Task 2: Configure FGSP
After the FortiGate NVA deployments are complete, the next step is to configure FortiGate Session Life Support FGSP on both FortiGates to enable session sync to support the Active-Active architecture.
Tip
You will open a browser session to each FortiGate, the FortiGate GUI defaults to a 5 minute “Idle timeout”. Avoid continually logging in by setting the idle timeout to 60 minutes in System–> Settings:Administration Settings:Idle timeout
To access the CLI on your FortiGate NVAs, following these steps:
From your assigned Resource Group “vwanxx-training”, navigate to your vWAN “vwanxx-training_VWAN” and then your hub “vwanXX-eastus-vHub1_VHUB”
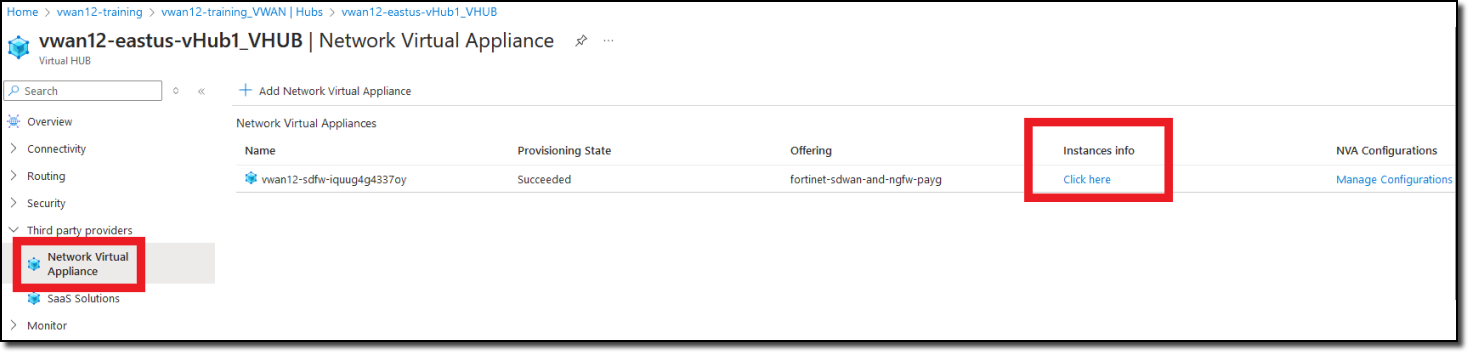
Click Network Virtual Appliance in the left-hand navigation
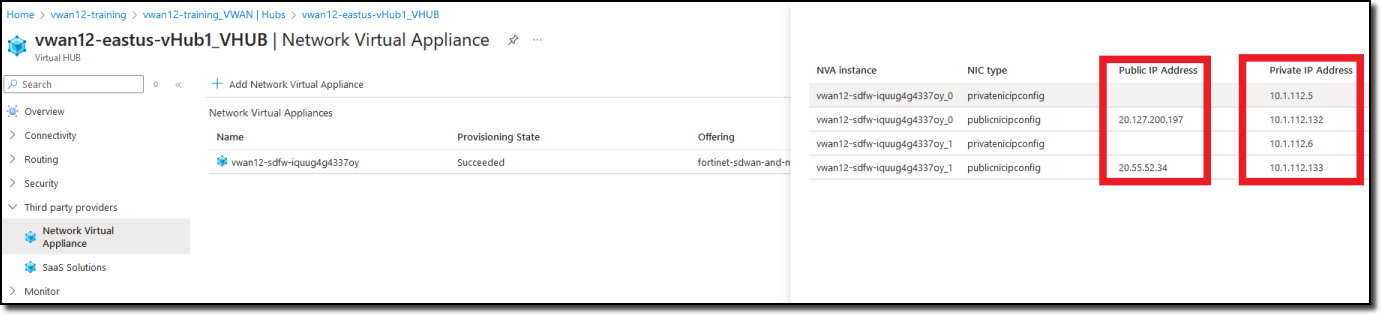
Click “Click here” link under “Instances info” in the right-hand “Network Virtual Appliances” pane
Note FortiGate Public IP and Private IP addresses
Open a browser tab to each FortiGate using the Public IP address of each FortiGate
Configure FGSP
Open a CLI session on each FortiGate
Enter the blocks of CLI commands on each FortiGate.
On FortiGate ending with _0 configure the peerip address with the port2 private IP address of the FortiGate ending with _1.
Warning
If the IP address of port2 on FortiGate ending _1 is not 10.1.112.7 replace the peerip below with the port2 private IP address of the FortiGate ending with _1Copy these CLI commands to notepad or similar tool to update the peerip address, if required.
config system standalone-cluster config cluster-peer edit 1 set peerip 10.1.112.7 next end set standalone-group-id 1 set group-member-id 1 endAnswer “y” to the “Do you want to continue? (y/n)” prompt
Changing standalone-group-id or group-member-id will potentially affect FGSP traffic.Please first make sure the member is isolated from FGSP cluster properly.Do you want to continue? (y/n)
config system ha set session-pickup enable set session-pickup-nat enable set session-pickup-connectionless enable set override disable endOn FortiGate ending with _1 configure the peerip address with the port2 private IP address of the FortiGate ending with _1.
Warning
If the IP address of port2 on FortiGate ending _0 is not 10.1.112.6 replace the peerip below with the port2 private IP address of the FortiGate ending with _0Copy these CLI commands to notepad or similar tool to update the peerip address, if required.
Warning
Notice that the group-member-id is 2 in the CLI commands below
config system standalone-cluster config cluster-peer edit 1 set peerip 10.1.112.6 next end set standalone-group-id 1 set group-member-id 2 endAnswer “y” to the “Do you want to continue? (y/n)” prompt
Changing standalone-group-id or group-member-id will potentially affect FGSP traffic.Please first make sure the member is isolated from FGSP cluster properly.Do you want to continue? (y/n)
config system ha set session-pickup enable set session-pickup-nat enable set session-pickup-connectionless enable set override disable end
FGSP is now configured and the FortiGates will share session information.
Continue to Chapter 4 - Task 3: VNET-to-VNET Traffic