Task 4 - Verify Firewall
| Goal | Ensure proper traffic flow via FortiGate for North/South and East/West traffic from Application servers |
| Task | SSH to applications and run ping tests between local and remote servers. Configure FortiGate policies to allow the traffic |
| Verify task completion | When complete, you should be able to ping between the application servers in different VPCs as well as ping the Remote Server from Application servers |
Info
Prior to starting this section, log into FortiGate 1 and ensure that you turned the remote IPsec tunnel back up.
Verify traffic
The Star topology in GCP NCC ensures that edge spokes can’t talk to one another directly. We set up the FortiGates as Center spokes, the application spokes must now traverse the Fortigate for inter-vpc communication or North/South connectivity to remote sites.
- Navigate back to the application (peered) project
- Using the Hambuger menu on the top left of the screen, navigate to Compute Engine > VM instances
- Open the details for each VM and click on SSH to open SSH-in-browser sessions for both.
- Start a ping from server 1 to server 2
ping 10.20.0.2This should fail.
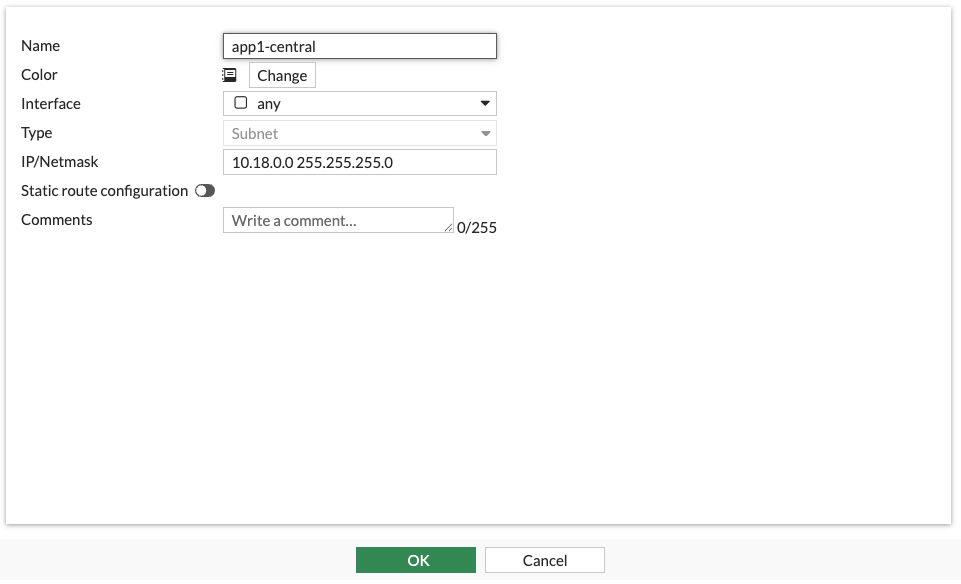
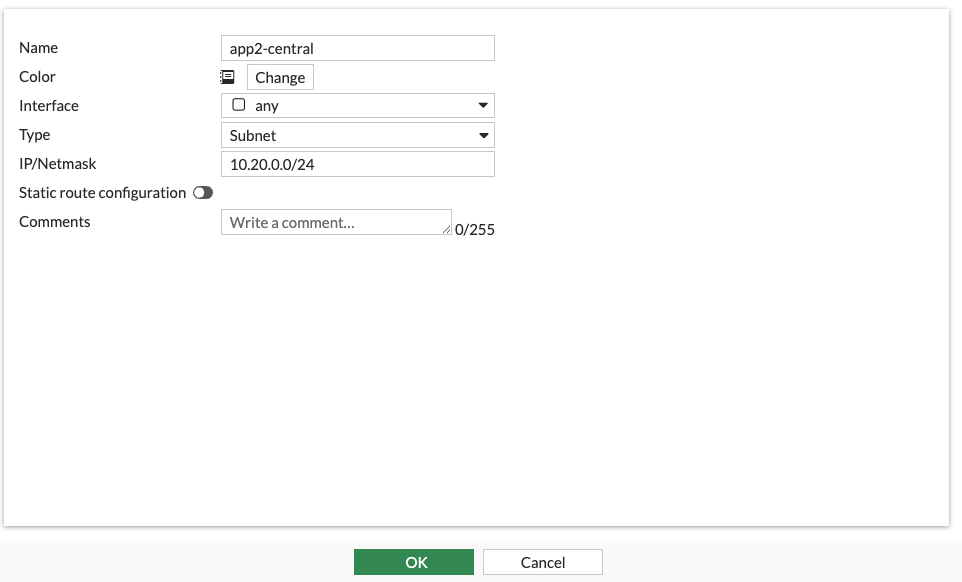
Create Address objects for the subnets containing the two servers.
- Navigate to Fortigate GUI
https://<fortigate1 public ip>:8443in your browser - Navigate to Policy & Objects > Addresses
- Click Create and add an address for each Central CIDR
- Navigate to Fortigate GUI
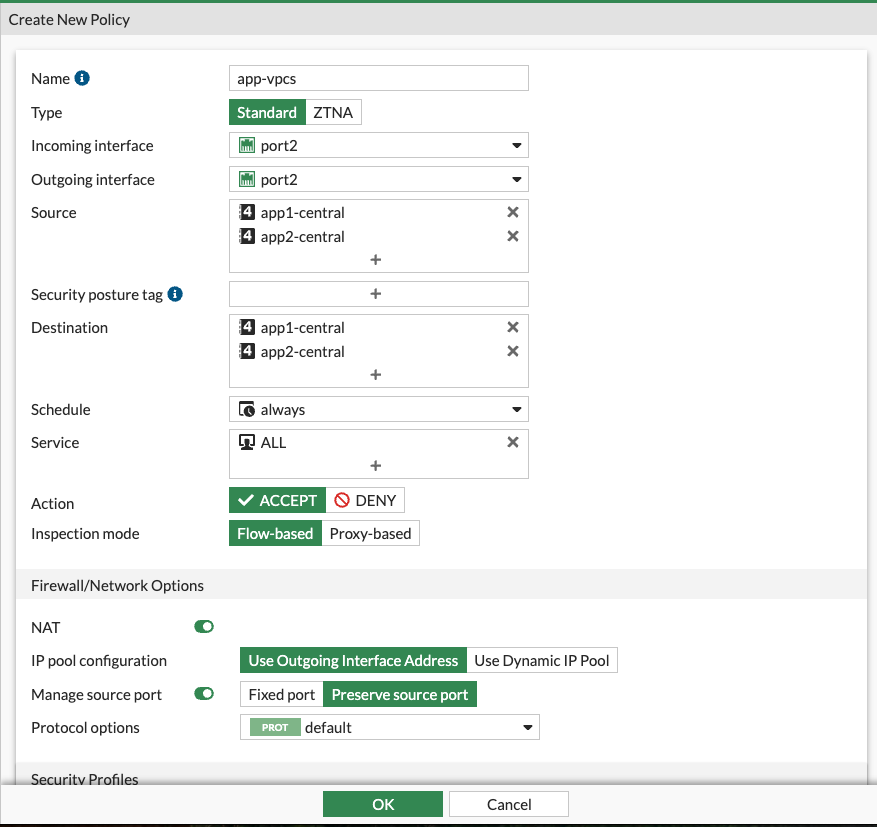
Create a policy allowing the traffic
- Navigate to Policy & Objects > Firewall Policy
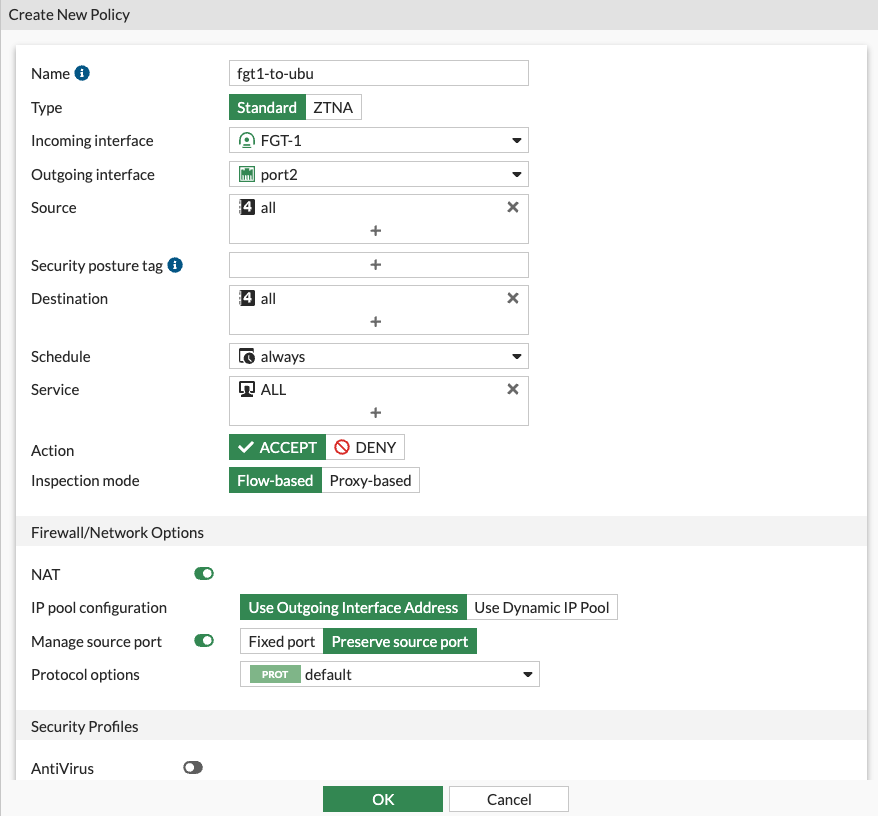
- Click Create new
- Configure the policy as below. Anything not visible is left as default value
Verify that ping is working from 1 to server 2
Attempt connectivity to remote site from server 1
- Start a ping from server 1 to server 2
ping 192.168.100.2This should fail.
- Start a ping from server 1 to server 2
Create a policy allowing the traffic on FortiGate1
- Navigate to Policy & Objects > Firewall Policy
- Click Create new
- Configure the policy as below. Anything not visible is left as default value
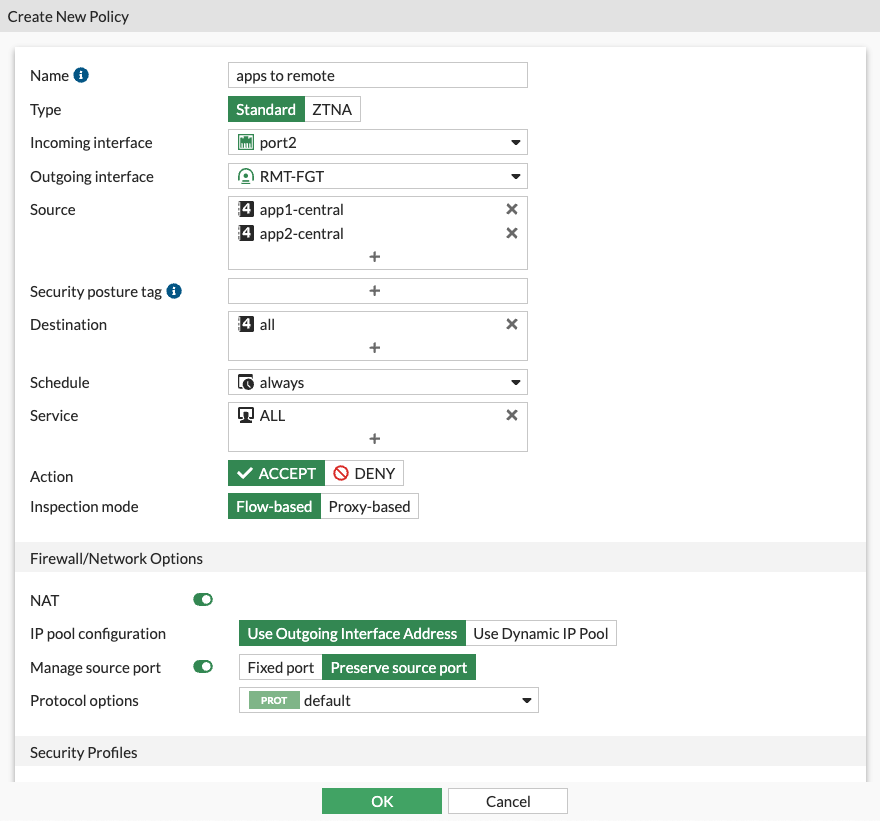
Create a policy allowing the traffic on Remote Fortigate
- Navigate to Policy & Objects > Firewall Policy
- Click Create new
- Configure the policy as below. Anything not visible is left as default value
Verify connectivity to remote site from server 1
- Start a ping from server 1 to server 2
ping 192.168.100.2This should now succeed.
- Start a ping from server 1 to server 2
Discussion
In this final hands-on task, we implemented the security policies that govern traffic flow. We started by demonstrating that, by design, all traffic between our application VPCs (East-West) and from our VPCs to the remote network (North-South) was blocked by the FortiGate. We then logged into the FortiGate appliances and created specific, granular firewall policies to explicitly permit this traffic. By successfully pinging between all locations after creating the policies, we have verified that our FortiGates are now acting as the central enforcement point for all traffic, securing our entire hybrid cloud network.
Chapter Summary
This chapter was dedicated to integrating our separate application VPCs into the secure transit hub we built.
- Task 1: Configure Application VPC Spokes: We initiated the connection by creating VPC spoke proposals from within the application project, pointing them towards our central NCC hub.
- Task 2: Accept Application Spokes: Acting as the network administrator, we switched back to the networking project and accepted the incoming spoke requests, officially activating the peering between the application VPCs and the hub.
- Task 3: Verify Routing: We manipulated the VPC routing tables, removing the direct internet gateways and confirming that the application VPCs learned the new default route from the FortiGates, forcing all traffic through them for inspection.
- Task 4: Verify Firewall: Finally, we configured the firewall policies on our FortiGates to allow the desired East-West and North-South traffic flows, completing the setup of our secure, centralized transit architecture.
Congratulations! You have completed the lab work! Now you can click on the below link to participate in a short Capture the Flag style game.
You will be prompted for a username. Pick something fun!
🎮 Interactive CTF Challenge
Launch the Capture The Flag challenge in a new window to test your skills!
Opens in a new window for the best experience