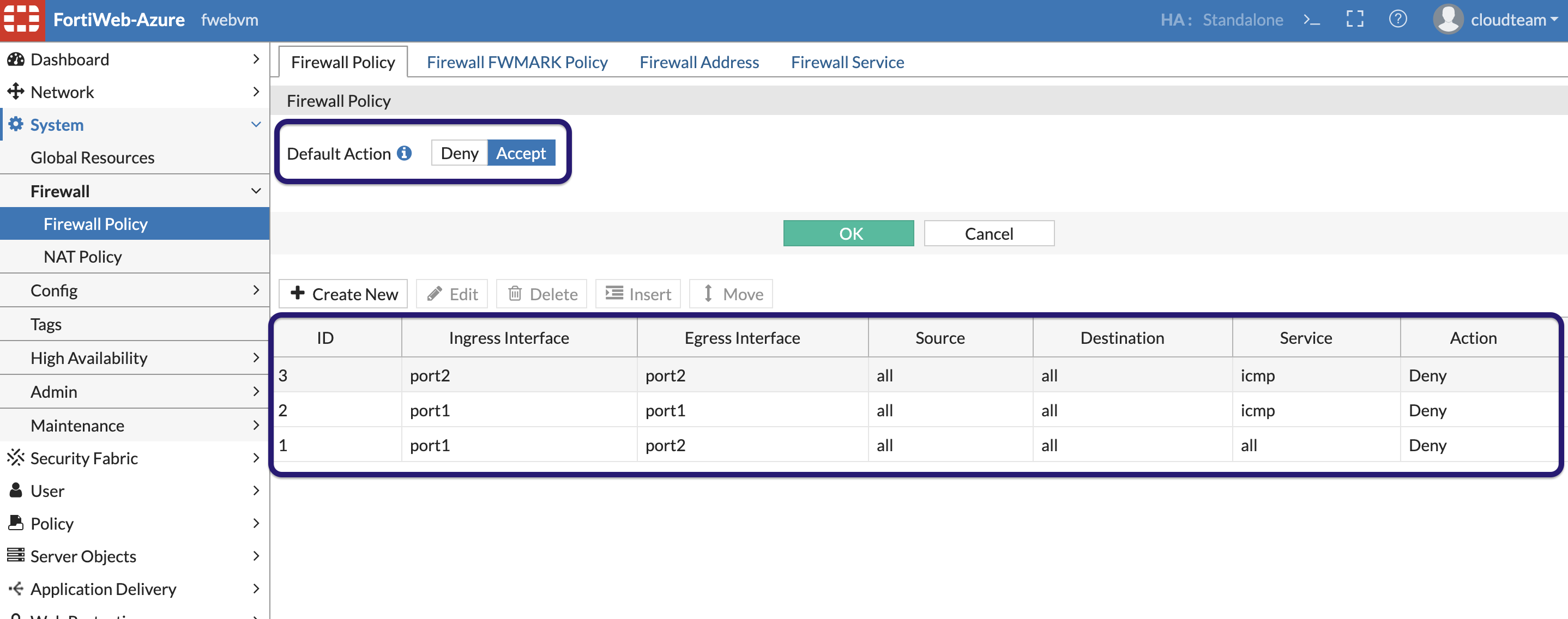
To create a firewall policy , set the default action to “Accept” also create policies as shown below to deny the icmp traffic and also all Port1 to port2 traffic.
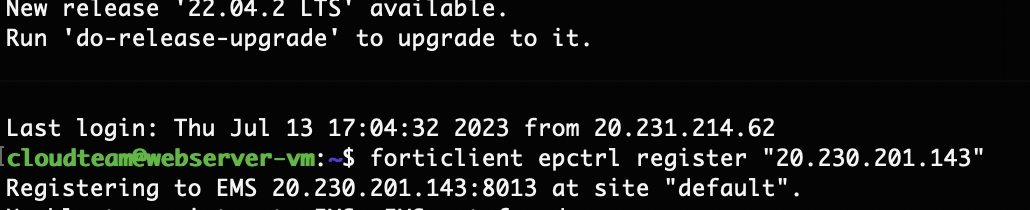
SSH to the webserver_public_ip to register it to FortiEMS using the below command. forticlient_ems_server_public_ip can be found in Terraform output log.
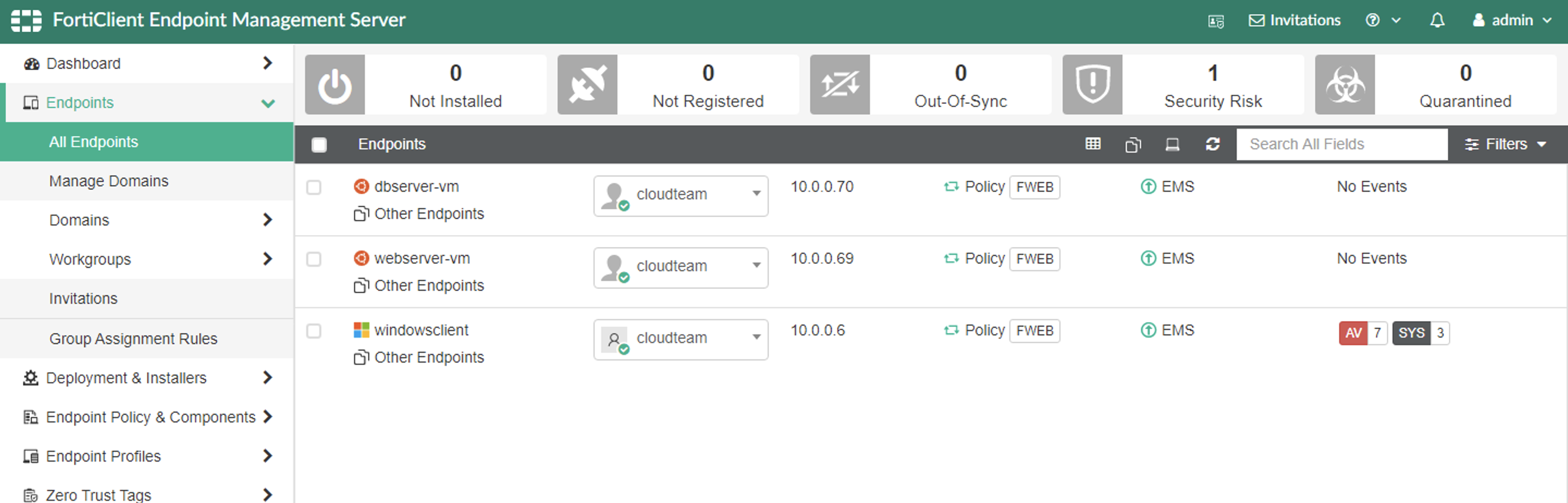
Once registered you should see the WebServer and APIServer on FortiEMS Endpoints module.
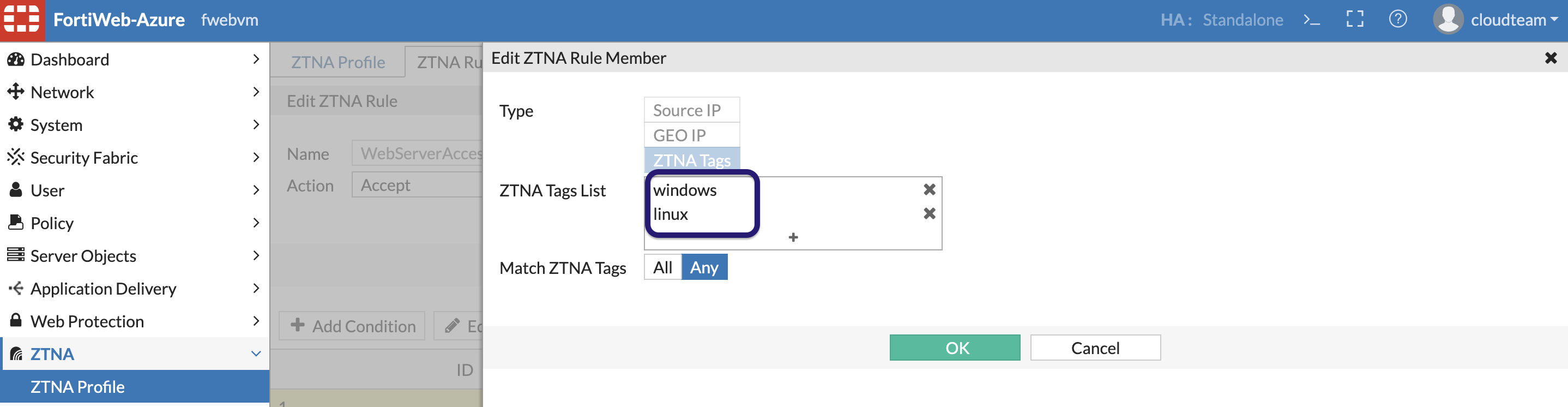
forticlient epctrl register "<forticlient_ems_server_public_ip>"Now in ZTNA profile, update the already created ZTNA rule to add Linux tag.
Linux VM is already connected to the EMS. You can check endpoints connected to EMS.
Now SSH to the other trusted Linux VM (IP address is in Terraform output) to get to the API server. once logged in type the below command.
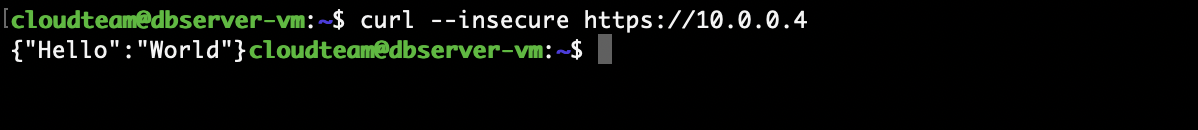
curl --insecure https://10.0.0.4curl --insecure https://10.0.0.4/docs
You should see hello world response from the first command and also swagger html as a response from the /docs
Now try the same to hit the trusted server directly.
curl --insecure https://10.0.1.5curl --insecure https://10.0.1.5/docs