Task 1: Find Vulnerability with Burp Suite
| Goal | Find vulnerability with Burp Suite |
| Task | Activate Burp Suite and use it to scan Juice Shop |
| Verify task completion | You will see a Server Response, indicating an SQLITE error. |
Burp Suite gives us a quick and easy way to query targeted sites.
Open a terminal window from your Kali desktop, and type:
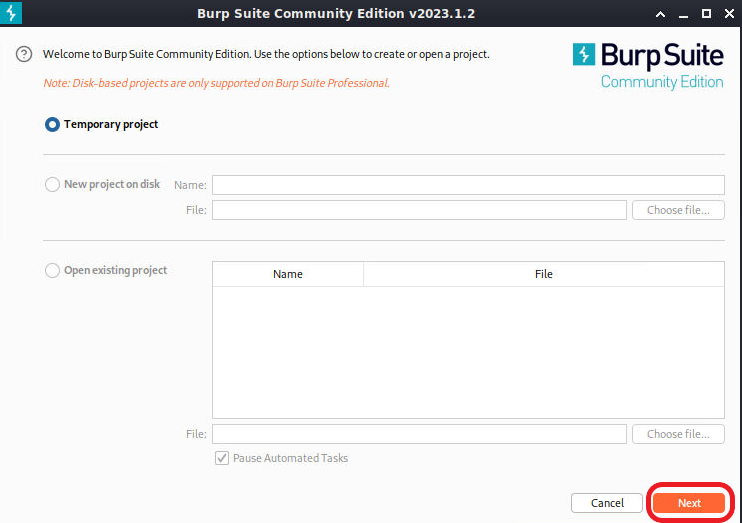
burpsuiteBurp Suite will pop up. Accept all warnings and EULAs. Leave Temporary Project selected and click Next
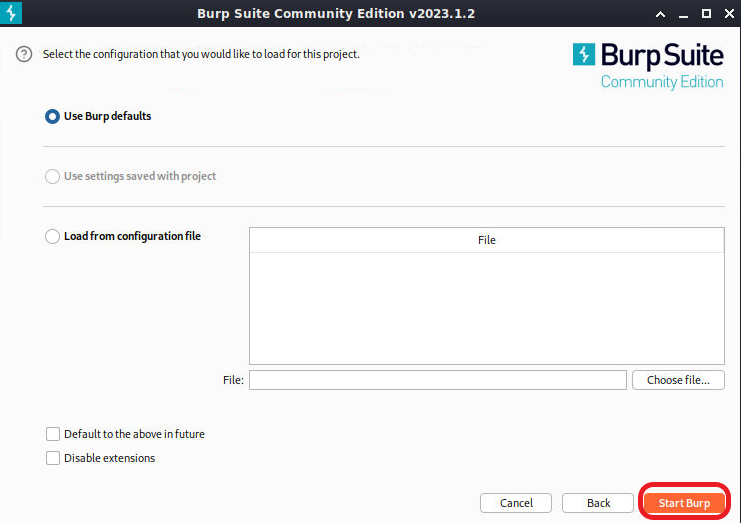
Leave “Use Burp defaults” selected and click Start Burp.
Accept the warning that Burp Suite is out of date and then select settings at the top right of the screen.
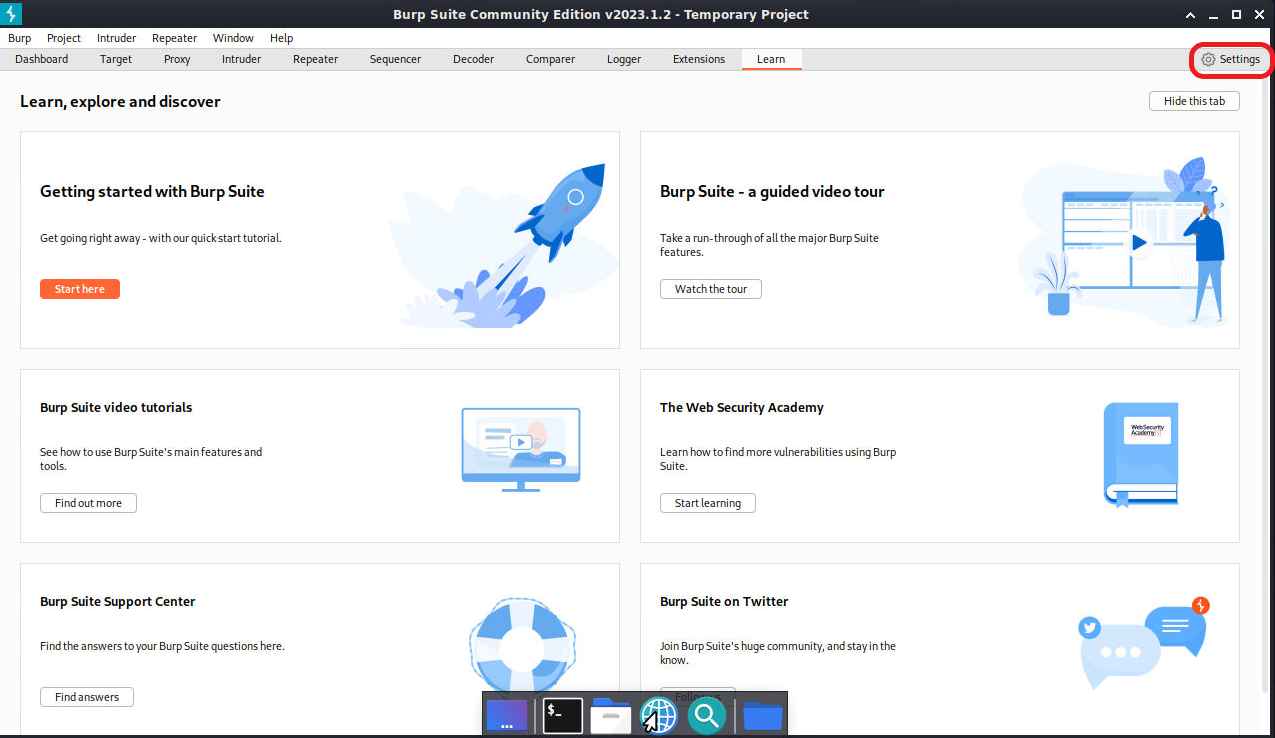
In the settings menu, select Burp’s browser. Under Browser running check the box for “Allow Burp’s browser without a sandbox”
Note
Once the button is clicked, just close the settings menu. There is no need to save.
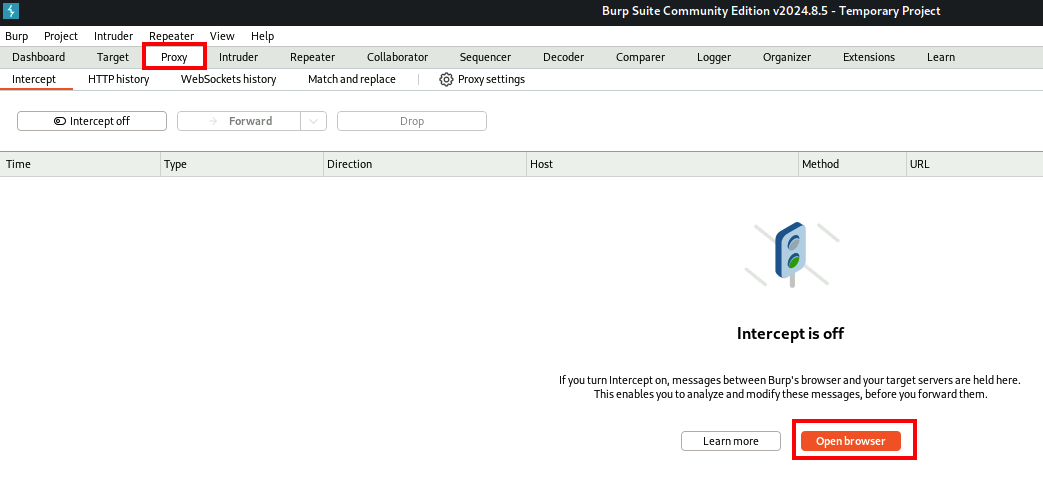
Click on the Proxy tab at the top of the Burp Suite screen. This will bring you to the Intercept screen. Click on Open Browser.
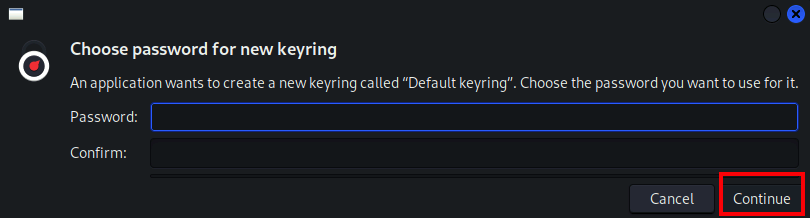
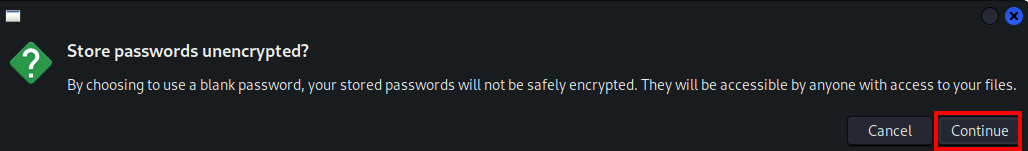
- Click Continue and then continue to NOT use a password for Burpsuite password encryption
- Click Continue and then continue to NOT use a password for Burpsuite password encryption
In the browser URL bar, input
https://<FortiAppSecStudentID>.fwebtraincse.comand hit enter. This will bring you to the juice shop home page.Minimize the browser and go back to the Burpsuite console and click on the HTTP History tab under Proxy.
- Scroll down the list until you find a URL labeled "/rest/products/search?q=.
- Select this line and right click. Then click on Send to Repeater.
- This will allow us to manipulate the requests in order to do a little nefarious recon.
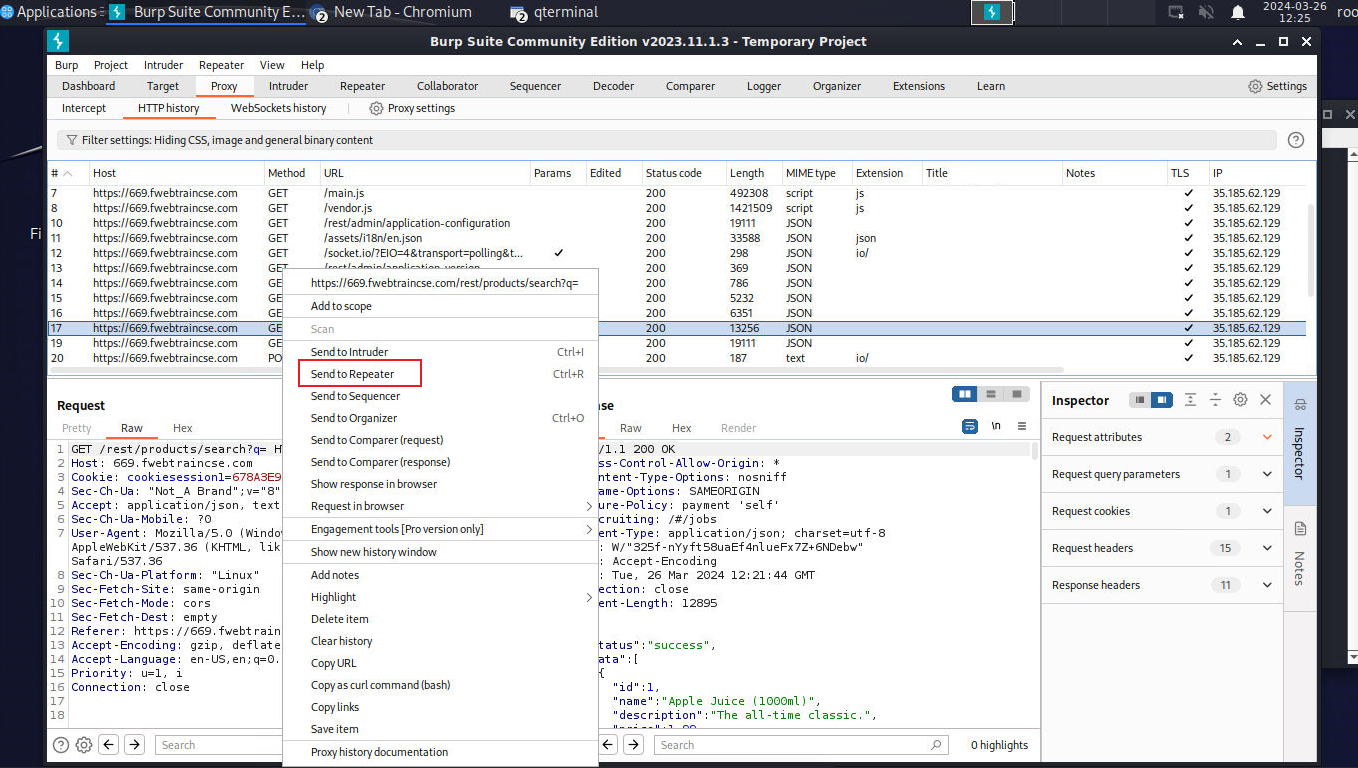
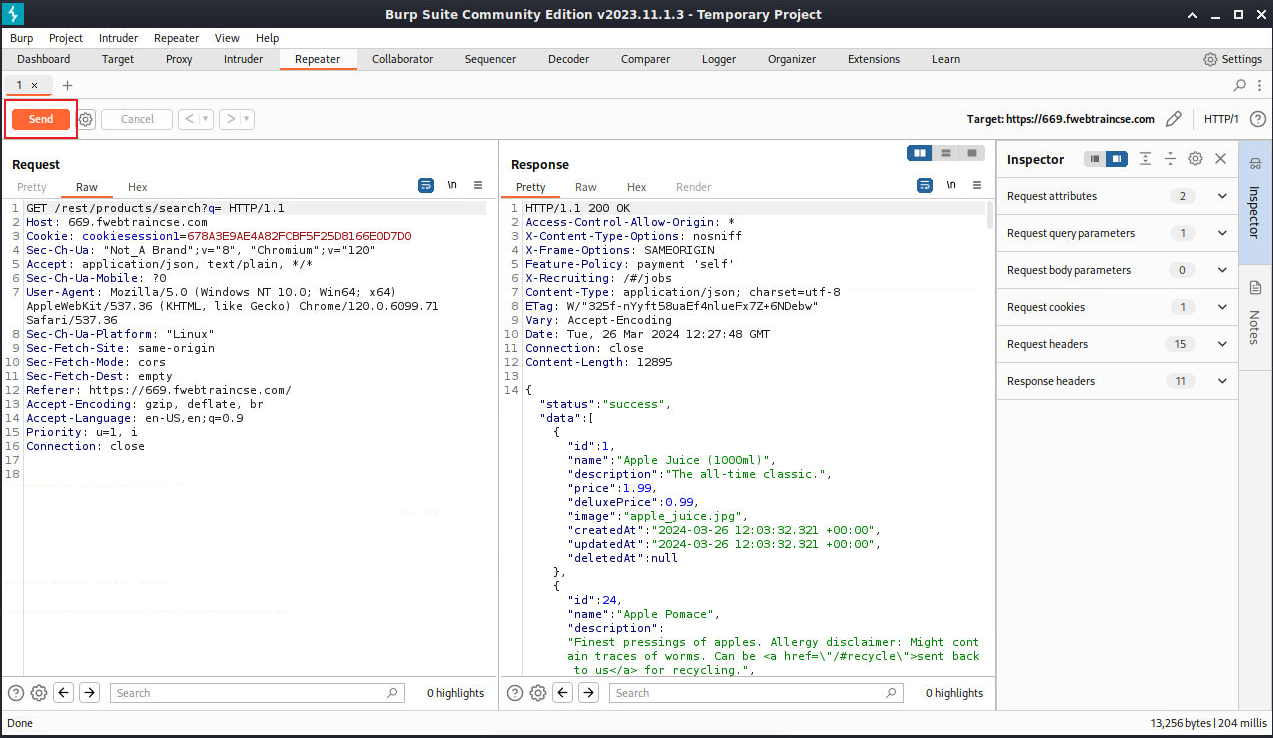
At the top of Burp Suite, Click on the Repeater Tab.
- You will see the request we just sent.
- Now click on the Send Button. This will populate the Response area.
Now we are going to modify our query a bit. We will intentionally send an incomplete input in order to generate an error.
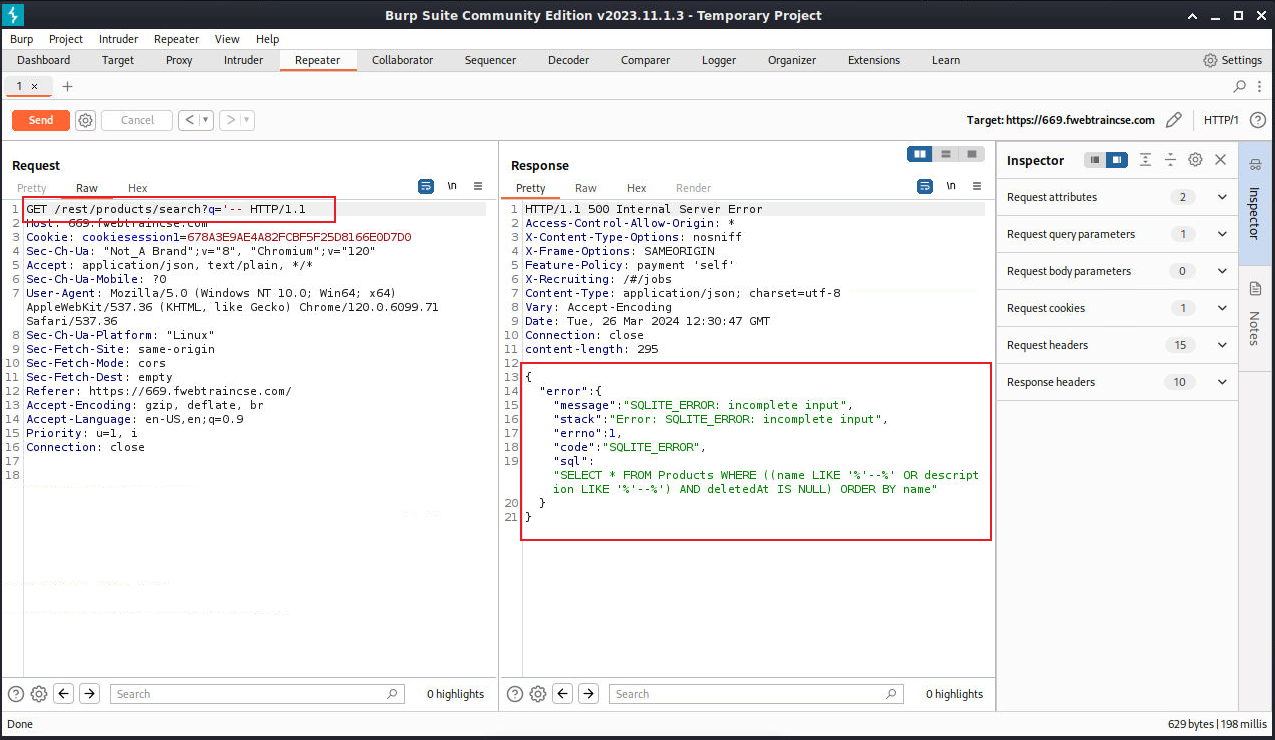
- Click on the First line in the Raw request and append
'--to the end of the GET request. - The GET should now look like
/rest/products/search?q='---. Click Send. - We will now see an error in the Response section.
- This error tells us that the database is SQLITE and uncovers a vulnerability.
Info
It's worth mentioning that the standard signature based Web Protection Profile did not catch this attempt. - If Machine Learning were enabled, this would not have succeeded. - Instead, it would have been identified as an anomaly and then passed to the threat engine where it would have been identified as an SQL Injection attempt. - We are not using ML in this lab, ML will be discussed in section 6- Click on the First line in the Raw request and append