Subsections of fortigate-aws-ha-dualaz-terraform
Introduction
Welcome
The purpose of this site is to provide a quick start guide for using Infrastructure as Code (IaC) templates located in the repo fortigate-aws-ha-dualaz-terraform.
Reference the prerequisites and deployment sections on this site to get started.
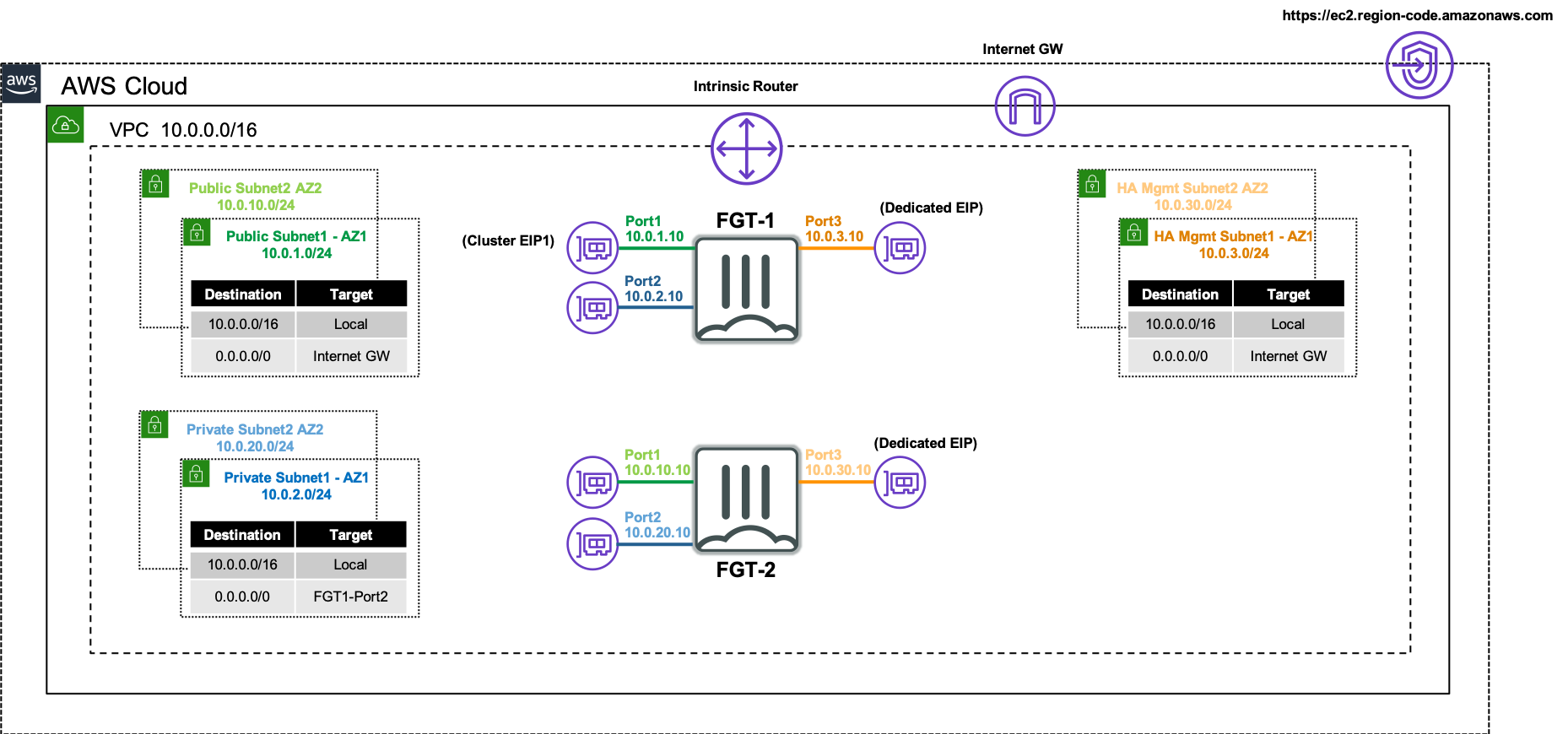
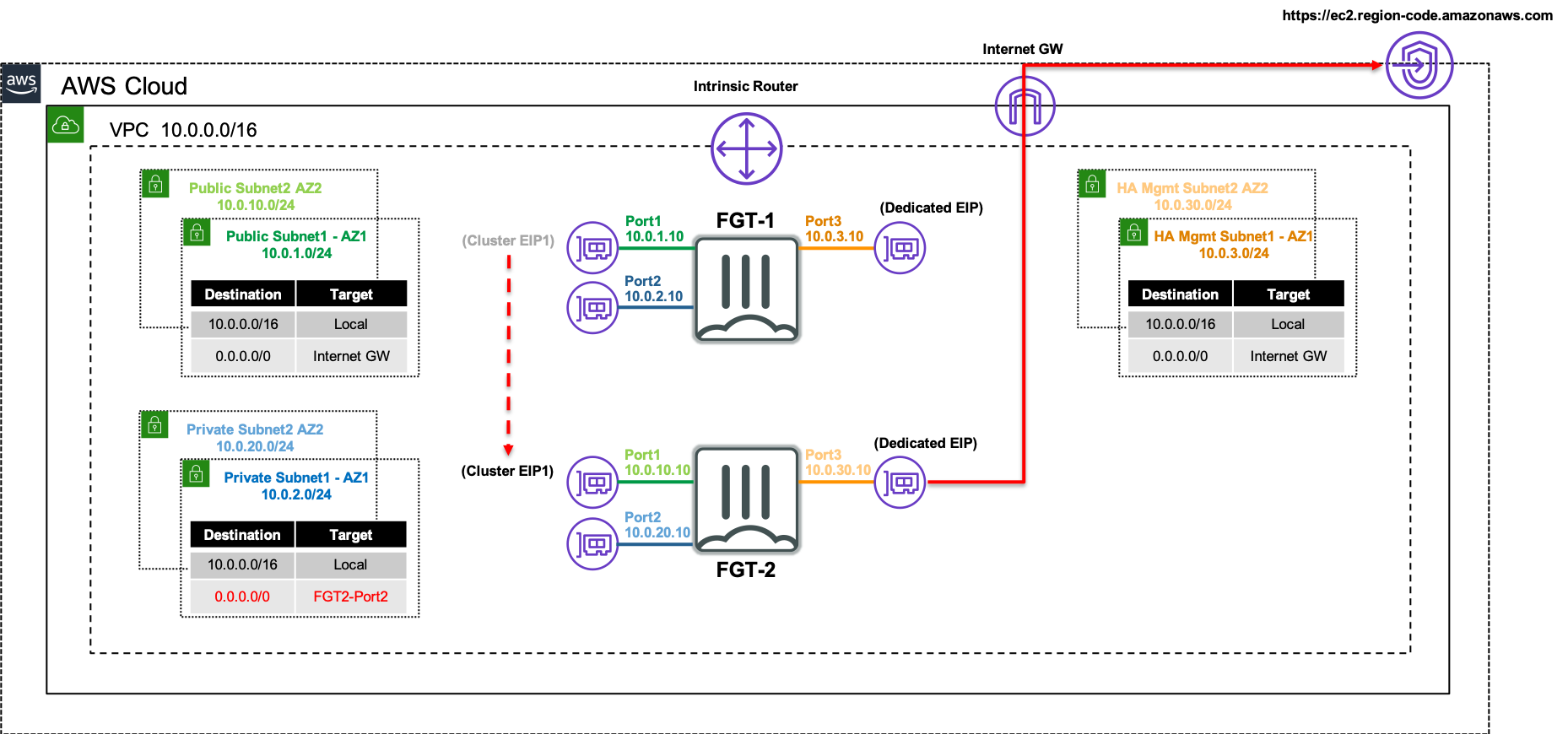
For detailed documentation on FGCP in AWS, walk through of a post deployment failover, and additional use cases, please reference CSE Team FGCP in AWS.
For other documentation needs such as FortiOS administration, please reference docs.fortinet.com.
Prerequisites
Before attempting to create a stack with the templates, a few prerequisites should be checked to ensure a successful deployment:
An AMI subscription must be active for the FortiGate license type being used in the template.
The solution requires 3 EIPs to be created so ensure the AWS region being used has available capacity. Reference AWS Documentation for more information on EC2 resource limits and how to request increases.
If BYOL licensing is to be used, ensure these licenses have been registered on the support site and license files downloaded locally.
Ensure that all of the PublicSubnet’s and HAmgmtSubnet’s AWS route tables have a default route to an AWS Internet Gateway. Reference AWS Documentation for further information. Otherwise you must set the variable only_private_ec2_api to ’true’.
Deployment
Once the prerequisites have been satisfied proceed with the deployment steps below.
- Clone this repo with the command below.
git clone https://github.com/FortinetCloudCSE/fortigate-aws-ha-dualaz-terraform.git- Change directories and modify the terraform.tfvars file with your credentials and deployment information.
Note
In the terraform.tfvars file, the comments explain what inputs are expected for the variables. For further details on a given variable or to see all possible variables, reference the variables.tf file.
cd fortigate-aws-ha-dualaz-terraform/terraform
nano terraform.tfvars- When ready to deploy, use the commands below to run through the deployment.
terraform init
terraform validate
terraform apply --auto-approve- When the deployment is complete, you will see login information for the FortiGates like so.
Apply complete! Resources: 33 added, 0 changed, 0 destroyed.
Outputs:
fgt_login_info = <<EOT
# fgt username: admin
# fgt initial password: i-0eb689028cc992e41
# cluster login url: https://13.56.40.46
# fgt1 login url: https://52.8.158.219
# fgt2 login url: https://54.241.49.19
# tgw_creation: no
EOT